
Week in Overview(5 Sep-12 Sep)
Key Findings
it is crucial for organizations and individuals to prioritize remediation and patching efforts to safeguard their systems and data. The following key findings highlight the importance of proactive measures to mitigate risks associated with various vulnerabilities and threats:
Apache Superset CVE-2023-39476
The Apache Superset project has released version 2.1.1, which includes crucial fixes for vulnerabilities that were previously reported. These vulnerabilities include issues related to Remote Code Execution (RCE), Local File Inclusion (LFI), and credential harvesting. The release of this version is a significant step towards strengthening the security of Apache Superset.
However, despite these remediations, there remains a considerable number of Internet-facing servers that are still affected by CVE-2023-27524, an authentication bypass issue. This report highlights the importance of addressing this issue promptly and taking necessary actions to secure Apache Superset instances.
II. Vulnerabilities and Fixes
The following vulnerabilities have been addressed in the Apache Superset 2.1.1 release:
III. Ongoing Concerns – CVE-2023-27524
Despite the availability of the 2.1.1 release and its associated fixes, there is a troubling issue regarding CVE-2023-27524, which allows for an authentication bypass. As per reports, over 2,000 Internet-facing servers remain vulnerable to this issue. An authentication bypass can provide attackers with unauthorized access to Apache Superset instances, potentially leading to further exploitation and data breaches.

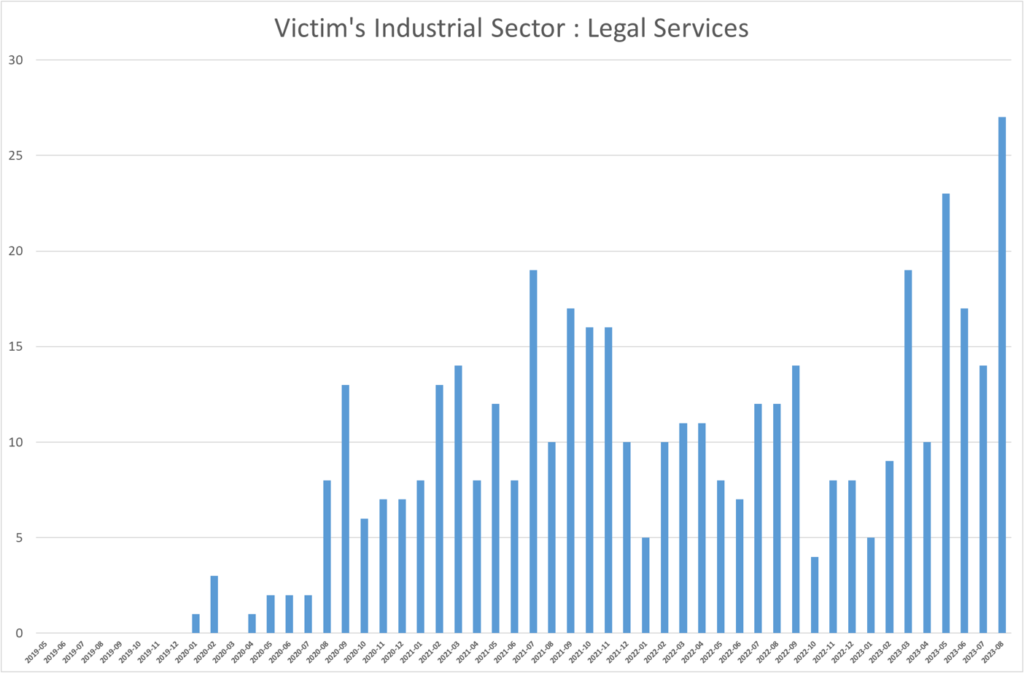
In recent years, the legal services sector, including law firms and associated organizations, has experienced a substantial increase in ransomware attacks, resulting in significant data breaches and financial losses. This trend has raised alarm within the industry, as it consistently suffers greater damage compared to other sectors. Furthermore, each passing year sees a higher degree of focus from ransomware gangs targeting legal services providers.
II. Ransomware Threat Landscape
The legal services sector is currently grappling with the following challenges related to ransomware attacks:
1. Increasing Targeted Attacks: Ransomware gangs are actively targeting legal services providers, recognizing the potential for high-value data and sensitive information. These attacks often lead to data encryption, financial extortion, and reputational damage.
2. Data Breaches: The compromise of sensitive client data, confidential legal documents, and financial records due to ransomware attacks poses a grave risk to both the affected organizations and their clients. Data breaches can result in legal liabilities, regulatory penalties, and severe reputational harm.
3. Financial Impact: Ransomware attacks have led to significant financial losses for legal services organizations. Not only do they incur costs associated with ransom payments, but also expenditures for incident response, system restoration, and legal counsel.
