
Week in Overview(5 Mar-12 Mar) – 2024
4. Critical Security Alert: CVE-2024-1403 in Progress OpenEdge: CVE-2024-1403, a critical vulnerability in Progress OpenEdge, allows unauthorized users to obtain admin permissions and potentially execute remote code. While no path to Remote Code Execution (RCE) has been discovered, the exploit poses significant risks.
5. Urgent Security Alert: CVE-2024-21899 Exploits Targeting QNAP NAS Systems: QNAP NAS systems face exploitation via CVE-2024-21899, which includes an authentication bypass vulnerability and other critical flaws. Attackers could compromise affected devices, emphasizing the importance of immediate updates to patched versions.
6. Unraveling Latrodectus: A Sophisticated Malware Campaign: An analysis of the Latrodectus malware campaign reveals its complex attack chain, involving URL redirection, malicious JavaScript, SMB, MSI, and DLL files. The campaign’s infrastructure, indicators of compromise (IOCs), and samples are detailed.
7. Unveiling a Critical Vulnerability in Microsoft Outlook: CVE-2024-21378: CVE-2024-21378 exposes a critical vulnerability in Microsoft Outlook, potentially allowing attackers to execute arbitrary code. The vulnerability affects Outlook’s handling of certain email content, posing significant security risks to users.
In the ever-evolving landscape of cybersecurity threats, 2023 saw a significant revelation by NetSPI regarding a critical vulnerability lurking within Microsoft Outlook. This vulnerability, designated CVE-2024-21378, opened the doors to authenticated remote code execution (RCE) via synced form objects. In this exposé, we delve into the discovery of this flaw and its subsequent weaponization, utilizing modifications to Ruler, an Outlook penetration testing tool initially published by SensePost. It’s crucial to note that a pull request containing proof-of-concept code is on the horizon, ensuring organizations have adequate time to patch their systems.
The Vulnerability Unveiled
The genesis of this vulnerability traces back to an original attack variant outlined by Etienne Stalmans at SensePost (Orange CyberDefense) in 2017. This exploit relied on VBScript code embedded within Outlook form objects, facilitating code execution with mailbox access. Although a patch was issued in response, mandating allowlisting for script code in custom forms, the syncing capability of these form objects remained unchanged.
Beneath the surface, forms are MAPI synced using IPM.Microsoft.FolderDesign.FormsDescription objects, housing special properties and attachments crucial for form installation on clients. The vulnerability stems from flaws in this installation process:
In-Depth Analysis
This discovery marks the culmination of a series of attacks leveraging compromised credentials to sync objects through Exchange. Beginning with Nick Landers’ 2015 revelation on the exploitation of Outlook Rules for RCE, subsequent discoveries by Etienne at SensePost and Nick uncovered additional vectors, ultimately patched by Microsoft. SensePost’s comprehensive blogs delved into these vulnerabilities and the underlying technologies, alongside the exploitation tool, Ruler.
Our foray into this research was spurred by the vast, yet underexplored attack surface presented by Outlook. Leveraging insights gained from engagements utilizing Device Code phishing/vishing, we embarked on a meticulous exploration of Outlook forms, employing tools like MFCMAPI and ProcMon to dissect the underlying technology.
Exploitation and Verification
Our journey began with attempts to demonstrate local code execution. Crafting a custom form configuration file, we imported it into Outlook to install a form, effectively setting the stage for exploitation. Through iterative testing, we confirmed the execution of arbitrary DLLs, a pivotal milestone in our exploit development.
Further exploration via MFCMAPI provided deeper insights into the workings of Outlook, unraveling the mechanics of form installation and storage within the system. This meticulous analysis unveiled the extent of the vulnerability, showcasing the potential for not just code execution but also arbitrary registry writes and file manipulation, all from within the confines of Outlook.
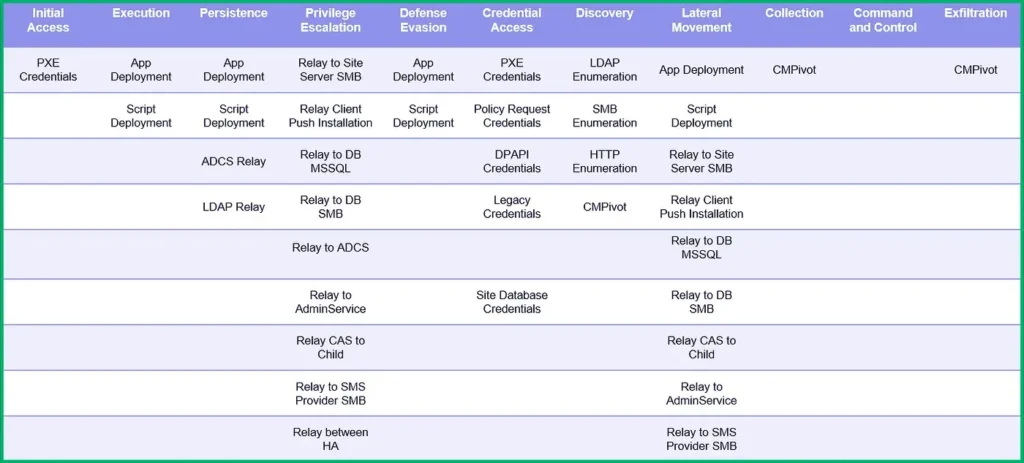
Security researchers at SpecterOps have unveiled Misconfiguration Manager, a comprehensive knowledge base repository designed to address the vulnerabilities stemming from improperly configured instances of Microsoft’s Configuration Manager (MCM). This initiative aims to equip both defenders and offensive security professionals with the necessary tools and insights to bolster security and mitigate potential risks associated with MCM deployment.
Understanding Microsoft Configuration Manager (MCM)
Formerly known as System Center Configuration Manager (SCCM, ConfigMgr), MCM has been a staple in Active Directory environments since 1994, serving as a crucial tool for administrators to manage servers and workstations within Windows networks. However, its extensive capabilities also make it a prime target for security research and exploitation, with adversaries seeking to leverage misconfigurations to gain unauthorized access and administrative privileges.
The Need for Misconfiguration Management
The complexity of MCM configurations often leaves room for vulnerabilities, with default settings and practices inadvertently exposing systems to potential exploitation. As highlighted by SpecterOps researchers Chris Thompson and Duane Michael, common misconfigurations such as overly privileged network access accounts (NAAs) can pave the way for attackers to escalate privileges and compromise critical components within the environment.
Attack Scenarios and Risks
The release of Misconfiguration Manager sheds light on various attack scenarios and risks associated with improperly configured MCM deployments. From compromising SharePoint accounts to achieving domain controller status, attackers can exploit vulnerabilities in MCM to execute payloads, elevate privileges, and infiltrate the network. Examples provided by Michael underscore the severity of these risks, emphasizing the need for proactive defense measures.
Empowering Defenders and Offensive Professionals
The Misconfiguration Manager repository, curated by Thompson, Garrett Foster, and Duane Michael, serves as a comprehensive resource for administrators, offering insights into MCM attack vectors and defensive strategies. With 22 techniques outlined, defenders can gain a deeper understanding of potential vulnerabilities and take proactive steps to mitigate risks. Additionally, offensive professionals can leverage this repository to enhance their knowledge of MCM’s attack surface and refine their penetration testing strategies.
Defense Strategies: PREVENT, DETECT, CANARY
The repository categorizes defense actions into three key areas:

