
Week in Overview(27 Feb-5 Mar) – 2024
4. Critical Vulnerability in Linksys E2000 Router (CVE-2024-27497):
5. Vulnerabilities in JetBrains TeamCity CI/CD Server:
6. New #PlanetStealer Malware Threat:
In February 2024, Rapid7’s vulnerability research team discovered two critical vulnerabilities affecting JetBrains TeamCity CI/CD server. These vulnerabilities, identified as CVE-2024-27198 and CVE-2024-27199, pose significant security risks to organizations utilizing TeamCity for their continuous integration and delivery processes.
Vulnerability Details:
Impact: Exploitation of these vulnerabilities could lead to severe consequences, including unauthorized access to sensitive information, manipulation of system configurations, and even the execution of arbitrary code on affected servers. Additionally, compromised TeamCity servers could serve as entry points for supply chain attacks, jeopardizing the integrity of software development pipelines.
Remediation: JetBrains responded promptly to these vulnerabilities by releasing TeamCity 2023.11.4 on March 3, 2024, which addresses both CVE-2024-27198 and CVE-2024-27199. Rapid7 strongly advises all TeamCity users to upgrade to the latest patched version immediately, regardless of their regular patch cycle. Failure to do so could leave systems vulnerable to exploitation.
For detailed instructions on upgrading to the patched version, please refer to the JetBrains release blog. Additionally, Rapid7 has provided sample indicators of compromise (IOCs) to assist in identifying potentially compromised systems.
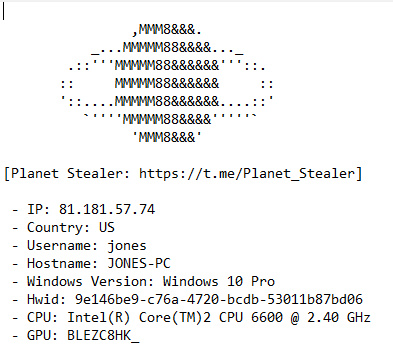
A new variant of the #PlanetStealer malware has been identified, this time written in Golang. It employs sophisticated techniques to infiltrate systems and exfiltrate sensitive data, posing a significant security threat to organizations and individuals alike.
Key Characteristics:
for the sandbox analysis:
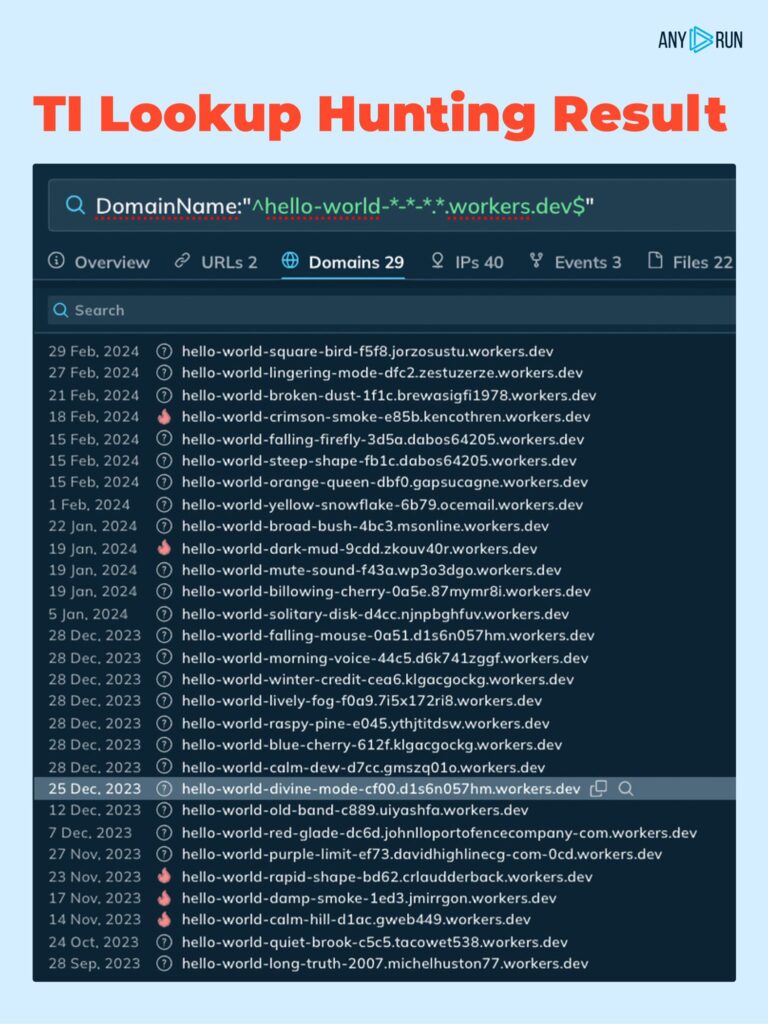
An ongoing phishing campaign has been identified, leveraging Telegram bots and pages hosted on Cloudflare Workers to steal credentials from unsuspecting victims. The attackers craft sophisticated phishing pages using various elements to mimic legitimate login interfaces and lure users into disclosing sensitive information.
Phishing Pages: The phishing pages are crafted using https://www.html-code-generator[.]com and contain the following components:
Cloudflare Workers Hosting: The attackers utilize https://workers.cloudflare.com to host these phishing pages, adding malicious content and additional functionality to enhance their effectiveness.
Telegram Exfiltration: Stolen credentials are exfiltrated via a Telegram bot using HTTP GET sendMessage requests. The stolen data, including email addresses, passwords, and IP addresses, is sent to the bot in a predefined template format.
Identifying the Threat: To identify malicious domains associated with this campaign, a regex pattern has been provided for creating hunting rules. Additionally, Threat Intelligence (TI) lookup queries can be performed to identify related domains.
Antivirus evasion, particularly in the context of Windows Defender, remains a critical concern for cybersecurity professionals. In this report, we explore the evolution of techniques used to evade Windows Defender detection, focusing on shellcode loaders. We revisit classic methodologies and analyze their effectiveness against modern antivirus solutions.
Background: Antivirus evasion has become a prominent topic within the cybersecurity community, with numerous articles and discussions dedicated to bypassing security measures. However, the efficacy of these techniques can diminish over time due to advancements in malware detection and prevention capabilities.
Methodology: Our analysis begins with a retrospective examination of older techniques, notably those outlined in a classic blog post discussing AV Bypass with Metasploit Templates and Custom Binaries. We attempt to replicate the steps outlined in the original post to assess their effectiveness against contemporary antivirus solutions.
Findings: Despite initial optimism, our attempts to evade Windows Defender detection using traditional shellcode loaders yielded mixed results. While some evasion techniques demonstrated marginal success, others were ineffective against modern antivirus signatures.
Challenges: The rapid evolution of antivirus technologies presents a significant challenge for malware developers and red team operators. Techniques that were once successful may now be detected by advanced heuristics and signature-based detection algorithms.
The Lazarus Group, a highly sophisticated threat actor known for its association with nation-state activities, has exploited a zero-day vulnerability in the Windows AppLocker driver (appid.sys). This flaw, identified as CVE-2024-21338, grants the attacker kernel-level access, allowing them to bypass security controls and disable security tools. The exploitation of this vulnerability poses significant risks to affected systems, potentially leading to unauthorized access, data theft, and system compromise.
Technical Details: The zero-day vulnerability in the Windows AppLocker driver (appid.sys) enables the Lazarus Group to gain elevated privileges, from administrative to kernel level, within the Windows operating system. By exploiting this flaw, attackers can bypass application whitelisting controls enforced by AppLocker and disable security tools, effectively undermining the system’s security posture.
Threat Actor: The Lazarus Group is a well-known threat actor with a history of conducting sophisticated cyber espionage and financially motivated attacks. This group has been associated with various high-profile cyber incidents, including the infamous WannaCry ransomware attack and the theft of funds from financial institutions.
Attack Vector: The exploitation of CVE-2024-21338 likely involves the delivery of a malicious payload through targeted phishing emails, watering hole attacks, or the exploitation of other vulnerabilities to gain initial access to the target system. Once inside the system, the attacker leverages the zero-day vulnerability to escalate privileges and execute further malicious activities.
A critical security vulnerability, identified as CVE-2024-27497, has been discovered in the Linksys E2000 router firmware version Ver.1.0.06 build 1. This flaw poses a severe risk to network security, allowing attackers to bypass authentication mechanisms and gain unauthorized access to the router’s administration interface, potentially leading to data theft, device compromise, and further malicious activity.
Vulnerability Details: The vulnerability resides within the position.js file of the router firmware, mishandling the session_key data used to secure user sessions. Exploiting this flaw, attackers can craftily retrieve active session keys, effectively bypassing the login process without requiring legitimate credentials.
Attack Scenario:
Impact:
The featured article explores the security risks associated with using virtual machines (VMs) for browsing potentially dangerous links and examines the vulnerabilities inherent in running the Chrome browser within a VM environment.
Key Points:
3. Chained Vulnerabilities: The article underscores the potential for attackers to chain these CVEs together, exploiting vulnerabilities in both the Chrome browser and the underlying VM infrastructure to achieve various levels of compromise, including remote code execution and privilege escalation.
4. Security Implications: The presence of these vulnerabilities highlights the importance of adopting a multi-layered security approach when using VMs for browsing unsafe content. While VMs offer isolation, they are not impervious to security risks, particularly when running vulnerable software such as web browsers.