Week in Overview(17 Oct-24 Oct)
Recent cybersecurity analyses have unearthed a variety of threats and vulnerabilities across different platforms and applications. Among them, the RedLine Stealer emerges as a potent threat, exemplifying the need for robust cybersecurity measures. A notable vulnerability, CVE-2023-36745, in Microsoft Exchange Server further accentuates the critical necessity for timely patch management. Concurrently, the distribution of CobaltStrike beacons by Pikabot and the vulnerability CVE-2023-34051 in VMware Aria Operations for Logs underline the multiplicity of threat vectors organizations are facing.
The advent of qBit, a new threat being promoted on the RansomedForum by a user named “qBitSupp,” demonstrates the continuous evolution of malware. Meanwhile, a manual decoding of a complex .vbs script used for loading Cobalt Strike Shellcode elucidates the intricate methodologies employed by adversaries to obfuscate malicious code. The exploitation of Cisco IOS XE Software Web UI vulnerabilities delves deeper into the indicators of compromise, providing a glimpse into the nefarious activities surrounding Cisco devices.
In a case of deception, an incident of a victim’s token approval being mistakenly granted to a scammer through an “increaseAllowance” transaction was reported, showcasing the sophisticated social engineering tactics at play. On another front, a stealthy malicious Excel file managed to evade detection by a majority of antivirus solutions, accentuating the limitations of existing defensive measures against evolving malware strains.
Lastly, the unveiling of the IRATA Family Attack Vector outlines the organized and well-structured approach of modern-day threat actors. The wide array of threats and vulnerabilities discussed here underscores the critical importance of employing comprehensive cybersecurity strategies, staying updated with the latest threat intelligence, and fostering a culture of continuous learning and adaptation to stay ahead in the ever-evolving cybersecurity landscape.
VMWare Aria CVE-2023-34051
The vulnerability identified as CVE-2023-34051 exists in VMware Aria Operations for Logs and allows an unauthenticated malicious actor to bypass authentication mechanisms. This can lead to unauthorized file injection into the operating system of the impacted appliance, and subsequently, remote code execution.
Details:
The flaw stems from inadequate authentication checks in the application, permitting an attacker without authentic credentials to inject files into the operating system of the targeted appliance. Once the files are injected, the attacker can execute arbitrary code remotely on the affected system. The vulnerability is critical and has been assigned a score of 9.8 out of 10 on the CVSS scale1.
Proof of Concept (PoC):
A proof of concept demonstrating the exploitation of this vulnerability is available at https://github.com/horizon3ai/CVE-2023-34051.
Affected Versions:
The advisory did not specify the affected versions. It’s recommended to refer to the official VMware advisory for this information.
Mitigations:
It’s recommended to apply the necessary patches or updates provided by VMware to remediate this vulnerability. Additionally, adhering to best practices such as restricting network access, employing strong authentication mechanisms, and regularly monitoring system logs can help mitigate the risks associated with this vulnerability.
References:
Official VMware Advisory: Link (Note: The page could not be accessed for further details)
Technical Deep Dive: Horizon3.ai
Vulnerability Details: CVE Details, Tenable, Vulners

The new ransomware named qBit has been advertised on the Ransomed cybercrime forum by a threat actor using the pseudonym qBitSupp. This ransomware is currently in its Beta stage and is claimed to be written from scratch in Go, making it a fresh addition to the growing list of ransomware variants. The ransomware operates on a Ransomware as a Service (RaaS) model, offering many features to potential affiliates. The threat actor behind qBit advertises faster encryption speed, a low detection rate, and remarkable versatility with both Windows and Linux variants available. There’s also mention of the development of an ESXi version. qBitSupp aims to make qBit an affordable and accessible choice for newcomers to cybercrime, offering a 85/15 profit-sharing arrangement to affiliates1.
Moreover, qBitSupp has shared demo videos showcasing the potential harm this ransomware could inflict, adding to the growing concerns within the cybersecurity community regarding the proliferating nature of ransomware threats1.
Interestingly, the mention of qBitSupp comes a week after the coverage of qBit Stealer malware by @pcrisk, suggesting that both the Stealer and Ransomware variants are managed and developed by qBitSupp. Although there isn’t a direct correlation established between qBit Stealer and qBit ransomware, the common pseudonym qBitSupp used in the promotion of both malicious software suggests a possible link between the two.