The cybersecurity landscape is often fraught with sophisticated threats, and the emergence of Latrodectus exemplifies this paradigm shift. This clandestine campaign operates through a meticulously orchestrated sequence, leveraging a series of stages encompassing URL manipulation, JavaScript execution, SMB exploitation, MSI installation, and DLL payload execution. In this narrative, we dissect the modus operandi of Latrodectus, shedding light on its intricacies and implications.
Initial Entry: URL Manipulation and JavaScript Execution
The inception of Latrodectus typically begins with the manipulation of URLs, luring unsuspecting users into accessing malicious JavaScript (.js) files. These files, often disguised as innocuous content, serve as the conduit for initiating the malware deployment chain. Upon execution via tools like wscript, these JavaScript payloads initiate the next phase of the attack.
SMB Exploitation and MSI Installation
Once the JavaScript payload is executed, Latrodectus proceeds to exploit vulnerabilities within the Server Message Block (SMB) protocol. By leveraging SMB, the malware establishes a connection to a remote server, facilitating the retrieval of malicious .msi (Windows Installer) files. These MSI files, typically embedded within the JavaScript payload or retrieved from remote locations, serve as the vehicle for deploying the malware onto the victim’s system.
DLL Payload Execution
With the MSI files successfully retrieved, Latrodectus proceeds to execute the embedded DLL payloads. Utilizing system utilities like msiexec.exe, the malware silently installs these DLLs onto the victim’s system, often within temporary directories to evade detection. Once installed, these DLLs are invoked for execution through system utilities like rundll32.exe, unleashing their malicious payloads.
Indicators of Compromise (IOCs) and Command & Control (C2) Infrastructure
As with any sophisticated malware campaign, Latrodectus leaves behind a trail of indicators of compromise (IOCs) and operates through a network of command and control (C2) infrastructure. These IOCs, meticulously documented by security researchers, provide crucial insights into the behaviors and characteristics of the malware. Additionally, the C2 infrastructure serves as the linchpin for orchestrating and coordinating malicious activities, encompassing a network of domains and servers.

This post explores the utilization of internal proxies within a target network for various purposes such as lateral movement, firewall evasion, trust exploitation, and defense evasion. We’ll delve into techniques using tools like PowerShell, netsh, and SpecterInsight.
Techniques:
Netsh Interface Portproxy:
TCP Proxy Using Implant Modules:

A critical vulnerability, CVE-2024-1403, has been uncovered in Progress OpenEdge, posing significant security risks to affected systems. This authentication bypass flaw enables unauthorized users to gain administrative privileges, potentially allowing them to manipulate services within the environment. While a direct path to Remote Code Execution (RCE) has not been confirmed, the severity of this vulnerability demands immediate attention and remediation efforts.
Overview of CVE-2024-1403:
The essence of CVE-2024-1403 lies in an authentication bypass mechanism within Progress OpenEdge. Specifically, if the username matches the string “NT AUTHORITY/SYSTEM,” the system grants administrative permissions, bypassing the authentication process. This loophole effectively grants unauthorized users elevated privileges, compromising the integrity and security of the system.
Risk Implications:
The implications of CVE-2024-1403 are grave. With administrative access, attackers can exert control over critical services within the Progress OpenEdge environment. This could lead to unauthorized data access, manipulation, or even disruption of essential business operations. Furthermore, while a direct path to Remote Code Execution has not yet been confirmed, the nature of the vulnerability suggests that such an exploit may be feasible, further exacerbating the risk landscape.
Research and Exploit Details:
A comprehensive analysis of CVE-2024-1403 has been conducted by security researchers at Horizon3 AI, providing valuable insights into the vulnerability and its potential impact. Their deep dive into the exploit, along with a detailed write-up, sheds light on the technical intricacies of the flaw. Additionally, an exploit for CVE-2024-1403 has been made publicly available on GitHub, underscoring the urgency of addressing this vulnerability.

In a recent security advisory, QNAP has disclosed critical vulnerabilities affecting their NAS (Network Attached Storage) software solutions. These vulnerabilities pose significant risks, potentially enabling attackers to compromise affected devices and gain unauthorized access to sensitive data. Below is an overview of the identified vulnerabilities and recommended actions to mitigate the associated risks:
CVE-2024-21899: Authentication Bypass (CVSS 9.8)
The most critical vulnerability identified is an authentication bypass flaw (CVE-2024-21899), allowing attackers to remotely access QNAP NAS devices without requiring valid credentials. Exploiting this flaw requires minimal effort and could lead to unauthorized access to sensitive data stored on the device.
Other Vulnerabilities Identified:
Affected Systems:
These vulnerabilities impact various QNAP operating systems, including:
Recommended Actions:
QNAP strongly advises users to apply immediate updates to patched versions, including:
Updating is straightforward; administrators can navigate to the ‘Control Panel > System > Firmware Update’ pathway for QTS, QuTS hero, and QuTScloud systems. Meanwhile, myQNAPcloud users can utilize the ‘App Center’ to locate and update their software.

Okta, a leading cloud identity and access management solutions provider based in San Francisco, has refuted claims of a data breach after a threat actor purportedly shared files allegedly pilfered during an October 2023 cyberattack on a hacker forum.
In October 2023, Okta disclosed a security incident where its support system was compromised by hackers wielding stolen credentials. This breach facilitated the theft of cookies and authentication data for select customers. Subsequent internal investigations revealed that the incident impacted all users of the customer support system, raising concerns about potential breaches for multiple Okta clients. Notably, hackers utilized access tokens pilfered during the Okta breach to compromise one of Cloudflare’s self-hosted Atlassian servers.
Over the weekend, a cybercriminal under the pseudonym ‘Ddarknotevil’ claimed to have leaked an Okta Database containing information of 3,800 customers allegedly stolen during the 2023 breach. The leaked data purportedly includes user IDs, full names, company names, office addresses, phone numbers, email addresses, positions/roles, and other information.
Upon reaching out to Okta for clarification, the company promptly denied any association with the leaked data. An Okta spokesperson emphasized that the data does not belong to Okta and appears to be sourced from publicly available information on the internet. Despite claims made by the threat actor, Okta’s IT team conducted thorough investigations over the weekend and found no evidence of a breach within their systems.
Further analysis conducted by cyber-intelligence firm KELA supported Okta’s assertion, confirming that the shared data does not originate from Okta. Instead, KELA identified the data as matching a dump from a separate breach in July 2023, attributed to the threat actor ‘IntelBroker.’ The data was purportedly stolen from the National Defense Information Sharing and Analysis Center during the July breach.
In light of these developments, Okta reassures its customers of its commitment to maintaining robust security measures and continues to monitor its systems vigilantly to safeguard against potential threats. Despite the false alarm, the incident underscores the importance of proactive cybersecurity measures and swift response protocols in today’s digital landscape.