BreachForum, a notorious online platform for trading stolen data, has been seized by the United States Federal Bureau of Investigation (FBI). The forum’s landing page now displays a notice confirming the FBI’s control and shows images of the administrators’ Telegram profile pictures behind bars. This seizure disrupts a key hub for cybercriminals and represents a significant step in ongoing efforts to combat cybercrime. The FBI is likely analyzing data and activities from the site to identify and prosecute individuals involved.
CVE-2024-4985: GitHub Enterprise Server Authentication Bypass
CVE-2024-4985 is an authentication bypass vulnerability in GitHub Enterprise Server (GHES), affecting versions prior to 3.13.0. The vulnerability exploits flaws in the handling of encrypted SAML claims, allowing attackers to create fake SAML assertions that GHES fails to validate correctly. This vulnerability can enable unauthorized access to GHES instances. Exploiting this involves crafting a specific SAML assertion and sending it to the GHES server. The issue has been addressed in version 3.13.0.
Hijack Loader
Hijack Loader, also known as IDAT Loader, is malware that emerged in September 2023 and has quickly become one of the most widely used loaders. The latest version includes enhanced anti-evasion techniques, such as avoiding inline API hooking, adding Windows Defender exclusions, bypassing User Account Control (UAC), and using process hollowing. This version decrypts and parses a PNG image to load its second-stage payload, which is modular and primarily focuses on injecting the main instrumentation module. Hijack Loader is currently ranked 6th on the ANY.RUN Trends Tracker and delivers payloads like Amadey, Lumma Stealer, Meta Stealer, Raccoon Stealer V2, Remcos RAT, and Rhadamanthys.
Vidar Stealer is a malware variant known for its ability to steal sensitive information from infected systems. Recently, changes have been observed in the response headers of servers associated with Vidar Stealer’s infrastructure. These changes are being tracked using specific queries and tools like Censys. Vidar Stealer is often deployed to exfiltrate data such as passwords, cryptocurrency wallet contents, and other personal information.
QNAP QTS – QNAPping at the Wheel (CVE-2024-27130 and Friends)
QNAP QTS is a NAS operating system that has been found vulnerable to multiple security issues, including CVE-2024-27130, an unauthenticated stack overflow bug that allows remote code execution. Researchers discovered this vulnerability and others while analyzing the shared codebase of QTS, QuTSCloud, and QTS hero. The vulnerabilities stem from legacy code and poor security practices, such as hardcoded credentials and memory corruption issues. Patches have been released for some vulnerabilities, but others remain unaddressed.
PDF.js is an open-source JavaScript library used for rendering PDF documents in web browsers. It allows users to view and interact with PDFs directly within the browser without needing external plugins. The library is widely used for its ease of integration and functionality, enabling features like text selection, searching, and document navigation. However, it must be regularly updated to avoid potential security vulnerabilities that could be exploited by attackers.
CVE-2024-32002 is a security vulnerability discovered in PDF.js, affecting versions prior to 3.0.0. This vulnerability allows attackers to execute arbitrary code on the user’s system by exploiting a flaw in the way PDF.js processes certain PDF files. An attacker can craft a malicious PDF file that, when opened, triggers the vulnerability and executes code with the same permissions as the user running the browser. Updating to PDF.js version 3.0.0 or later mitigates this risk.
This repository contains a Proof of Concept (PoC) for CVE-2024-32002, a Remote Code Execution (RCE) vulnerability in Git submodules. The exploit demonstrates how a malicious payload can be triggered via a recursive clone of a Git repository.
Before running the PoC, create the following repositories on your remote Git server or feel free to change the names as needed:
Update the repository paths in the PoC script accordingly if you change the names.
The exploit leverages Git submodules to execute a payload on the target system when the repository is cloned recursively. This PoC is tested on macOS.
HULK_REPO=”[email protected]:safebuffer/hulk.git”
pullme_REPO=”[email protected]:safebuffer/submod.git”
# Final Exploit Repo
SMASH_REPO=”[email protected]:safebuffer/smash.git”
Triggering the Exploit
To trigger the exploit, run the poc.sh script and then execute the following command:
git clone –recursive $SMASH_REPO
Payload
The default payload in this PoC opens the Calculator application on macOS. You can change this to any payload of your choice.
