
Week in Overview(16 Apr-23 Apr) – 2024
4. CVE-2024-3832:
5. CVE-2024-21111 in Oracle VirtualBox:
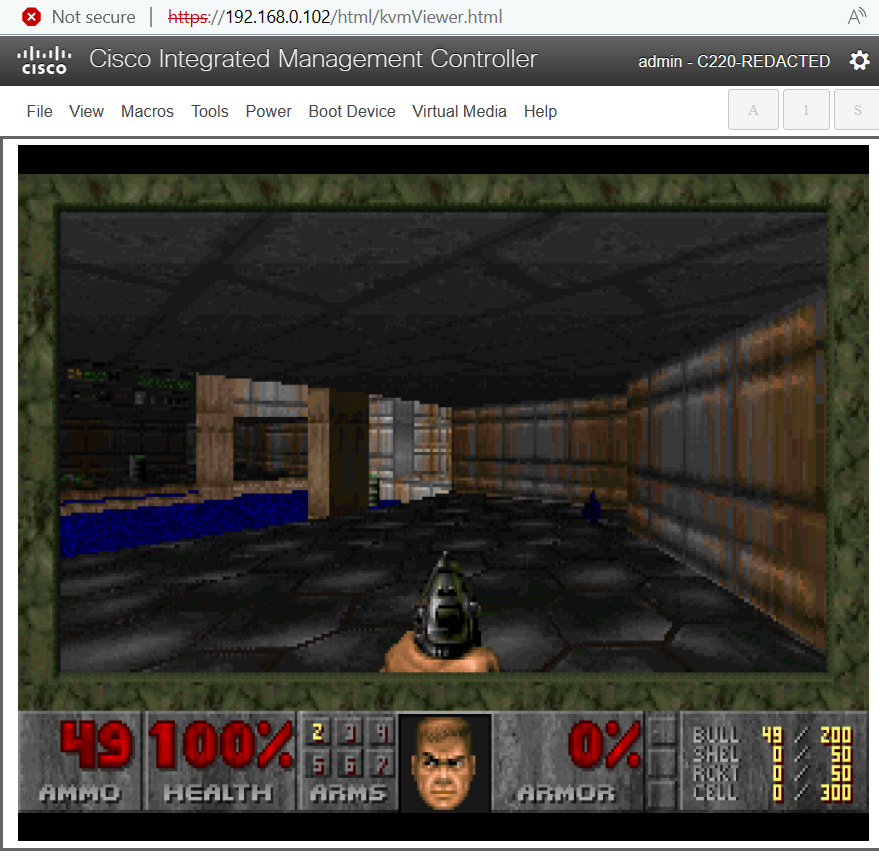
The Cisco C195 is a robust Email Security Appliance (ESA) device designed to function as an SMTP gateway, enhancing network security by managing email traffic at the perimeter. Like other appliances in Cisco’s range, the C195 is engineered with stringent security measures to prevent unauthorized code execution, ensuring the integrity of its operations. However, recent endeavors have seen individuals exploring the device’s potential beyond its intended purpose.
In a notable adventure, a Cisco C195 appliance was disassembled with the aim of repurposing it as a general server. Despite assertions online that the device’s secure boot mechanisms would thwart attempts to run alternate operating systems, innovative exploration led to a breakthrough. The Cisco C195 was successfully jailbroken, enabling the execution of unintended code. Central to this exploit was the discovery of a vulnerability within the CIMC (Cisco Integrated Management Controller) body management controller, identified as CVE-2024-20356. This vulnerability, when leveraged by an authenticated high-privilege user, grants root access to the server’s BMC (Baseboard Management Controller), which holds considerable influence over various system components.
The ultimate objective of this endeavor was rather whimsical: to run the iconic video game DOOM on the Cisco C195 device. Following the successful jailbreak, a comprehensive toolkit for detecting and exploiting the CVE-2024-20356 vulnerability was released on GitHub, facilitating further exploration and experimentation.
One of the primary targets of this exploit chain was the BIOS (Basic Input/Output System), the firmware responsible for initializing hardware during the boot process. By examining different BIOS versions and assessing their impact on device operations, researchers sought to uncover potential attack surfaces and exploit vectors. Despite encountering challenges posed by the device’s secure boot configuration, innovative techniques such as flash chip removal and DIY socket creation were employed to facilitate BIOS modification.
To mitigate the risk posed by such vulnerabilities, it is recommended to adhere to best practices such as changing default credentials, implementing strong password policies, and promptly updating devices to patch known vulnerabilities like CVE-2024-20356. By adopting proactive security measures, organizations can reduce the likelihood and impact of exploitation, safeguarding their network infrastructure from emerging threats.
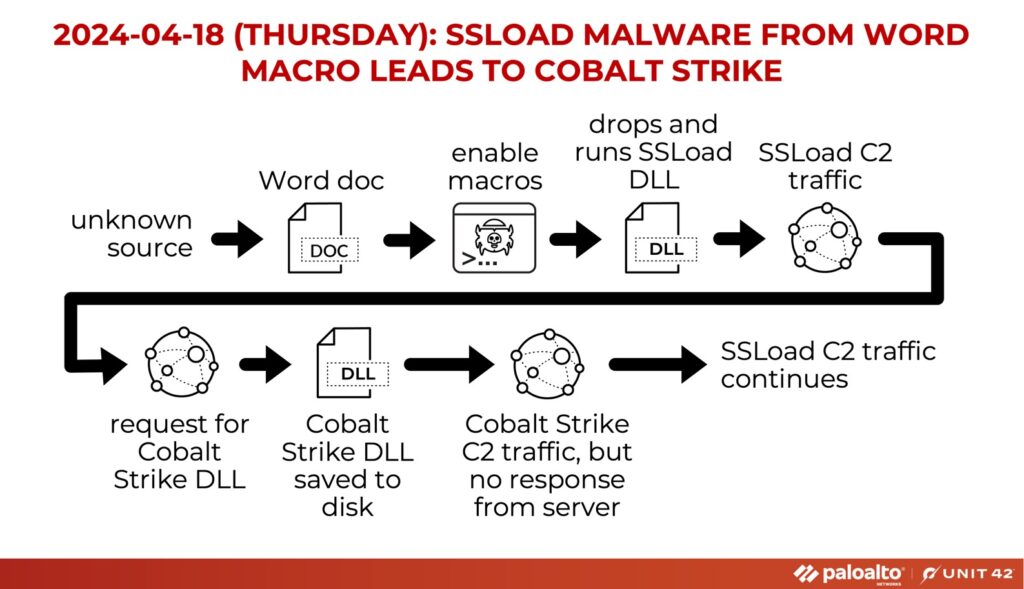
On April 18, 2024, a sophisticated cyberattack campaign was observed, where an infection chain involving SSLoad malware ultimately led to attempted deployment of Cobalt Strike, a notorious tool used by threat actors for advanced persistent threats (APTs) and targeted attacks.
Infection Chain:
Associated Files:
Infection Traffic:
The infection traffic included communication over ports 443 and 80, with attempts to connect to various servers for command and control purposes. Notably, traffic to retrieve the Cobalt Strike DLL was observed on port 80, targeting the server at “212.18.104[.]28.”
Cobalt Strike Traffic:
Upon attempted execution, the Cobalt Strike DLL generated traffic directed to the server at “193.32.176[.]22” over port 8080. However, no response was received from the server, indicating potential disruption or evasion tactics by the attackers.
This incident highlights the evolving sophistication of cyber threats, where multi-stage infection chains and attempts to deploy advanced tools like Cobalt Strike are used to infiltrate and compromise targeted systems. Organizations are urged to remain vigilant and implement robust cybersecurity measures to defend against such threats.
A security advisory has been issued regarding CVE-2024-3832, highlighting an object corruption vulnerability affecting WebAssembly (wasm) functions installation. This vulnerability, reported by Man Yue Mo of GitHub Security Lab, was disclosed on March 27, 2024. The issue arises due to object corruption in V8, the JavaScript engine used in Google Chrome and other Chromium-based browsers.
The vulnerability allows for the manipulation of wasm functions during installation, leading to potential object corruption. While no Proof-of-Concept (PoC) has been provided, the vulnerability’s severity is underscored by its classification as “High” and the reward of $20,000 offered for its discovery.
The vulnerability involves a scenario where installing wasm functions can cause object corruption, potentially leading to security breaches. The exploit revolves around the manipulation of properties and elements within JavaScript objects, specifically targeting the WebAssembly global object.
Previous similar vulnerabilities, such as CVE-2021-30561 and CVE-2022-1486, have been reported, indicating a recurring pattern of object corruption issues in the context of JavaScript and wasm integration.
Efforts to address this vulnerability include adding runtime name collision checks and implementing safeguards during property appending to prevent the creation of corrupted JavaScript objects. Additionally, historical write-ups, such as CVE-2023-2935, provide insights into similar exploitation techniques involving duplicate property primitives and object reshuffling.
The vulnerability analysis suggests potential exploitation avenues through type confusion and object reshuffling, emphasizing the need for thorough mitigation measures to protect against malicious attacks leveraging this vulnerability.
Ultimately, the security community’s ongoing efforts to identify and address vulnerabilities in JavaScript engines like V8 highlight the importance of continuous security research and proactive vulnerability management to safeguard against emerging threats.
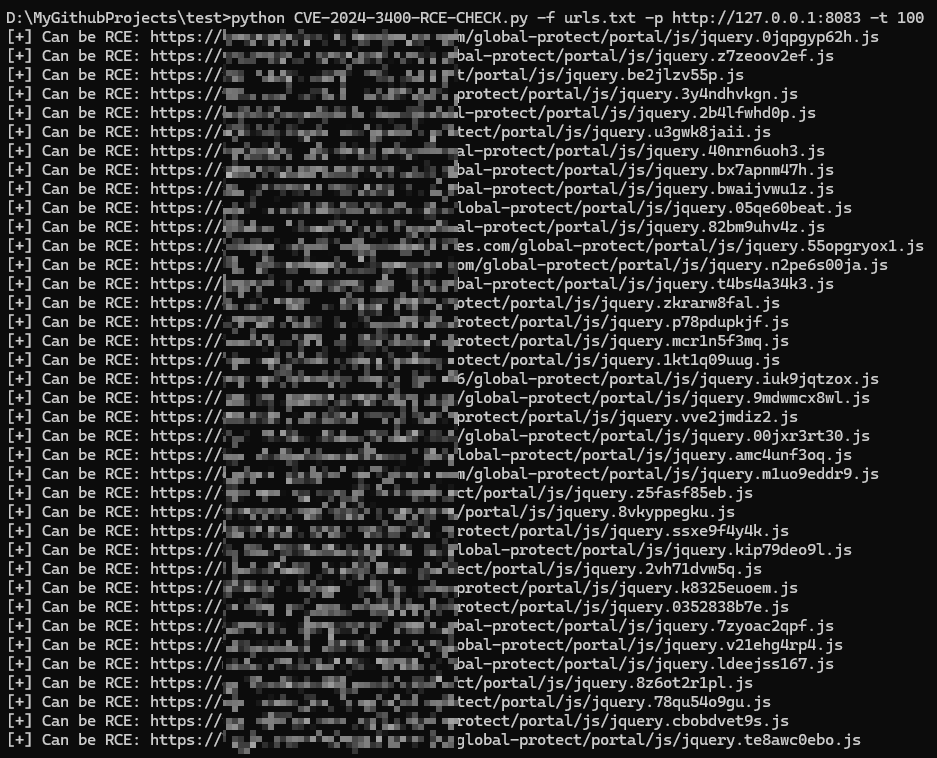
CVE-2024-3400-RCE is a critical security vulnerability that affects Palo Alto Networks GlobalProtect, a widely used VPN solution. This vulnerability allows remote attackers to execute arbitrary code on affected systems, potentially leading to complete compromise of the target network.
The vulnerability was discovered through a technique known as “Cyberspace Mapping Dork,” which involves using specialized search engines like Fofa, Zoomeye, Hunter.how, and Shodan to identify systems running vulnerable software.
To check for the vulnerability, a Python script named CVE-2024-3400-RCE-CHECK.py is provided. This script scans a list of URLs specified in a text file and attempts to exploit the vulnerability by connecting to the target systems using the provided payload and port.
References to further information and analysis of the vulnerability are provided via GitHub repositories, AttackerKB, and Watchtower Labs. These resources offer details on the vulnerability’s exploitation, potential impact, and mitigation strategies.
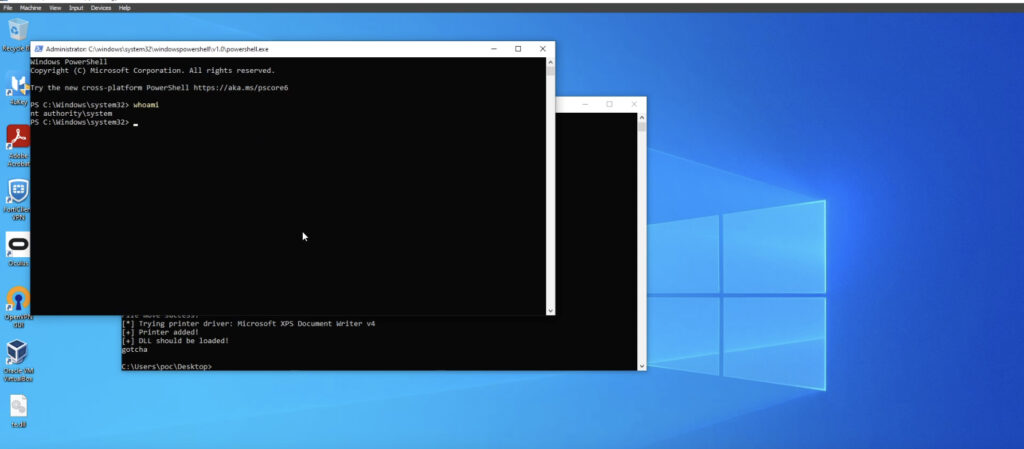
A security researcher has recently disclosed a Proof-of-Concept (PoC) exploit for a critical vulnerability discovered in Oracle VirtualBox. Identified as CVE-2024-21111, this flaw affects VirtualBox versions prior to 7.0.16. It poses a significant threat as it enables attackers with limited access to a Windows system hosting VirtualBox to escalate their privileges.
The exploit code has been made publicly available on GitHub by the researcher, raising concerns about potential exploitation by malicious actors. This revelation underscores the importance of promptly updating VirtualBox installations to the latest secure version to mitigate the risk posed by this vulnerability.

Taylor Swift's new album has some people in the typewriter community worried about an influx of "newbs" that could drive up the price of typewriter-ing: https://t.co/hm6gxzxTIT
— 404 Media (@404mediaco) April 22, 2024
In the lead-up to the release of Taylor Swift’s album “The Tortured Poets Department,” the singer-songwriter sparked a buzz within both her fanbase and an unexpected community: vintage typewriter enthusiasts. Swift’s teaser video, featuring her typing the words “as she was leaving it felt like breathing” on a typewriter, ignited speculation among fans and typewriter aficionados alike.
Members of typewriter-focused online forums and social media groups expressed mixed reactions to Swift’s typewriter-themed promotional content. Some expressed concern over a potential surge in demand for typewriters, anticipating higher prices and competition for vintage models. Others welcomed the attention, viewing it as an opportunity to introduce newcomers to the hobby and preserve interest in vintage typewriters for future generations.
The release of Swift’s music video for “Fortnight,” featuring typewriter scenes with Post Malone, further fueled discussions within the typewriter community. Identified as a Royal 10, the typewriter featured in Swift’s promotional materials led enthusiasts to speculate about its history and value.
Swift’s frequent references to typewriters in her music and promotional materials, including lyrics mentioning the “Tortured Poets Department” and imagery of her using typewriters, added to the intrigue. While some worried about a potential influx of inexperienced buyers, others noted the hobby’s resilience over the years, citing periodic surges in popularity and the enduring appeal of vintage typewriters.
Despite concerns, many in the typewriter community remained optimistic about the hobby’s future. Some saw Swift’s influence as an opportunity to educate newcomers and foster a deeper appreciation for typewriters’ craftsmanship and history. Ultimately, the community hoped that Swift’s involvement would spark renewed interest in typewriters and contribute to their preservation for years to come.