The emergence of qBit and its advertisement on the Ransomed forum indicates a continuous evolution in the ransomware landscape, with threat actors developing and promoting new tools to commit cyber extortion. The RaaS model, which qBit operates under, continues to provide a platform for cyber criminals to easily deploy ransomware attacks, even for those with lesser technical skills, thus broadening the scope and scale of potential cyber threats.
The report on Pikabot distributing a CobaltStrike beacon through the URL hxxps://173.44.141.113/Create/v10.58/RTYZC2PY and the mentioned Command and Control servers (C2s) is as follows:
Pikabot has been identified to distribute CobaltStrike beacons, which are typically used for establishing persistent connections to infiltrated networks, allowing attackers to control compromised systems remotely. The distribution is carried out through malicious URLs, with the specified URL being one of the mediums. The technical analysis reveals that the malicious URL hxxps://173.44.141.113/Create/v10.58/RTYZC2PY is associated with a CobaltStrike beacon, indicating that it’s part of a malicious campaign orchestrated by Pikabot1.
Moreover, the listed Pikabot C2s (Command and Control servers) are essentially remote servers controlled by cyber attackers to manage malware or receive stolen data from compromised systems. The IP addresses and ports mentioned:
are part of this malicious network infrastructure utilized by Pikabot for its nefarious activities. Each of these IP addresses corresponds to a server that can potentially control malware, send commands, or exfiltrate data from victimized networks.
A deeper understanding of Pikabot’s mechanisms can be gleaned from technical analyses and deep dives into its cyber threat tactics, techniques, and procedures (TTPs)23. Additionally, the detection of Cobalt Strike beacons and the mitigation of associated threats are critical aspects that cybersecurity professionals are continually working on, as evidenced by resources and guides available online4.
While the specific Twitter post by Threatlabz was not directly accessible in the searched resources, the information gathered provides a substantial understanding of the cyber threat posed by Pikabot and its use of CobaltStrike beacons distributed through malicious URLs and controlled via the specified C2 servers.
A new malware threat identified as the IRATA family has emerged in the cybersecurity landscape, exhibiting an orchestrated attack pattern. This malicious software is distributed via certain payload URLs, with one such URL being highlighted by URLhaus: https://urlhaus.abuse.ch/url/2722813/. The payload linked to this URL was found to be hosted on Bazaar’s platform, showcasing a distinct malware sample with the hash: 6993d0ce074816c4f58761aa1579104aa5b95f1dbbf32ea70a67f904f6023fc6. The threat actors behind the IRATA family have operationalized this malware to execute malicious activities upon successful infiltration.
The IRATA malware communicates with its command and control servers (C2) to receive instructions and exfiltrate sensitive data. Two particular IoCs (Indicators of Compromise) linked with this C2 communication have been noted on ThreatFox: https://threatfox.abuse.ch/ioc/1191454/ and https://threatfox.abuse.ch/ioc/1191455/. Furthermore, a domain associated with this malware campaign, tedalat[.]hair, has been identified, which further unveils the infrastructure used by the attackers to perpetrate their malicious intents.
The infrastructure supporting this malware campaign is leveraged through services provided by Cloudflare (ISP) and the domain is registered with Namecheap (Registrar). These platforms inadvertently play a part in hosting and facilitating the malware’s network, underlining the significant role of third-party service providers in the malware distribution chain. The use of reputable service providers aids in masking the malicious activities, thereby increasing the chances of the malware evading detection and prolonging its operational lifespan.
The emergence of the IRATA family exemplifies the continuous evolution of malware threats. The modus operandi involving the use of legitimate service providers and a multi-tier communication infrastructure underscores the sophisticated techniques employed by modern-day threat actors. It’s imperative for organizations to remain vigilant, employ robust cybersecurity measures, and collaborate with external threat intelligence platforms to stay ahead of such evolving threats. The insights provided by platforms like URLhaus, Bazaar, and ThreatFox are invaluable in understanding the threat landscape and preparing defenses against such nuanced malware campaigns.
