
Week in Overview(19 Sep-26 Sep)
1. Malware Distribution from zzlsteel[.]cc and Associated C2 Domains
2. “Passport and KYC Documents[.]zip” Malware
3. Stealth Falcon Preying on Middle Eastern Skies with DeadGlypH
4. T-Mobile Employee PII Breach and Sony Data Breach
5. CVE-2023-41892 Craft CMS Remote Code Execution Vulnerability
6. From ScreenConnect to Hive Ransomware in 61 Hours
7. Critical Authentication Bypass in JetBrains TeamCity CI/CD Servers (CVE-2023-42793)
8. Critical Vulnerability in Juniper Devices
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
A significant security vulnerability, CVE-2023-41892, has been identified in Craft CMS, a widely used content management system. This vulnerability allows for Remote Code Execution (RCE), enabling attackers to execute arbitrary code remotely and potentially compromise the security and integrity of the affected application. The Proof-of-Concept (POC) provided demonstrates the exploitation process, underscoring the urgency for immediate mitigation actions to prevent unauthorized access and control over the vulnerable systems.
Technical Details
The POC outlines the exploitation process, beginning with the use of specific headers and data payloads sent via HTTP requests to the vulnerable Craft CMS server. The exploit involves writing a malicious payload to a temporary file on the server, triggering Imagick to write a shell, and then executing arbitrary commands on the server. The exploit uses the conditions/render action and manipulates the configObject[class] parameter to execute the arbitrary code, leading to the compromise of the server. The POC code provided is executed with Python, and it automates the entire exploitation process, making it easy for an attacker to compromise a vulnerable Craft CMS server.
Mitigation and Recommendations
To mitigate the risks associated with CVE-2023-41892, it is crucial for organizations using Craft CMS to update their systems to a version that patches this vulnerability. If an update is not immediately available, organizations should consider disabling the affected functionality or increasing monitoring and access controls to detect and prevent exploitation attempts. It is also essential to conduct a thorough security assessment to identify and remediate any unauthorized changes or access to the affected systems. Organizations are advised to follow best practices for security hygiene, including regular patch management, monitoring, and employee awareness training to prevent exploitation of vulnerabilities.
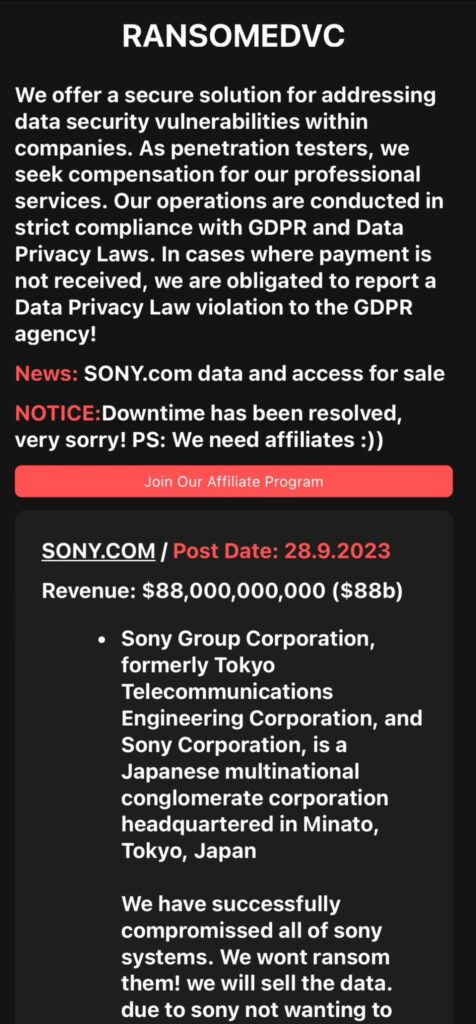
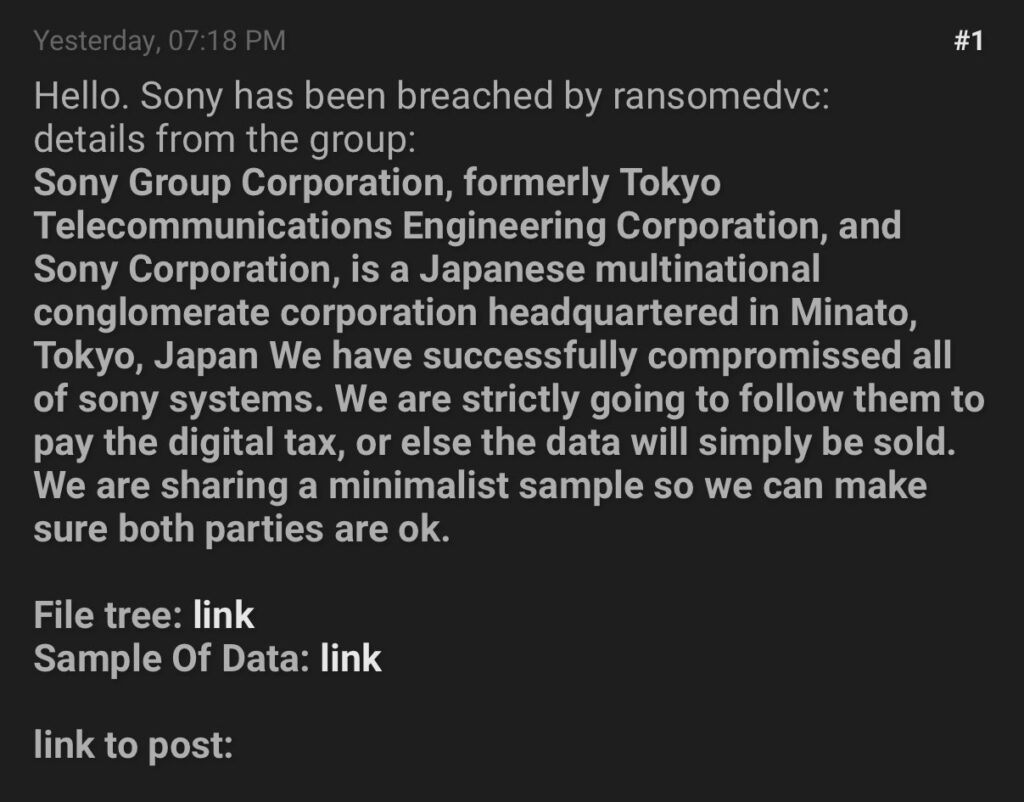
A significant data breach has been reported involving the leak of T-Mobile employee Personally Identifiable Information (PII), marking the second such incident this year. The breach, which occurred in April 2023, was not disclosed until September 21, 2023. The individuals allegedly responsible for the breach and the subsequent leak are known as “Doubl” and “Emo,” respectively. The leaked information, now publicly available on BreachForum, is being disseminated widely across various platforms, including Telegram and Discord. This incident underscores the critical importance of robust data security measures and timely breach disclosure to protect sensitive employee information.
Detailed Information
The breach was executed by “Doubl” and the leaked information was disseminated by “Emo.” The exact details of the breach methodology are not known, but the delay in the leak suggests a possible period of data exploitation or sale in underground markets before public release. The leaked data is extensive, encompassing multiple databases, and the exact extent of the information leaked is still being ascertained. Preliminary reports suggest that the data is substantial and sensitive, warranting immediate attention and mitigation efforts to protect the affected individuals.
In light of the T-Mobile breach, organizations must prioritize the security of both customer and employee data. The alleged data breach at Sony further emphasizes the growing cybersecurity threats facing corporations. While details about the Sony breach are still emerging, it is crucial for Sony to conduct a swift and thorough investigation, notify affected parties, and take appropriate measures to mitigate the impact. Continuous monitoring, robust cybersecurity infrastructure, and adherence to best security practices are paramount in protecting organizational and personal data from breaches and leaks.
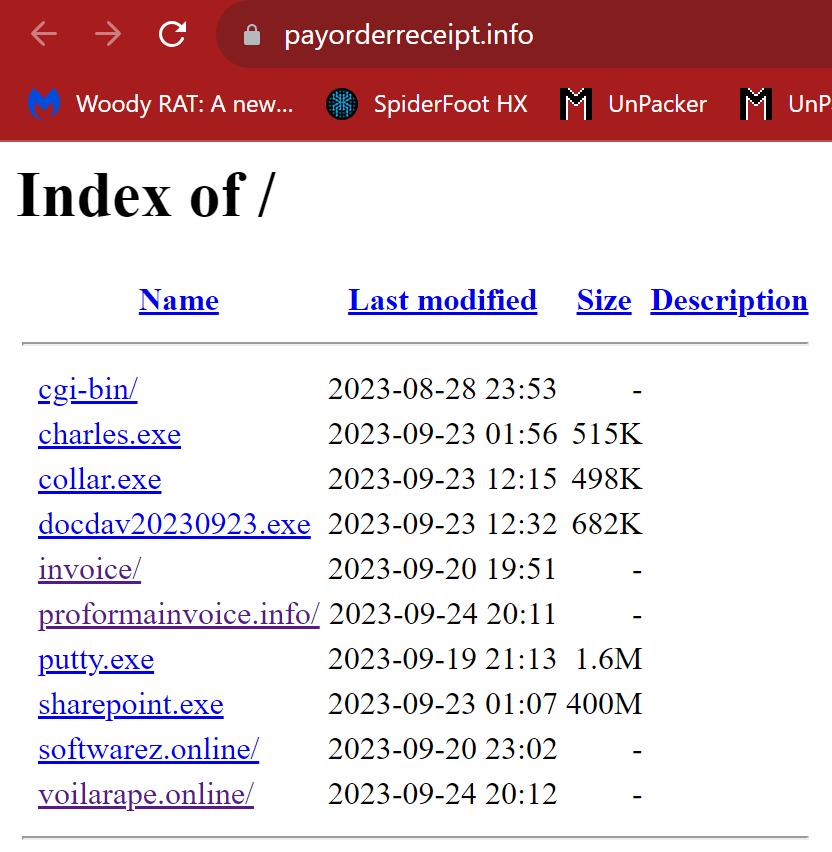
A malicious infrastructure has been identified, hosting XWorm and SnakeKeylogger malware. The staging server and command and control servers (C2s) associated with XWorm, as well as an FTP server associated with SnakeKeylogger, have been spotted. The pattern aligns with the known cybercriminal group, DDGroup. Organizations are advised to take immediate action to block access to the identified malicious domains and servers and scan their networks for indicators of compromise.
Details of the Malware Infrastructure
Impact
YARA Rule for Detection
Below is a basic YARA rule for detecting the presence of XWorm and SnakeKeylogger. This rule should be customized and enhanced for more effective detection.
rule XWorm_SnakeKeylogger_Detection {
meta:
description = “YARA Rule for XWorm and SnakeKeylogger Detection”
author = “Your Organization”
date = “2023-09-26”
strings:
$xworm1 = “xwormfresh[.]duckdns[.]org:7002”
$xworm2 = “homesafe1000[.]duckdns[.]org:7000”
$snakekeylogger = “ftp.product-secured[.]com”
condition:
any of them
}
This advisory report provides a comprehensive technical analysis of a malicious file named “Passport and KYC Documents[.]zip,” identified by its hash on VirusTotal. The malware follows a sophisticated execution chain: LNK -> PowerShell -> Dropbox -> Delphi RunPE -> UPX -> unknown C++ malware, and is suspected to communicate with a Command and Control (C2) server at macores[.]com (192.71.249[.]198). The malware employs various evasion and obfuscation techniques, making detection and analysis challenging.
Technical Details
Malware Execution Chain:
C2 Communication:
Evasion Techniques:
The report from WeLiveSecurity provides an in-depth analysis of the cyber-espionage group, Stealth Falcon, and their latest campaign utilizing the DeadGlypH malware to target entities in the Middle East. Stealth Falcon, known for its sophisticated cyber-espionage tactics, has been actively deploying DeadGlypH, a custom backdoor, to compromise systems and exfiltrate sensitive information. The group’s operations are characterized by meticulous planning, the use of previously unseen malware, and a clear focus on specific targets, making their activities a significant concern for cybersecurity in the Middle East.
Technical Details of DeadGlypH
Malware Delivery and Installation:
Malware Capabilities:
Evasion Techniques:
Stealth Falcon Tactics, Techniques, and Procedures (TTPs)
Stealth Falcon’s operations demonstrate a high level of sophistication and coordination:
The dashboard on Dune, titled “sha-zhu-pan” by Tayvano, highlights a critical and growing issue in the cryptocurrency space: the proliferation of scams that are effectively onboarding more individuals to crypto than legitimate organizations, only to defraud them of their investments. The scammers operate by building trust with individuals over extended periods, sometimes months or even years, guiding them through the process of investing in cryptocurrency, and then exploiting this trust to steal their funds.
The Scam Operation
The scammers initiate contact with potential victims and gradually build a relationship of trust. Users who reached out for help in April 2023 reported that they had been in contact with the scammers since October 2022. This long con allows the scammers to guide the victims through the process of purchasing and investing in cryptocurrency, all the while setting the stage for the eventual fraud. The victims, believing they are making legitimate investments, willingly and happily follow the instructions of the scammers, visiting fraudulent websites, approving interactions, and sending transactions, unaware of the deception.
This advisory report outlines the critical information regarding a malware distribution site, zzlsteel[.]cc, which is notably serving the OriginBotnet and XKeyBot malware. These malicious software variants are known to communicate with a Command and Control (C2) server located at nitrosoftwares[.]shop. Both domains, along with other C2 servers, are registered with Namecheap, highlighting a potential security concern related to the domain registration service. Immediate attention and action are required to mitigate the risks associated with this malware distribution and control infrastructure.
Malware Distribution:
Command and Control Servers:
Malware Functionality:
A critical authentication bypass vulnerability, CVE-2023-42793, has been disclosed in JetBrains TeamCity CI/CD servers. This vulnerability allows an unauthenticated attacker with HTTP(S) access to perform a remote code execution attack and gain administrative control of the server, posing a significant threat as a potential supply chain attack vector. Immediate action is required to mitigate this vulnerability.
Details of the Vulnerability
Exploitation
As of September 25, 2023, there is no known in-the-wild exploitation or public exploit code available for CVE-2023-42793. However, the potential impact of successful exploitation is significant, warranting urgent attention and mitigation.
Affected Versions
CVE-2023-42793 affects all on-prem versions of JetBrains TeamCity prior to 2023.05.4. TeamCity Cloud is not affected.
Mitigation Guidance
A critical unauthenticated remote code execution (RCE) vulnerability has been discovered in Juniper SRX firewalls and EX switches, affecting an estimated 12,000 devices. Despite initially being rated as medium severity, the vulnerability (CVE-2023-36845) has been proven to allow remote code execution without authentication, posing a significant threat to affected systems. Immediate action is required to mitigate the risk.
Details of the Vulnerability
Exploitation
Researchers have released proof-of-concept (PoC) exploits demonstrating the vulnerability’s exploitability. The exploit allows attackers to remotely execute arbitrary code without authentication by manipulating environment variables and utilizing PHP’s features.
Affected Versions
The vulnerability impacts the following versions of Junos OS on EX Series and SRX Series:
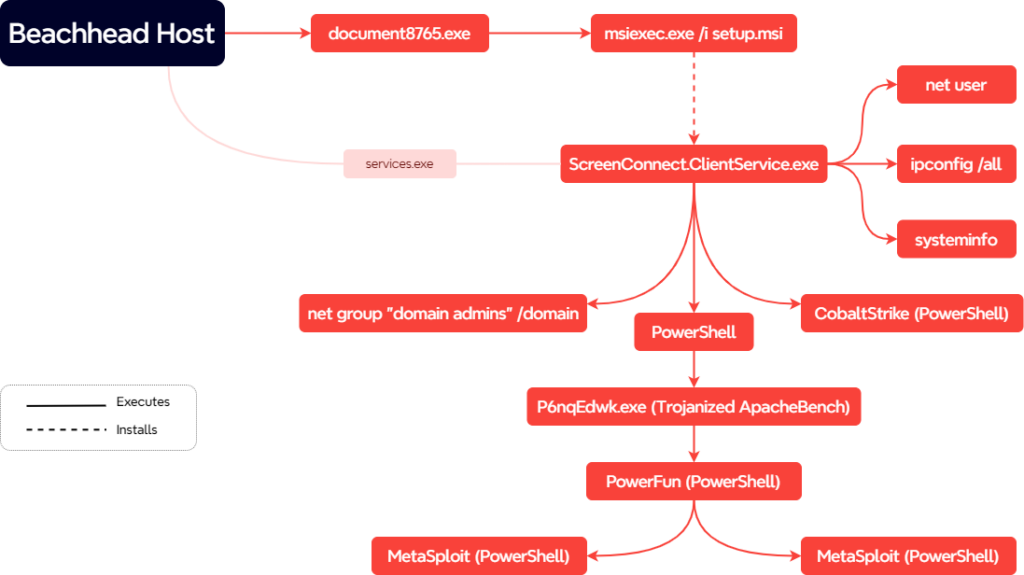
The detailed report from The DFIR Report, published on September 25, 2023, offers an in-depth examination of a cyberattack that culminated in the deployment of Hive Ransomware within a mere 61 hours. The attackers exploited ScreenConnect, a widely used remote access tool, to infiltrate the victim’s network. This case study highlights the speed and efficiency with which cybercriminals can operate, leveraging legitimate tools to bypass security measures and execute their attack swiftly and stealthily.
Attack Progression
Upon gaining access via ScreenConnect, the attackers quickly escalated their privileges, demonstrating a comprehensive understanding of the network’s vulnerabilities. The use of Cobalt Strike, a legitimate penetration testing tool, further aided their malicious activities, allowing them to traverse the network undetected. The attackers’ adeptness in utilizing these tools underscores the challenge organizations face in differentiating between legitimate and malicious activities within their networks. The rapid lateral movement and privilege escalation led to the successful deployment of Hive Ransomware, leaving the victim with encrypted files and a ransom demand.
Tactics and Techniques
The attackers exhibited a range of sophisticated tactics and techniques throughout the attack. Their initial exploitation of ScreenConnect, a tool typically used for legitimate remote access, highlights the trend of cybercriminals leveraging legitimate tools to avoid detection. The subsequent use of Cobalt Strike allowed them to further navigate the network, likely exploiting unpatched vulnerabilities and weak security configurations to escalate privileges and move laterally. The final deployment of Hive Ransomware encrypted the victim’s files, rendering them inaccessible and culminating in a ransom demand for decryption keys.