/System/Applications/Calculator.app/Contents/MacOS/Calculator
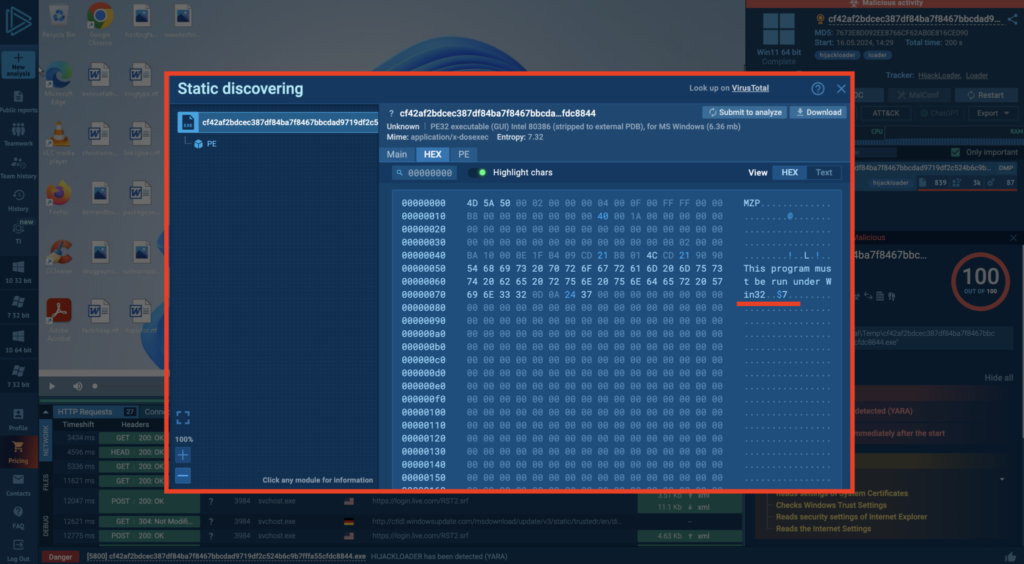
The new version of Hijack Loader employs a modular architecture, which primarily focuses on the injection of the main instrumentation module. This architecture allows the malware to load additional modules as needed, making it more flexible and adaptable to various environments.
To enhance its stealth and evade detection, the malware has adopted several advanced techniques:
Security researchers identified seven new modules associated with Hijack Loader in March and April 2024, indicating ongoing development and enhancement by the threat actors.
Background on Hijack Loader
Hijack Loader, also known as IDAT Loader, emerged in September 2023 and has quickly gained popularity. It is now one of the most widely used loaders, ranking sixth in the ANY.RUN Trends Tracker. This ranking is based on the analysis of public sandbox submissions.
Common Payloads Delivered by Hijack Loader
The following are some of the common payloads delivered by Hijack Loader:
In a specific analysis session, the second-stage payload did not download because the Command and Control (C2) server was inactive at the time. Despite this, the detection mechanisms of ANY.RUN remain robust.
Latest Hijack Loader Indicators of Compromise (IOCs)
The following are the latest IOCs for Hijack Loader, collected from the Malware Trends Tracker. These artifacts are dynamically updated with new public analysis sessions and uploads to ANY.RUN.
IPs
Hashes
URLs
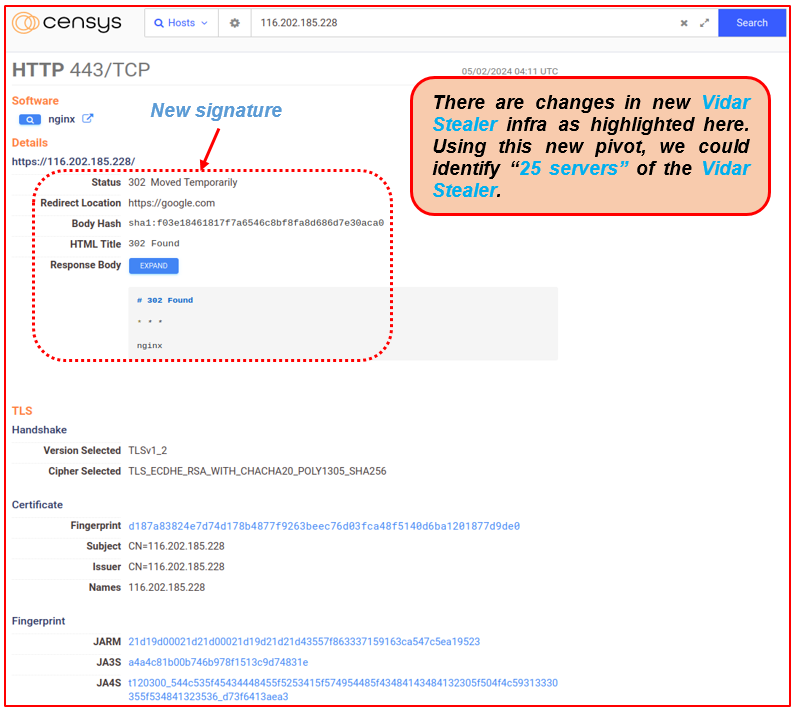
Recent investigations into the Vidar Stealer infrastructure have revealed notable changes in the response headers associated with its command and control (C2) servers. These modifications could indicate evolving tactics and techniques employed by the threat actors behind Vidar Stealer, potentially impacting detection and mitigation strategies.
Overview of Vidar Stealer
Vidar Stealer is a notorious piece of malware primarily used to exfiltrate sensitive information from infected systems. This includes passwords, credit card information, and other personal data. The malware operates by communicating with C2 servers to send collected data and receive instructions.
Our analysis, supported by data from Censys and other sources, highlights specific changes in the response headers returned by the C2 servers of Vidar Stealer. These observations are critical for understanding how the malware infrastructure is adapting to evade detection.
Changes in Response Headers
The following changes have been identified in the response headers of Vidar Stealer’s C2 servers:
Analytical Insights
The changes in response headers suggest a deliberate attempt by the operators of Vidar Stealer to adjust their infrastructure’s fingerprint. This makes it harder for security tools to reliably identify and block traffic associated with the malware. Such adaptability is a common trait among sophisticated threat actors aiming to maintain persistence and evade detection.
A critical vulnerability, tracked as CVE-2024-4985, has been discovered in GitHub Enterprise Server (GHES), allowing unauthorized access to instances without requiring pre-authentication. This flaw affects all GHES versions prior to 3.13.0.
The vulnerability exploits the way GHES handles encrypted Security Assertion Markup Language (SAML) claims. An attacker can craft a fake SAML claim containing valid user information. When GHES processes this fake SAML claim, it fails to correctly validate its signature, thus granting unauthorized access to the GHES instance.
Proof of Concept (PoC):
To demonstrate the exploitation of this vulnerability, follow these steps:
This post details CVE-2024-4367, a vulnerability in PDF.js found by Codean Labs. PDF.js is a JavaScript-based PDF viewer maintained by Mozilla. This bug allows an attacker to execute arbitrary JavaScript code as soon as a malicious PDF file is opened. This affects all Firefox users (versions below 126) because PDF.js is used by Firefox to display PDF files. It also impacts many web- and Electron-based applications that indirectly use PDF.js for preview functionality.
If you are a developer of a JavaScript/TypeScript-based application that handles PDF files in any way, we recommend checking that you are not indirectly using a vulnerable version of PDF.js. See the end of this post for mitigation details.
PDF.js is commonly used in two scenarios:
The PDF format is notoriously complex, with support for various media types, intricate font rendering, and even rudimentary scripting. This complexity makes PDF readers a common target for vulnerability researchers. While PDF.js avoids memory corruption issues by being written in JavaScript rather than C or C++, it introduces its own set of risks.
Surprisingly, this bug is not related to the PDF format’s scripting functionality. Instead, it stems from an oversight in a specific part of the font rendering code.
Fonts in PDFs can come in various formats. For modern formats like TrueType, PDF.js mostly relies on the browser’s font renderer. For other formats, PDF.js manually turns glyph (character) descriptions into curves on the page. To optimize performance, a path generator function is pre-compiled for each glyph by creating a JavaScript Function object with a body (jsBuf) containing the path instructions.
NAS devices, typically used in multi-user environments such as offices, are attractive targets for attackers due to the potential for acquiring large amounts of sensitive data. Given the long legacy and history of security weaknesses in QNAP’s QTS codebase, we decided to conduct a thorough analysis, focusing on three main variants: QTS, QuTSCloud, and QTS hero.
Initial Analysis
We began our exploration with QuTSCloud, a VM-optimized version of QTS. After obtaining and setting up a virtual machine, we delved into the system, discovering a Linux-based environment with various middleware components exposed via HTTPS for management purposes. Notably, the middleware was written in C, which is notorious for security issues such as memory corruption.
Vulnerability Discovery
Our initial examination revealed several bugs, mostly memory corruption issues like double frees and buffer overflows. One significant find was CVE-2024-27130, an unauthenticated stack overflow bug that could lead to remote code execution. Here’s a high-level overview of our discovery process:
CVE-2024-27130 is a particularly concerning bug due to its unauthenticated nature. By exploiting this stack overflow, an attacker can execute arbitrary code. Here’s a simplified exploitation sequence:
QNAP has released patches for some of the vulnerabilities we found. The following products have been updated:
For those still affected, we recommend taking systems offline or heavily restricting access until patches are available. Additionally, users should monitor for unusual activity that could indicate exploitation of these bugs.

BreachForum, a notorious online platform known for facilitating the exchange of stolen data, has been seized once again. The current display page on the forum reveals that the United States Federal Bureau of Investigation (FBI) has taken control and is actively reviewing the site.
Upon visiting BreachForum, users are now greeted with a stark notice indicating the site’s new status. The message clearly states that the forum is under the control of the FBI. In addition to this, the notice prominently features an image of the current administrators’ Telegram profile pictures, depicted behind bars, symbolizing their capture and the forum’s shutdown.
The seizure of BreachForum marks another significant victory in the ongoing battle against cybercrime. This forum has long been a hotspot for cybercriminals to trade in stolen data, including personal information, financial records, and other sensitive materials. The FBI’s intervention is a critical step in disrupting these illicit activities and bringing perpetrators to justice.
BreachForum has faced law enforcement action before, reflecting its persistent role in cybercrime. The forum’s repeated shutdowns highlight both the resilience of cybercriminal communities and the ongoing efforts by global law enforcement agencies to curb their operations.
With the forum under FBI control, the focus will likely shift to analyzing the data and activities that occurred on the site. This could lead to further arrests and the dismantling of other cybercriminal networks connected to BreachForum. Users who frequented the site for illegal purposes are now at risk of identification and prosecution.
The seizure of BreachForum serves as a reminder of the relentless efforts by law enforcement to combat cybercrime. While the forum’s closure will disrupt cybercriminal activities temporarily, it also underscores the need for continued vigilance and cooperation in the cybersecurity community to address the evolving threat landscape.