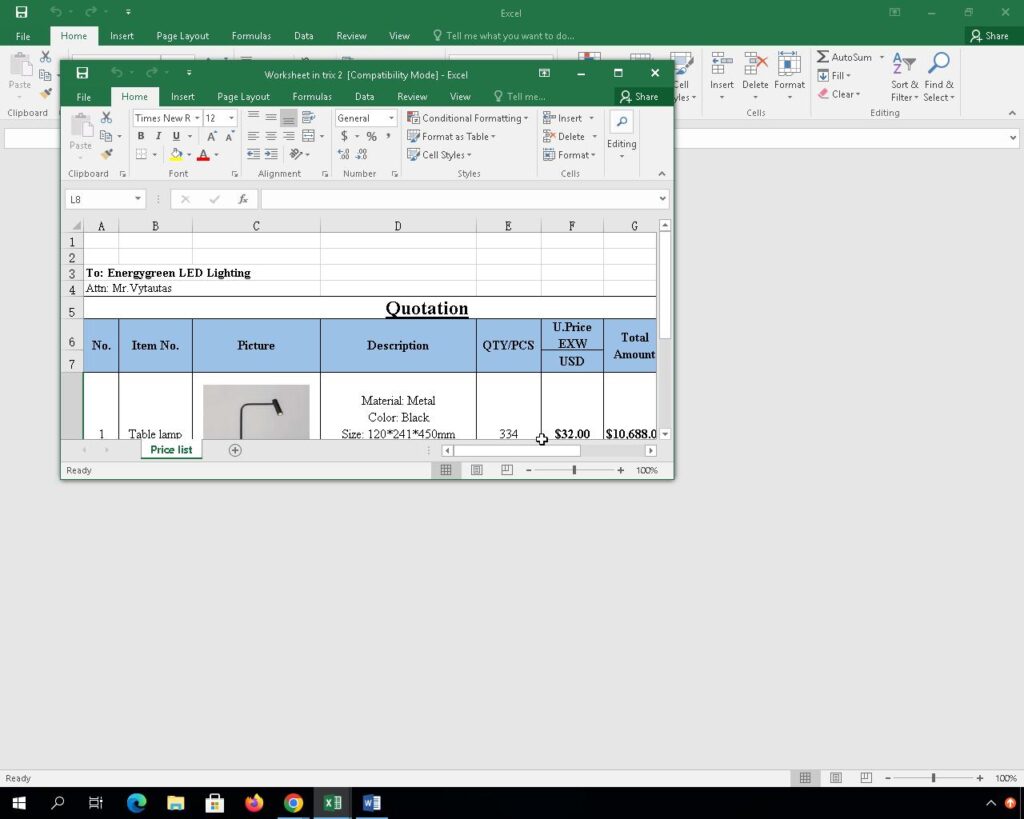
In a recent security incident, a malicious Excel file has managed to slip past the detection mechanisms of a majority of antivirus solutions, signaling a potential rise in the sophistication of malware delivery techniques. The malicious file, named “solicitud de cotización.xla”, exhibited a complex multi-step infection flow that involved multiple Microsoft applications and processes to ultimately execute malicious code on the victim’s system. With a low detection rate of 9 out of 62 on VirusTotal (VT), this file poses a significant threat to users and networks unprepared for such advanced evasion tactics.
The infection chain commenced with the malicious Excel file, which upon being opened, triggered a cascade of actions involving Word, the Equation Editor (eqnedt32.exe), Windows Script Host (wscript.exe), and subsequently multiple instances of PowerShell, ultimately leading to the execution of regasm.exe. This elaborate sequence of actions serves as a means to evade detection, by leveraging legitimate processes to carry out malicious activities stealthily. The multi-stage attack vector not only demonstrates the attacker’s in-depth understanding of Microsoft’s suite of applications but also their ability to manipulate these interconnected processes to fulfill malicious intents.
The MD5 hash value of the malicious file is identified as 2ca17c363987979bbbee80b08f3f97be, and it has been reported to communicate with a malicious IP address 185.254.37.174, which is suspected to be a command and control server (C2) for the malware. The detailed analysis provided by DOCGuard in their report highlights the intricacies of the attack and the stealthy nature of the malicious Excel file. The evasion of nearly all antivirus solutions is alarming and underscores the necessity for advanced detection mechanisms capable of identifying and mitigating multi-stage, obfuscated attack vectors.
As malicious actors continue to refine their evasion techniques and employ multi-stage attack vectors, the onus falls on security solutions to evolve and adapt to these emerging threats. This incident emphasizes the importance of employing a multi-layered security approach, encompassing not just antivirus solutions but also employing behavior analysis, heuristic detection, and robust incident response procedures to detect and mitigate such sophisticated threats. Additionally, educating end-users on the risks associated with opening unsolicited attachments and promoting a culture of cybersecurity awareness can significantly contribute to minimizing the risk posed by such stealthy malicious files.
A complex .vbs script has been identified which is designed to load Cobalt Strike shellcode into memory. The script utilizes heavy text-based obfuscation which can be decoded manually using CyberChef and Regex. Post-obfuscation, some “malformed” shellcode is identified, which is then manually fixed before being emulated with the SpeakEasy emulator.
Methods:
Results: Upon successful decoding and emulation, the script is revealed to load a Cobalt Strike shellcode into memory which acts as an HTTP-based downloader from a specified IP address. The manual decoding process unveiled the underlying malicious activity hidden behind multiple layers of obfuscation in the .vbs script.
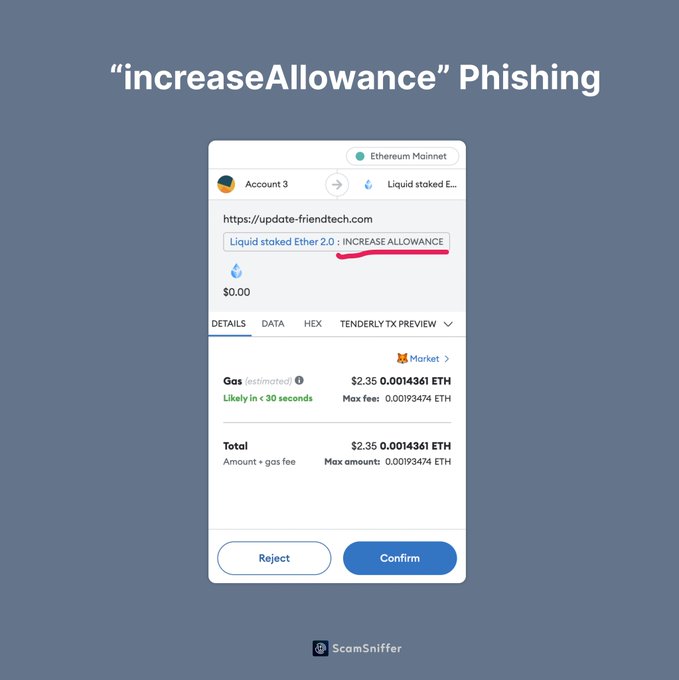
In the ever-evolving space of digital transactions, security has become the centerpiece of concerns, especially with the increasing sophistication of scams. A particularly concerning scenario unfolded recently when a victim mistakenly approved a token allowance to a scammer by signing an “increaseAllowance” transaction. The “increaseAllowance” function is a part of the ERC-20 token standard in the Ethereum blockchain, which allows a specified address to spend tokens on behalf of the owner up to a certain amount. Unwittingly, the victim authorized the scammer to access and manage their tokens by executing this function, which set off a series of unauthorized transactions.
This unfortunate event underscores the critical importance of understanding the implications of the transactions one is signing on the blockchain. The deceptive request for an “increaseAllowance” transaction might have appeared benign or routine to the victim, masking the malicious intent of the scammer. Furthermore, the scammer could have employed social engineering techniques to gain the trust of the victim or exploit their lack of understanding regarding the functionalities associated with such transactions. In essence, the scammer’s ability to mislead the victim into signing the transaction accentuates the emerging sophisticated tactics employed by malicious actors in the blockchain space.
The aftermath of this incident holds substantial financial ramifications for the victim, alongside a breach of their digital trust. Once the scammer received the misguided approval, they gained the ability to initiate transactions with the victim’s tokens up to the approved limit. Without immediate corrective measures, such as revoking the allowance using the “decreaseAllowance” function or transferring the tokens to a secure address, the victim stood to lose a significant portion, if not all, of their digital assets. The scenario sheds light on the potentially catastrophic impacts that a single misguided transaction approval could entail in the blockchain ecosystem.
Moving forward, this incident serves as a stark reminder for individuals and entities interacting with blockchain technologies to exercise utmost caution. It’s imperative to have a solid understanding of the transactions one is engaging in, especially when authorizing allowances for token transactions. Employing additional security measures such as multi-signature approvals, utilizing secure and reputable platforms, and seeking advice from knowledgeable sources before executing sensitive transactions can act as deterrents against falling victim to such scams. The blockchain community must also ramp up efforts in educating users on the security aspects and potential risks associated with token transactions to foster a safer digital transaction environment.
The report on CVE-2023-36745 sheds light on a vulnerability in Microsoft Exchange Server, identified as a variant of CVE-2022-41082. This vulnerability surfaced after the release of a report by Trend Micro Zero Day Initiative regarding remote code execution in Exchange PowerShell Backend. It has a lineage of deserialization bypass vulnerabilities, specifically in the PowerShell endpoint of Microsoft Exchange Server, like CVE-2023-21707 and CVE-2023-32031 demonstrated at Hexacon 2023 by chudyPB.