In recent cybersecurity research, several malicious URLs have been identified under the campaign name #404TDS. These URLs are linked to the distribution of the Lumma Stealer, a notorious malware strain known for its data theft capabilities. Additionally, the Command and Control (C2) server for the Lumma Stealer has been identified. This advisory report outlines the details of these findings and provides recommendations for mitigation.
II. Malicious URLs in the #404TDS Campaign
The following malicious URLs have been identified as part of the #404TDS campaign:
These URLs have been associated with the distribution of the Lumma Stealer malware.
III. Lumma Stealer and Associated Threats
The Lumma Stealer is a highly malicious data-stealing malware strain known for its capability to exfiltrate sensitive information from infected systems. In this case, the Lumma Stealer is being distributed through the aforementioned malicious URLs.
IV. Command and Control (C2) Server
The C2 server used to communicate with the Lumma Stealer has been identified as http://gapi-node[.]io/c2conf. This server plays a crucial role in the control and coordination of infected systems.
In September 2023, a highly sophisticated phishing campaign named “Lumma” has been identified, specifically designed to target hotels and their reservation systems. This campaign employs advanced tactics and techniques, including password-protected email attachments, malicious payload downloads, and process injection, to compromise the security of hotel reservation systems.
Phishing Campaign Overview
6. Execution of Malicious File: Simultaneously, a malicious file named “filex.exe” is executed, carrying out the primary objective of the campaign.
7. Injection with MSBuild.exe: The campaign further utilizes “MSBuild.exe” to inject malicious code into legitimate processes, making detection and mitigation more challenging.
In January 2021, Google’s Threat Analysis Group (TAG) publicly disclosed a campaign attributed to government-backed actors in North Korea. These actors employed zero-day exploits to target security researchers engaged in vulnerability research and development. Over the past two and a half years, TAG has continuously monitored and disrupted campaigns by these actors, discovering zero-day vulnerabilities and protecting online users. Recently, TAG identified a new campaign that shares similarities with previous ones, and it is highly likely to be the work of the same actors. TAG is aware of at least one actively exploited zero-day vulnerability used against security researchers in recent weeks. The affected vendor has been notified, and a patch is in the process of being developed.
This advisory report aims to raise awareness among the security research community about the ongoing threat and encourage vigilance in security practices.
II. Security Researcher Targeting
Similar to the previously reported campaign, North Korean threat actors have used social media platforms like Twitter (now X) to establish contact with their targets. They engage in lengthy conversations to build rapport with security researchers, often seeking collaboration on topics of mutual interest. After initial contact via X, communication is shifted to encrypted messaging apps such as Signal, WhatsApp, or Wire. Once trust is established, the threat actors send malicious files containing one or more zero-day vulnerabilities within popular software packages.
Upon successful exploitation, the malicious code conducts anti-virtual machine checks and sends collected information, including a screenshot, to an attacker-controlled command and control domain.
The shellcode utilized in this exploit shares similarities with that observed in previous North Korean attacks.
The affected vendor has been informed about the vulnerability, and a patch is in development. Detailed technical analysis of the exploits will be released in line with disclosure policies once the patch is available.
III. Potential Secondary Infection Vector
In addition to targeting researchers with zero-day exploits, the threat actors have created a standalone Windows tool named “GetSymbol.” The tool’s ostensible purpose is to download debugging symbols from symbol servers maintained by Microsoft, Google, Mozilla, and Citrix, primarily for reverse engineering purposes. While this tool can indeed serve a legitimate function, it also possesses the capability to download and execute arbitrary code from an attacker-controlled domain.
The source code for “GetSymbol” was first published on GitHub on September 30, 2022, with subsequent updates. If you have downloaded or executed this tool, TAG recommends taking precautionary measures to ensure the system’s cleanliness, potentially requiring an operating system reinstallation.
V. Actor-Controlled Sites and Accounts
GetSymbol:
Command and Control (C2) IPs/Domains:
Actor-Controlled Accounts:
The Ethereum address “0x88522a43427c96f9773ca110fe9373be6bbc5cc1” has been associated with various phishing events. These events involve fraudulent attempts to deceive individuals into disclosing sensitive information, such as private keys or login credentials, with the aim of stealing cryptocurrency assets or compromising user accounts.
Given the concerning nature of this Ethereum address’s activities, we recommend the following actions to mitigate the risk associated with it:
CVE-2023-33246 is a severe vulnerability affecting Apache RocketMQ. This vulnerability allows remote and unauthenticated attackers to manipulate the RocketMQ broker configuration, ultimately leading to command injection and potential code execution on the affected systems. Notably, this vulnerability has been actively exploited by threat actors since June 2023.
Vulnerability Exploitation
The exploitation of CVE-2023-33246 occurs through a custom remoting protocol that targets RocketMQ broker ports, typically on ports 10909 and 10911. It is crucial to highlight that widely-used scanning tools like Shodan and Censys do not specifically detect this protocol, making it challenging to assess the full extent of vulnerable systems in the wild.
While using Censys, we were able to identify approximately 4,500 potentially affected systems by searching for hosts exposing tcp/9876 (RocketMQ nameserver) in conjunction with one of the default broker ports (tcp/10909 and tcp/10911). However, it is important to note that a concentration of these systems in a single country raises concerns about the possibility of some being honeypots.
Payload Exposure
The RocketMQ broker was originally designed to operate within secure networks and was never intended to be exposed to the internet. Its inherently insecure interface includes various administrative functions, including updating the broker configuration and downloading it without authentication.
When an attacker updates the broker configuration with a malicious “rocketmqHome” variable, the payload is not executed immediately. Instead, the payload is written into the configuration file. After a brief delay, a process parses the configuration, executing a shell command containing the malicious variable, thereby resulting in the execution of attacker code. Importantly, unless overwritten, the attacker’s payload persists in the configuration indefinitely.
The lack of proper security awareness regarding the underlying protocol carrying the payload is evident in some public exploits, which involve sending hexadecimal blobs to victims.
https://vulncheck.com/blog/rocketmq-exploit-payloads
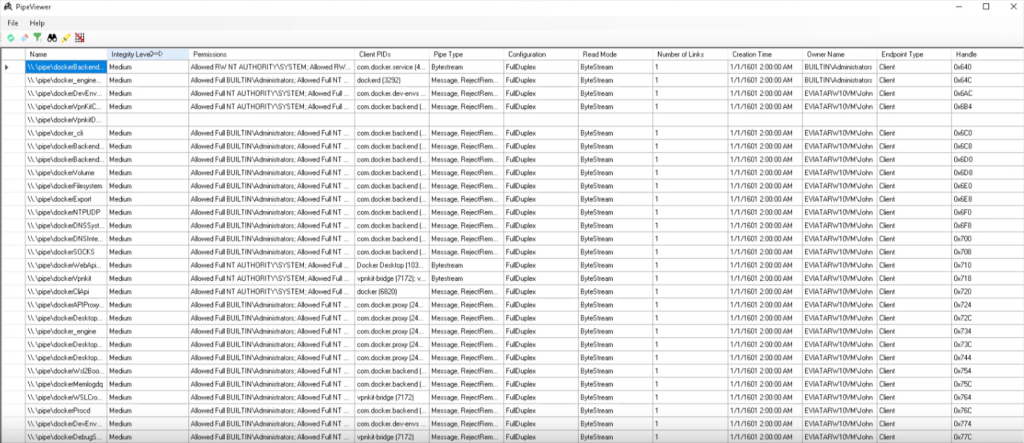
CyberArk has recently published a blog post titled “Breaking Docker Named Pipes Systematically – Docker Desktop Privilege Escalation (Part 1)” and released a complementary tool called PipeViewer. These resources are valuable for the security community, as they shed light on potential privilege escalation vulnerabilities in Docker for Windows and provide a tool for analyzing named pipes and their permissions.
Docker for Windows Privilege Escalation
The blog post by CyberArk delves into the findings related to Docker for Windows and highlights the discovery of a potential Local Privilege Escalation (LPE) vulnerability. This vulnerability, if successfully exploited, could allow an attacker to escalate their privileges on a Windows system where Docker for Windows is installed. The blog post outlines the methodology used to identify and systematically exploit this vulnerability.
Security professionals, particularly those involved in red teaming and penetration testing, should take note of this discovery, as it provides insights into potential attack vectors and the importance of securing Docker for Windows installations.
PipeViewer Tool
CyberArk has also released PipeViewer, a tool designed to assist security professionals in analyzing named pipes and their permissions. Named pipes are a crucial component of Windows interprocess communication and can be leveraged by attackers for various purposes, including privilege escalation. PipeViewer simplifies the process of inspecting named pipes and their associated permissions, making it an invaluable resource for security assessments.
https://github.com/cyberark/PipeViewer

@golem recently highlighted a blog post that discusses how the FlipperZero device can flood iPhones with BLE Advertisements that imitate Apple devices. This activity raises several security concerns, as it showcases the ease with which BLE Advertisements can be used to impersonate devices and potentially disrupt normal device operations.
II. BLE Advertisements and Device Impersonation
Bluetooth Low Energy (BLE) Advertisements are a fundamental part of the BLE protocol and are used for device discovery and communication. BLE Advertisements can carry information about the device, including its name, services offered, and more. Unfortunately, this feature can also be exploited to impersonate other devices, potentially causing confusion and security issues.
In this instance, @golem demonstrated how the FlipperZero device, and potentially other similar devices, can generate BLE Advertisements that mimic Apple devices. This impersonation can mislead nearby devices into believing that they are in proximity to legitimate Apple devices when, in fact, they are not.
The security implications of this activity are multi-fold: