
Week in Overview(13 Feb-20 Feb) – 2024
4. Security Advisory Summary Report for CVE-2024-21412:
5. CVE-2024-21413 | Microsoft Outlook Remote Code Execution Vulnerability PoC:
Week in Overview(13 Feb-20 eb) – 20
The vulnerability, termed the #MonikerLink bug, is assigned CVE-2024-21413 with a CVSS score of 9.8. It allows for remote code execution and potential leakage of local NTLM information. The vulnerability enables attackers to bypass Office Protected View, extending its threat to other Office applications.
Usage: The PoC script facilitates testing responsibly with proper authorization. It utilizes SMTP authentication to send emails, bypassing SPF, DKIM, and DMARC checks, simulating real-world attack scenarios effectively.
Parameters:
Importance of SMTP Authentication: SMTP authentication is crucial for demonstrating how emails sent bypass common validation checks, mimicking sophisticated attacker techniques. This emphasizes the importance of comprehensive email security practices.
Demos:
Changelog:
Credits: Checkpoint conducted the research.
https://github.com/xaitax/CVE-2024-21413-Microsoft-Outlook-Remote-Code-Execution-Vulnerability
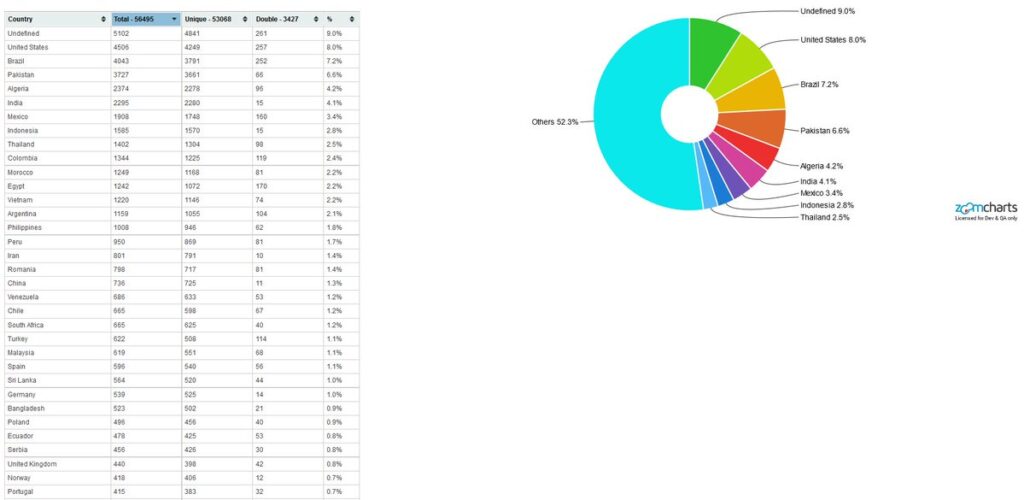
A comprehensive analysis of the STOP/DJVU ransomware campaign reveals significant insights into its reach and impact across various countries. The provided data, sourced from the attackers’ panel, sheds light on the scale of potential installations and highlights the geographical distribution of affected devices.
Campaign Overview:
Key Statistics:
Insights:

An open community event dedicated to security researchers leveraging Jupyter Notebooks within the InfoSec field provided a platform for knowledge-sharing and collaboration. Attendees participated virtually, exchanging insights, favorite notebooks, and practical applications of Jupyter Notebooks in various security domains. The event featured keynote speeches and presentations from industry experts, covering a wide range of topics related to security operations, threat hunting, data visualization, and more.
Keynote Address: The keynote speech titled “Barn Raising: Building a Community Around Jupyter Notebooks for DFIR, SecOps, and Detection Engineering Teams” by Ryan Marcotte Cobb highlighted the journey of growing a community of notebook users across different security teams. The keynote emphasized the adoption challenges, best practices, and the positive impacts of integrating Jupyter Notebooks into operational workflows.
Highlighted Talks: Several notable presentations showcased innovative approaches and practical use cases of Jupyter Notebooks in InfoSec:
Insights and Discussions: Throughout the event, speakers and participants engaged in discussions on various topics, including hacking proprietary protocols, threat hunting methodologies, and risk scoring models. Attendees gained insights into effective collaboration methods, threat intelligence analysis, and the practical applications of Jupyter Notebooks in security research and operations.

CVE-2024-21412 is a critical security vulnerability discovered in Microsoft Defender SmartScreen by the Trend Micro™ Zero Day Initiative™ (ZDI). This vulnerability was identified as part of a sophisticated zero-day attack chain orchestrated by the advanced persistent threat (APT) group known as Water Hydra (also referred to as DarkCasino). Notably, another unidentified group was also found exploiting the same vulnerability.
Patch Report: A special patch report was released by ZDI Senior Threat Researcher, Peter Girnus, who provided insights into the actively exploited nature of CVE-2024-21412 in the wild. The report delves into the specifics of the bug and the threat actors involved, offering crucial information for mitigation strategies.
Security Update: ZDI also issued a comprehensive security update regarding CVE-2024-21412, presenting insights from their zero-day initiative team. This update serves as a valuable resource for understanding the implications of the vulnerability and the necessary protective measures.
Impact: The exploitation of CVE-2024-21412 highlights the constant evolution of threat actors’ tactics in bypassing security measures. It was observed that the bypass of CVE-2023-36025, a previously patched SmartScreen vulnerability, ultimately led to the discovery and exploitation of CVE-2024-21412. This underscores the agility of threat actors in identifying new attack vectors even around patched software components.
A critical security vulnerability, identified as CVE-2023-45866, has been discovered in Android smartphones, enabling attackers to remotely lock out users or even wipe data through Bluetooth exploitation. This vulnerability poses a significant threat to user privacy and data security.
Vulnerability Details: The vulnerability allows attackers to remotely exploit Bluetooth functionality on Android smartphones without requiring pairing. By leveraging this vulnerability, attackers can inject keystrokes into the device, potentially leading to unauthorized access or control over the device’s functions.
Impact: The exploitation of CVE-2023-45866 poses serious risks to Android smartphone users. Attackers can remotely lock out users from their devices or, if the “Auto factory reset” feature is enabled, trigger a factory reset after 20 incorrect unlock attempts, resulting in the loss of all user data.
Mitigation: Android users are advised to take immediate action to mitigate the risks associated with this vulnerability:
Further Information: Additional details regarding the exploitation of this vulnerability can be found in the article provided by mobile-hacker.com: Exploiting 0-click Android Bluetooth Vulnerability to Inject Keystrokes Without Pairing
The administrative staff of the Lockbit ransomware group has confirmed the seizure of their websites. Lockbit, a notorious ransomware-as-a-service (RaaS) operation, has been associated with numerous high-profile cyberattacks, targeting organizations worldwide.
The seizure of Lockbit’s websites represents a significant blow to their infrastructure and operations. These websites likely served as crucial communication platforms for the ransomware group, facilitating negotiations with victims and providing information on their malicious activities.
While the exact circumstances surrounding the seizure remain undisclosed, it signals a potential disruption in Lockbit’s ability to conduct their illicit activities. This development aligns with global efforts to combat ransomware and disrupt cybercriminal operations.
Organizations impacted by Lockbit ransomware attacks may benefit from this development, as it could potentially hinder the group’s ability to execute attacks and demand ransom payments. However, it’s essential for affected organizations to remain vigilant and continue implementing robust cybersecurity measures to protect against evolving threats.
Law enforcement agencies, cybersecurity firms, and international partners are likely involved in the efforts to seize Lockbit’s infrastructure and hold its operators accountable. Such coordinated actions are critical in combating ransomware and dismantling cybercriminal networks.
As the situation develops, organizations should stay informed and collaborate with relevant authorities to mitigate the risks associated with ransomware attacks. Additionally, proactive measures such as data backups, network segmentation, and employee training remain essential components of a comprehensive cybersecurity strategy in defending against ransomware threats.