The crux of CVE-2023-36745 lies in bypassing via the Microsoft.Exchange.DxStore.Common.DxSerializationUtil.SharedTypeResolver class, wherein its single-argument constructor calls Assembly.LoadFrom to load assemblies.
The Microsoft.Exchange.Diagnostics.ChainedSerializationBinder class has a LoadType method which loads classes from the assemblies in the current application context.
The exploitation process involves leveraging deserialization type conversion to invoke the single-argument constructor of Microsoft.Exchange.DxStore.Common.DxSerializationUtil.SharedTypeResolver class to load a custom assembly introducing malicious classes. Thereafter, utilizing deserialization type conversion to invoke the single-argument constructor of the malicious class enables Remote Code Execution (RCE).
However, there’s a caveat since the .NET Framework 4 and onwards has disabled the ability to execute code in assemblies loaded from remote locations by default, which could lead to a FileLoadException being thrown when calling the LoadFrom method. A workaround is mentioned using SMB share to load assemblies from other machines.
In order to bypass the whitelist of allowed classes for deserialization, the exploitation process requires to be paired with CVE-2023-21529 to utilize the generic class Microsoft.Exchange.Data.MultiValuedProperty.
The Proof of Concept (PoC) section provides XML snippets showing how to construct malicious objects to exploit this vulnerability, by setting the TargetTypeForDeserialization to a malicious value and providing an SMB path to load assemblies from or executing a malicious command like calc.exe.
This report represents a deep technical analysis of the CVE-2023-36745 vulnerability, providing insights into how it can be exploited to achieve remote code execution on a target Microsoft Exchange Server, by bypassing deserialization protections.
You can read the full report here.
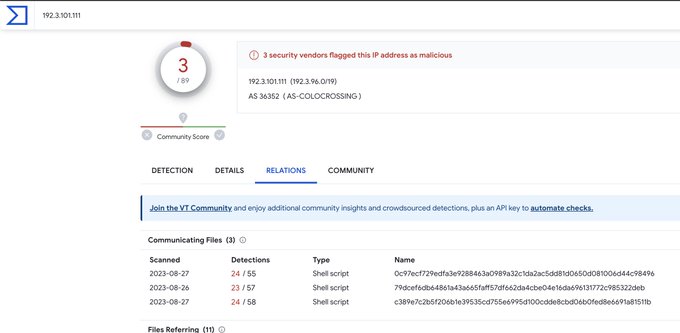
Cisco IOS XE Software Web UI has been identified to have vulnerabilities that are actively being exploited. A deeper look into the Indicators of Compromise (IoCs) provided shows a pattern of exploitation originating from specific IP addresses which share a unique HTML page. This report explores the identified IoCs and advises on the necessary vigilance to mitigate the risks associated with this exploitation.
Methods:
Identified IoCs: Below are the IP addresses identified to be sharing an identical unique HTML page, which is a significant indicator of the ongoing exploitation:
RedLine Stealer is a notorious malware that operates by pilfering sensitive data from infected computers. It is typically classified as an “infostealer” due to its data theft capabilities. The malware is often utilized by cyber criminals for reconnaissance and initial access to networks. RedLine Stealer extracts a variety of data, including login credentials, session cookies, cryptocurrency keys, and system details. A notable breach attributable to RedLine Stealer is the 2023 hack of the Linus Tech Tips YouTube channel. In the face of its growing infamy, devising measures to catch and curb RedLine Stealer’s activities is imperative.
Data Exfiltration Protocol: RedLine Stealer’s data exfiltration mechanism initiates with communication to a hard-coded Command-and-Control (C2) server using a unique cleartext protocol. This protocol outlines a structured format for data transmission, including connection initiation, call classification, authorization, and data sending. Each communication is tagged with specific ‘Id numbers’, providing a well-organized structure for data exfiltration. A specific pattern observed is the use of a string “http://tempuri.org/” before an entity’s classification, a remnant of improperly implemented ASP.Net web services. This pattern can be employed to create network signatures for detecting RedLine Stealer data exfiltration.
Command-and-Control Meta-Analysis: RedLine Stealer’s C2 infrastructure presents a blend of domain names and hard-coded IP addresses for establishing connections. Notably, about two-thirds of the domain names are registered under *.xyz and *.top top-level domains, often leveraging Dynamic DNS (DDNS) services. However, a majority of RedLine payloads, around 80%, directly connect to hard-coded IP addresses, which are often hosted on bulletproof hosting providers or compromised infrastructure.
Catching the RedLine: Efficient strategies to mitigate the RedLine Stealer include: