
Week in Overview(3 Oct-10 Oct)
Zero-Day Privilege Escalation in Confluence Server and Data Center
CVE: CVE-2023-22515
This zero-day vulnerability affects on-premises instances of Confluence Server and Confluence Data Center. Originally identified as a privilege escalation flaw, it was later classified as a broken access control issue. Attackers can exploit this vulnerability to create unauthorized Confluence administrator accounts and access instances remotely. The vulnerability is fully unauthenticated and trivially exploitable, posing a severe risk to systems exposed to the public internet.
Darkgate MalSpam Advisory Report – Italy 🇮🇹
The Darkgate MalSpam campaign targeted Italian entities. The attack involved malicious emails with stolen conversation content, which contained links leading to zip files. Upon extraction, these files contained malware, ultimately leading to the delivery of malicious executable files. Vigilance and email security measures are crucial to thwarting such campaigns.
Recreation of SharePoint PoC for CVE-2023-29357
CVE: CVE-2023-29357
This technical summary pertains to a proof-of-concept (PoC) recreation of the SharePoint vulnerability tracked as CVE-2023-29357. The PoC is coded in C# and built with .NET Version 4.7.2 in Visual Studio 2017. It is designed to exploit the vulnerability via a command-line interface, using a specified URL. The PoC allows threat actors to remotely execute commands on vulnerable systems.
‘Predator Files’ Spyware Scandal – Brazen Targeting of Civil Society and Officials
This report highlights the “Predator Files” spyware scandal, which exposed invasive espionage activities targeting civil society, journalists, politicians, and officials globally. The spyware, known as Predator, was used in brazen attacks facilitated by the Intellexa alliance. Predator is highly invasive, providing attackers unfettered access to compromised devices, including microphones, cameras, and sensitive data. The campaign targeted high-profile individuals, including UN officials, members of parliament, and academics.
Threat Posed by Hacker Groups Targeting Israel and US Infrastructure
This section addresses the threat posed by hacker groups targeting the infrastructure of Israel and the United States. Multiple hacker groups have expressed intentions to target government websites and institutions. While the authenticity of some claims remains uncertain, the attacks underscore the persistent cybersecurity challenges faced by governments and organizations. Proactive security measures, incident response planning, and threat intelligence are essential to safeguard against potential cyberattacks.
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
Confluence CVE-2023-22515
On October 4, 2023, Atlassian released a security advisory regarding CVE-2023-22515, a critical vulnerability affecting on-premises instances of Confluence Server and Confluence Data Center. This security flaw was initially identified as a privilege escalation vulnerability but later reclassified as a broken access control issue. The precise root cause of the vulnerability remains undisclosed, and Atlassian has not provided specific details about its location within Confluence implementations. However, indications point to the /setup/* endpoints as potential areas of concern.
The advisory reports that external attackers may have exploited this vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and gain access to these instances.
Research conducted by Rapid7’s team has confirmed that the vulnerability is fully unauthenticated and easily exploitable. It appears that multiple avenues of attack are possible, extending beyond the creation of new administrator accounts. Rapid7’s analysis revealed the use of the /server-info.action endpoint as a possible attack vector, which was not mentioned in Atlassian’s initial indicator of compromise (IOCs).
Atlassian has urgently recommended that on-premises Confluence Server and Data Center customers either update to a fixed version immediately or implement mitigations. The advisory emphasizes that instances exposed to the public internet are particularly susceptible, as this vulnerability can be exploited anonymously.
Affected Products
The following versions of Confluence Server and Data Center are confirmed to be affected by CVE-2023-22515:
Versions prior to 8.0.0 are not vulnerable to this issue. Additionally, Atlassian Cloud sites and Confluence sites accessed via an atlassian.net domain are not affected.
Fixed Versions
To address this critical vulnerability, Atlassian has released the following fixed versions:
Customers are strongly encouraged to update their Confluence Server and Data Center instances to one of these versions promptly.
Cobalt Strike is a legitimate security tool developed by Raphael Mudge for penetration testing, red teaming, and security assessment purposes. It is designed to assist cybersecurity professionals in identifying vulnerabilities within an organization’s network and infrastructure. However, Cobalt Strike has also gained notoriety for being abused by threat actors for malicious activities.
The unauthorized distribution of Cobalt Strike 4.9 has several significant security implications:
ITo mitigate the risks associated with the leaked Cobalt Strike 4.9, organizations and security professionals are advised to take the following measures:
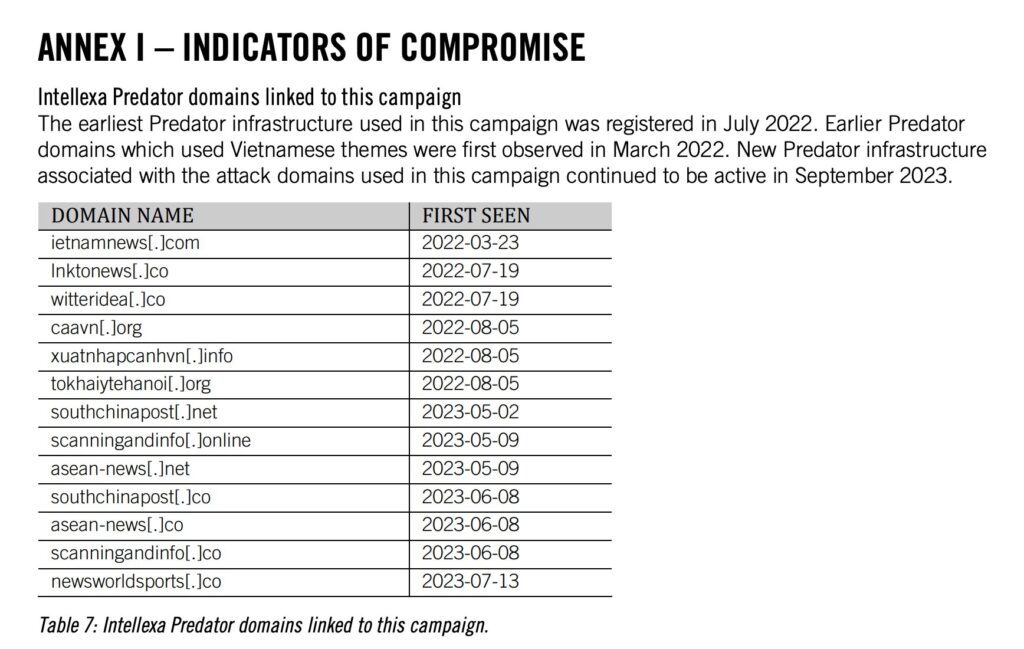
Predator Spyware Campaign
Between February and June 2023, at least 50 accounts belonging to 27 individuals and 23 institutions were publicly targeted via social media platforms, particularly X (formerly Twitter) and Facebook. The cyber-surveillance weapon used for these attacks was the highly invasive Predator spyware, developed and sold by the Intellexa alliance. This alliance, which has presented itself as “EU-based and regulated,” is a conglomerate of companies that develop and distribute surveillance products, including the Predator spyware.
Invasive Nature of Predator
Predator is categorized as highly invasive spyware, capable of unrestricted access to a compromised device’s microphone, camera, and all data, including contacts, messages, photos, and videos. Once installed, the user remains unaware of its presence. Presently, this type of spyware cannot be independently audited or limited in its functionality, making it exceedingly challenging to control its misuse.
High-Profile Targets
Among the prominent figures targeted by the Predator spyware campaign are United Nations (UN) officials, a US Senator and Congressman, and the Presidents of the European Parliament and Taiwan. Numerous officials, academics, and institutions have also been subjected to these attacks.
Comments from Amnesty International
Agnes Callamard, Secretary General at Amnesty International, emphasized the grave implications of these attacks, stating, “The targets this time around are journalists in exile, public figures, and intergovernmental officials. But let’s make no mistake: the victims are all of us, our societies, good governance, and everyone’s human rights.”
Regarding the Intellexa alliance’s role, she added, “The Intellexa alliance, European-based developers of Predator and other surveillance products, have done nothing to limit who is able to use this spyware and for what purpose. In the wake of this latest scandal, surely the only effective response is for states to impose an immediate worldwide ban on highly invasive spyware.”
Targeting Details
The investigation found that an attacker-controlled X (formerly Twitter) account, ‘@Joseph_Gordon16,’ shared malicious links designed to infect targets with the Predator spyware. One notable target was Berlin-based journalist Khoa Lê Trung, who faced threats due to his reporting in Vietnam. This attack is significant as it occurred within the EU, where member states are obligated to control the sale and transfer of surveillance technologies.
International Implications
The investigation revealed that the Predator spyware and other Intellexa alliance products were deployed in at least 25 countries across Europe, Asia, the Middle East, and Africa. These tools have been used to undermine human rights, press freedom, and social movements globally. Amnesty International calls for the immediate revocation of marketing and export licenses issued to the Intellexa alliance by states, including France, Germany, Greece, Ireland, Czech Republic, Cyprus, Hungary, Switzerland, Israel, North Macedonia, and the UAE.
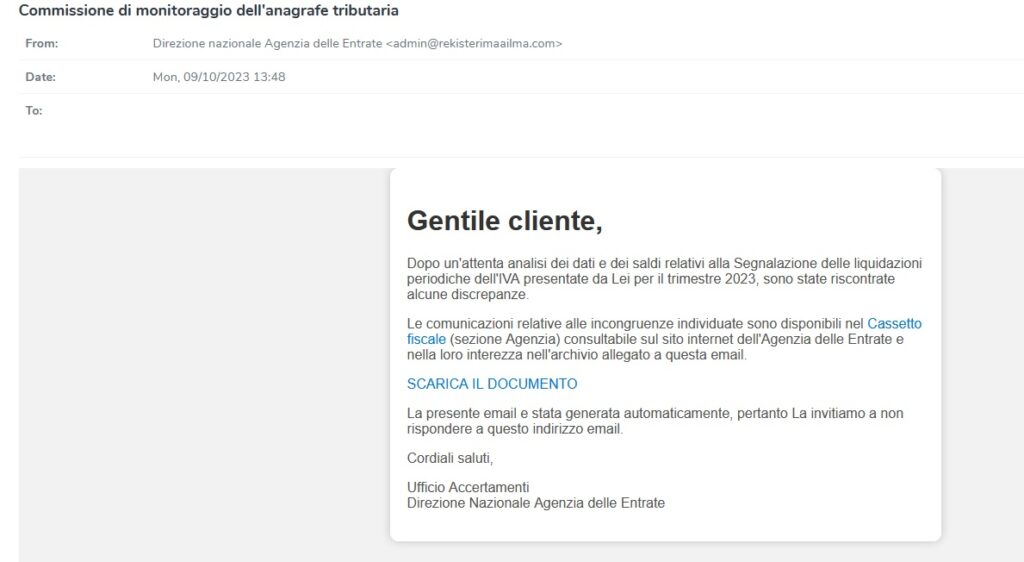
https://twitter.com/JAMESWT_MHT/status/1711357394733707592
This advisory report highlights a significant threat involving the Ursnif malware campaign targeting an entity referred to as “Commissione di monitoraggio dell’anagrafe tributaria.” The Ursnif campaign, tagged with #Ursnif and #agenziaentrate, is a malicious campaign that utilizes various attack vectors to compromise systems and deliver a payload. The report provides information on the attack chain, indicators of compromise (IOCs), and recommended mitigation measures.
Attack Chain
The Ursnif malware campaign follows a multi-stage attack chain as outlined below:
Indicators of Compromise (IOCs)
The following IOCs are associated with this Ursnif campaign:
Attack Staging Domain
Attack Chain
The Darkgate malspam campaign follows a multi-stage attack chain, as outlined below:
Indicators of Compromise (IOCs)
The following indicators of compromise (IOCs) have been associated with the Darkgate malspam campaign:
The KONNI Advanced Persistent Threat (APT) group, believed to originate from North Korea, has a significant presence in the world of cyber espionage. With a focus on targeted attacks, primarily against South Korea, KONNI has gained notoriety for its sophisticated and adaptable tactics. This report provides an overview of the group’s operations, tactics, and objectives, highlighting the need for robust cybersecurity measures to mitigate potential threats.
Background
KONNI is an APT group known for its longstanding involvement in cyber espionage. The group’s origins are believed to be in North Korea, although attribution in the world of cybersecurity can be challenging. KONNI has consistently directed its attacks towards South Korea, demonstrating a persistent interest in the region.
Modus Operandi
KONNI’s operations are characterized by their careful planning and execution. The group primarily relies on spear-phishing emails and malicious documents as entry points for their cyberattacks. By crafting convincing lures and tailored content, they aim to deceive specific individuals or organizations.
Objectives
KONNI’s primary objectives include:
Tools and Techniques
KONNI employs a wide range of malware and tools to achieve its objectives. The group is known for its adaptability, frequently adjusting tactics to evade detection and attribution. Their toolkit includes custom malware, remote access trojans (RATs), and other malicious software.
Attack Chain
The typical attack chain associated with KONNI begins with the download of an ISO image from an Internet-accessible location (ITW URL). This ISO image is used to deploy another zip file containing malicious scripts, initiating the attack process.
https://github.com/blackorbird/APT_REPORT/tree/master/konni
Cryptocurrency Phishing Scam Results in Loss of $299.49 rETH (Approximately $534,000)
A cryptocurrency investor has reported a significant loss of 299.49 rETH, equivalent to approximately $534,000, as a result of a cunning crypto phishing scam. The victim unwittingly granted token approval to the scammer by signing “increaseAllowance” transactions, enabling the theft of their digital assets.
The incident unfolded as follows:
Recommendations:
The loss of 299.49 rETH, valued at approximately $534,000, to a cryptocurrency phishing scam serves as a reminder that users must remain vigilant and exercise caution when interacting with their digital assets. Crypto scams continue to evolve, and users are urged to take proactive measures to safeguard their investments and personal information. Law enforcement agencies and cryptocurrency platforms are actively working to track down and apprehend the individuals responsible for such attacks.
In the realm of database management, PostgreSQL is recognized as a leading open-source database system, known for its advanced features and user-friendly interface. To enhance database management further, pgAdmin, a widely-used graphical user interface (GUI) tool, simplifies the interaction between users and PostgreSQL databases. However, as with any software, even powerful tools can be susceptible to vulnerabilities.
A critical remote code execution (RCE) vulnerability, identified as CVE-2023-5002, has been identified in pgAdmin, the popular GUI management tool for PostgreSQL databases. This vulnerability affects all versions of pgAdmin prior to 7.7. The vulnerability originates from pgAdmin’s HTTP API, which is responsible for validating user-defined paths leading to external PostgreSQL utilities, such as pg_dump or pg_restore.
Before version 7.7, pgAdmin’s security checks exhibited a weakness. The API did not effectively restrict the execution of server code, allowing authenticated users with appropriate access privileges to execute arbitrary commands on the server. This vulnerability could be exploited by cleverly crafting commands as filenames and having them validated through the API. It’s akin to an intruder sneaking in through a backdoor while the security guard checks the front entrance.
Of particular concern is the potential for malicious users to inject and execute harmful commands within the pgAdmin server environment.
Notably, this issue does not impact users running pgAdmin in desktop mode.
The CVE-2023-29357 PoC exploit has been developed in C# and is compatible with .NET Framework version 4.7.2. Visual Studio 2017 is the recommended Integrated Development Environment (IDE) for building and compiling the exploit. To ensure all dependencies are correctly installed, it is advisable to use the NuGet Package Manager to manage and install any missing packages.
Usage Instructions
The CVE-2023-29357 PoC exploit can be executed using the following command format:
CVE-2023-29357.exe http(s)://yoursharepoint.lol [-v]
https://github.com/LuemmelSec/CVE-2023-29357
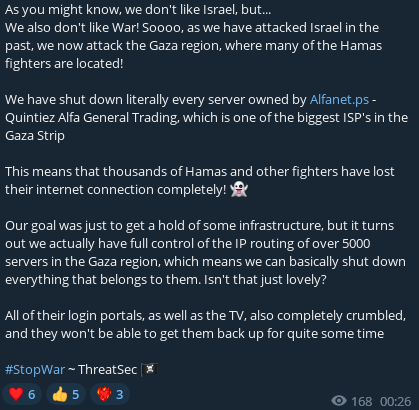
This advisory report addresses concerning developments involving hacker groups targeting infrastructure in Israel and the United States. Two prominent hacker groups, “Ghosts of Palestine” and “Killnet,” have recently made public statements and claims related to cyberattacks on government websites and internet service providers (ISPs). While these incidents are indicative of ongoing cyber threats, the severity and authenticity of these claims should be assessed carefully. This report aims to provide an overview of the situation and recommends proactive security measures.
Threat Landscape
The Palestinian hacker group “Ghosts of Palestine” has issued an invitation to hackers worldwide, urging them to launch cyberattacks on both private and public infrastructure in Israel and the United States. Their statement, shared on social media platforms like Twitter, raises concerns about potential cyber threats targeting critical infrastructure and sensitive data.
Killnet
The Russian hacker group “Killnet” has claimed responsibility for hacking the Israel government website and expressed support for Hamas. Their statement places blame on the Israeli government for ongoing conflicts. While the group’s motivations and affiliations are apparent, the authenticity and extent of their cyberattacks require thorough investigation.
#ThreatSec
An entity known as “#ThreatSec” has claimed to have breached and disabled the entire Palestinian Gaza ISP infrastructure of alfanet.ps. The veracity of this claim should be subject to investigation by relevant authorities.